Vulnerability testing specialists report that, over the most recent days, thousands of cases of infection have been detected by a dangerous new ransomware variant that compromises web servers and encrypts stored files.
This ransomware variant, dubbed as Lilocked or Lilu, has been active for just over a month, but its most important activity period includes the last two weeks, as mentioned.
About a month ago, some victims of this
ransomware began uploading screenshots of the ransom note sent by Lilu operators
on the platform ID Ransomware, a website that, based on screenshots and samples
of the encrypted files, allows users to identify the malware variants used to
infect a system. “Apparently this ransomware variant only infects Linux-based
systems, at least that’s what the evidence collected so far suggests,”
vulnerability testing specialists mention.
However, this time the Ransomware ID database
only managed to confirm that both the method of attack against compromised
servers and the encryption used by Lilu are never seen before techniques.
On the other hand, a forum frequented by
vulnerability testing experts has mentioned that Lilu operators are likely to
attack systems running non supported Exim software. However, experts have not
found the way this malware gets root access to servers.
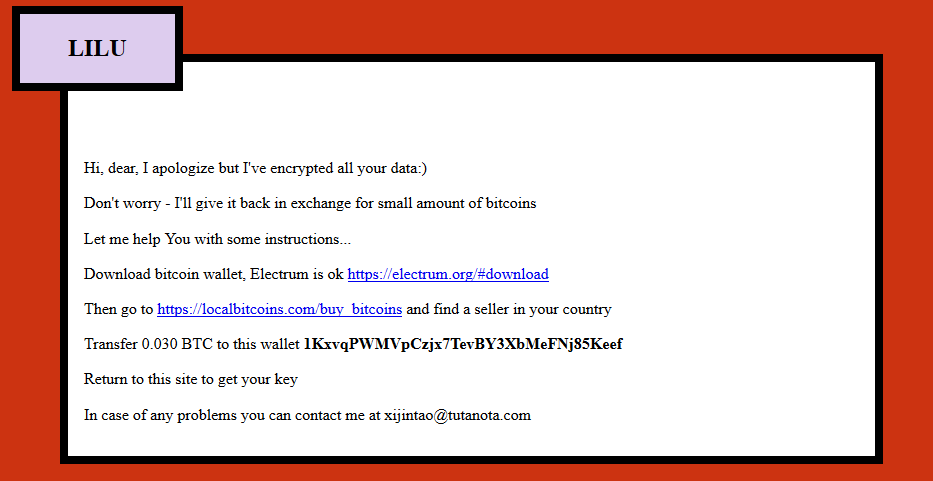
Although it is a new variant of ransomware, it
is very easy to identify a Lilu infection, as the malware encrypts almost all
files on the compromised server, subsequently adding the .lilocked extension to
the encrypted files. Finally, the ransom note is shown to the victim; in
addition, the hackers include a copy of that note in each folder that stores
some encrypted document.
The malware includes a feature to redirect the
victim to a portal hosted on dark web, where they will find complete
instructions to pay the ransom. Attackers usually demand a payment of 0.03
Bitcoin (about $350 USD depending on the current exchange rate) from each
victim.
Researchers note that the Lilu ransomware does
not fully compromise the activities of the infected server, as it does not
encrypt system files and only refers against a group of extensions like HTML,
JS, PHP, in addition to some content formats multimedia.
According to vulnerability testing specialists
at the International Institute of Cyber Security (IICS), this ransomware has
already infected at least 6,500 servers, many of which are indexed to popular
search engines. Although some details are already known about this new malware
variant, the number of victims could grow in a significant way.