Malware samples used in the recent attacks against several Polish banks contained planted evidence that attempted to blame the attacks on Russian-speaking hackers.
These false flags, as the (IT and real-world) security community refers to these planted clues, were discovered by Sergei Shevchenko, a Russian-speaking security expert for BAE Systems.
In a report published this morning, the researcher reveals that the malware used in those attacks contained a lot of mangled Russian words that no native speaker would have ever used.
His investigation revealed that the malware’s real operators used online services, such as Google Translate, to translate the words from English to Russian.
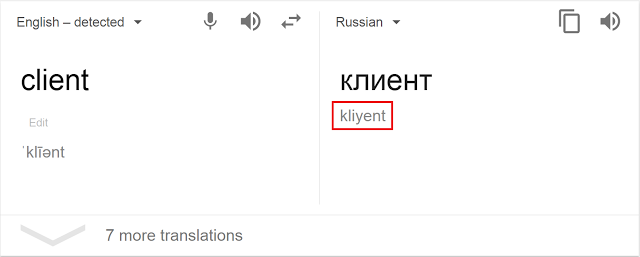
Shevchenko says the person who translated the words had no experience in dealing with the Russian language and was fooled by the phonetic spelling shown underneath the translated text.
The hacker thought he was copy-pasting the Latin spelling of the Russian word, but he actually copy-pasted the word’s phonetic spelling instead.
Hackers used lots of nonsensical words
For example, when he attempted to translate the English word “client” to Russian, he copy-pasted the “kliyent” phonetic spelling, not knowing that the correct spelling of the Russian word “клиент” was “client” or “klient,” but never “kliyent.”
This word was just one of the many the researcher found used in the wrong context, such as using the Russian word for “farm animals” after the attacker attempted to translate the English word “beast,” or using verbs in the wrong tense.
Other examples include the usage of the Russian word for “kettle” or “stupid person” when attempting to translated “dummy” in the context of dummy data or placeholder.
The researcher found these false flags in the malware deployed on infected hosts, but also inside a custom built exploit kit that was used to deploy malware binaries to victims via drive-by downloads.
In-depth analysis of this exploit kit and the malware that infected Polish banks can be found on the websites of BAE Systems, Symantec, and ESET.
Malware linked to attacks against banks in Mexico and Uruguay
All three security firms said that before targeting Polish banks, the same malware was used against banks and some private companies located in Mexico and Uruguay, towards the end of 2016.
Before Shevchenko found the false flags, all three companies said the Polish bank malware shares similarities with the malware used by Lazarus, a cybercrime group previously tied to attacks that took advantage of the SWIFT banking system [1, 2], and the high-profile attacks against the Sony movie studios.
A consortium of 13 security firms has published a report on the activities of the Lazarus group, who also attacked the governments of South Korea and the US. Many believe this group to be operating out of North Korea.
Polish bank malware linked to Sony hackers
According to ESET, the malware used in the recent attacks on Polish, Uruguay, and Mexican banks uses the same dynamic API loading techniques observed in previous Lazarus group malware.
Similarly, Symantec researchers discovered that the malware also used the same code strings, while BAE Systems researchers noted that the recent malware samples were also protected by the same Enigma Protector code packing system, and also shared the same “dropping” techniques.
All in all, putting together all these common techniques, and all the false flags that attempted to blame the attacks on Russian-speaking hackers, the recent attacks on Polish banks appear to be the work of a well-versed group with a history of attacks against financial institutions and with links to North Korea, rather than Russia.
Of course, this doesn’t mean that Russian hackers are innocent, but they don’t appear to be behind these attacks, based on the currently available information.