Fraudsters continue to innovate their scam propagation methods. Again using Facebook and a pretense of a shocking video, they also utilize browser plugins to execute malicious scripts. We also see how the malware scene is intertwined, when the user is directed to a dubious Potentially Unwanted Application. Facebook auto-like scams have been commonplace on the
Fraudsters continue to innovate their scam propagation methods. Again using Facebook and a pretense of a shocking video, they also utilize browser plugins to execute malicious scripts. We also see how the malware scene is intertwined, when the user is directed to a dubious Potentially Unwanted Application.
Facebook auto-like scams have been commonplace on the world’s largest social network for some time now. Typical techniques that the “likejacking” fraudsters use include overlaying pictures, invisible ‘Like’ buttons, and so on. Such tricks could be used for various nefarious purposes including malware distribution – a few examples of malware spreading through Facebook (albeit not always through likejacking) included Koobface, Boonana, Win32/Delf.QCZ, Yimfoca, to name just a few.
The scam described below does not, at the time of this writing, lead to the download of a malicious Windows executable, but appears to use the viral spreading campaign to promote a cheesy porn site and probably to monetize the web traffic in accordance with a Pay-per-Click model. Let’s look at the details that make this case interesting.
Figure 1
Not the Da Vinci Codec
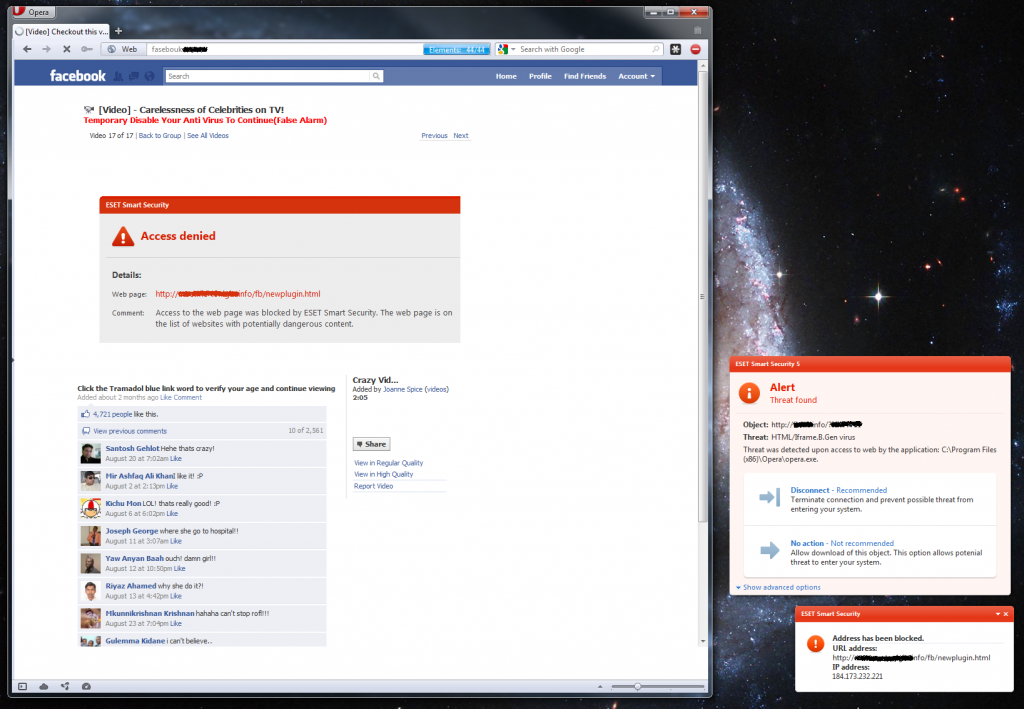
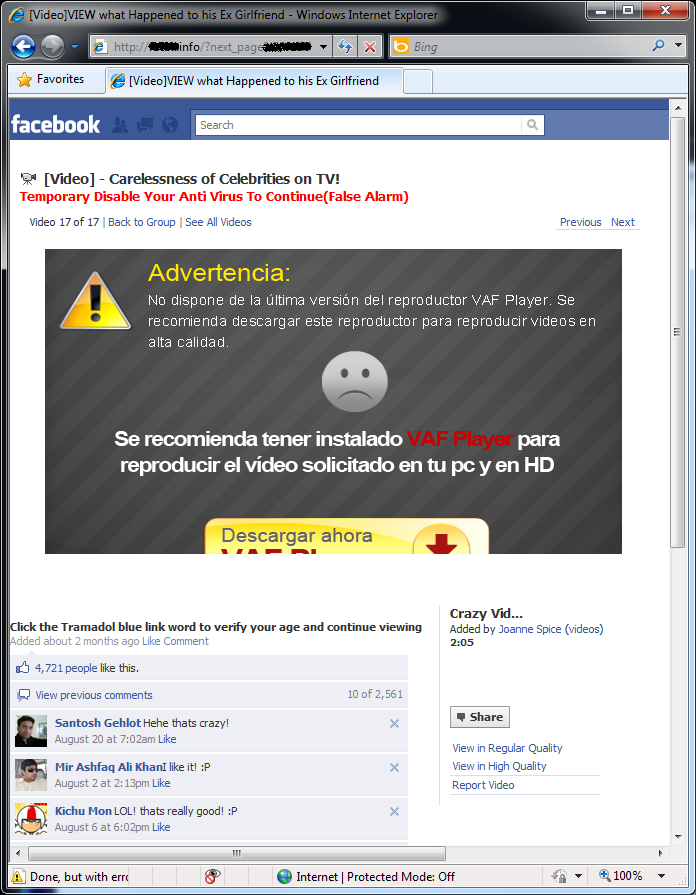
By now, the fake codec / media player trick is already getting a bit old hat, but it’s a little bit different as implemented here. The typical scenario would be “In order to view this great/shocking/hot video, you must first download the latest version of Flash player” and – as is common practice with trojan horses – the binary downloaded and executed (by the duped user himself!) infects the victim’s computer. In this version, the first part of the scam still applies – we have a fake Facebook-looking website featuring a video of “Carelessness of Celebrities on TV”. The first interesting point is the tip that the user should disable their antivirus, and that any detection of the binary as malicious is a false positive.
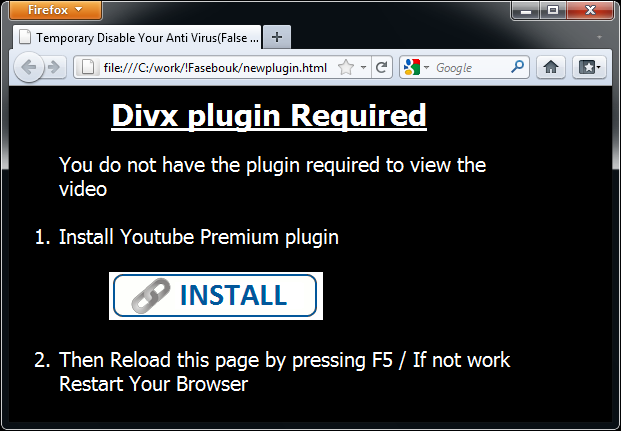
Secondly, as can also be seen from the above screenshot, what’s being blocked by our web filter is not an executable, but an HTML page. This is what it would have looked like if it had not been blocked:
Figure 2
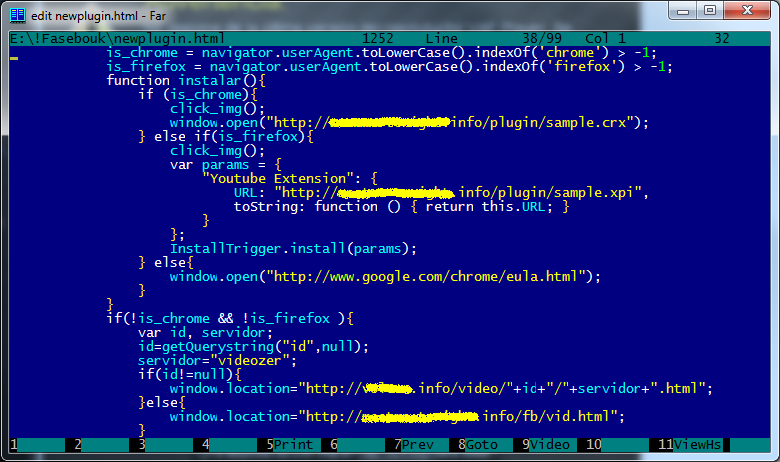
The victim is prompted to install a “Youtube Premium” plugin. The interesting part is that it really is a plugin! See the HTML source code below:
Figure 3
We can see that the script checks whether the user’s browser is Chrome or Firefox, and the corresponding plugin is then downloaded and installed.
Figure 4 Figure 5
Payload: the Code beneath
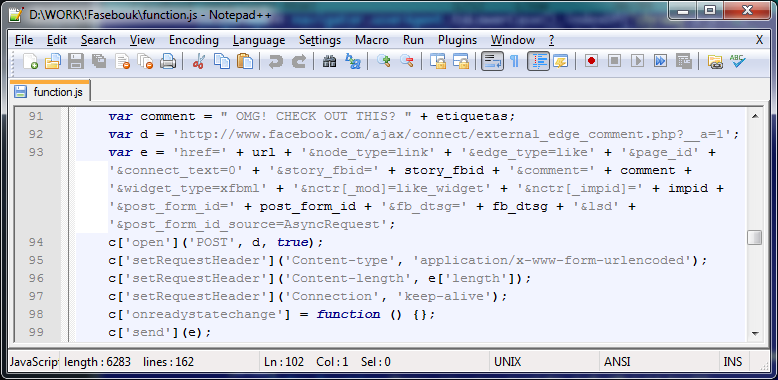
If we take a look into the plugin source code (they’re just ZIP archives that contain JavaScript code files inside – see here and here), and follow a chain of injected .js files (meaning that JavaScript injects JavaScript, which injects JavaScript, which injects JavaScript …) we finally get to the code responsible for posting the malicious links to the user’s Facebook wall. Below is an excerpt from the code (which also correctly includes the post_form_id and fb_dtsg variables which Facebook uses as a countermeasure against Cross-Site Request Forgery). This is actually an example of CSRF where the security of the browser is compromised by its trust in the user.
Figure 6
Here’s what happens when the script is executed:
Figure 7
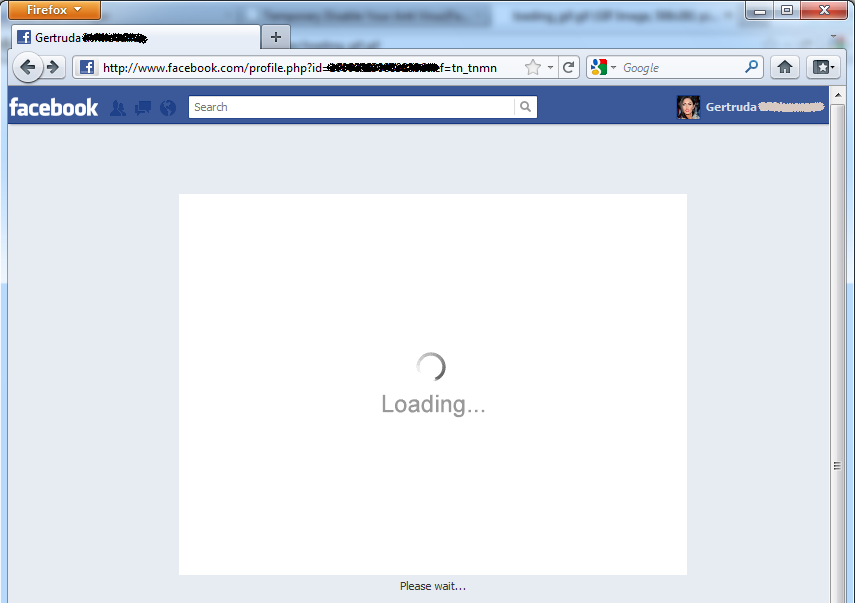
Following the “OMG! CHECK OUT THIS?” text you can see that the victim’s Facebook friends have been tagged in the post. This way, it will be shown on their Facebook walls as well (even though they haven’t themselves been infected…yet), because of the default setting for making Facebook wall posts visible:
Figure 8
This trick can lead to a very rapid outbreak.
Another payload, carried out by the JavaScript code in the malicious plugin, is a blatant redirection to the advertised porn site. This happens right after the infected user logs in to Facebook and is accompanied by an animated GIF, provided by the attackers:
Figure 9
Here’s a cropped and blurred screenshot of the promoted porn site:
Figure 10
Not a Chrome or Firefox user?
Don’t despair, the perpetrators have got something for you as well. As can be seen in the source code of newplugin.html (Figure 3), in case none of these two browsers is detected, the user is redirected to another URL. What we found there has really caught our attention:
Figure 11
It’s not the fact that some “player” is needed in order to view the video – that’s how traditional fake codec scams and malware work. But let’s see what happens if we give in and try this “VAF player” out.
Figure 12
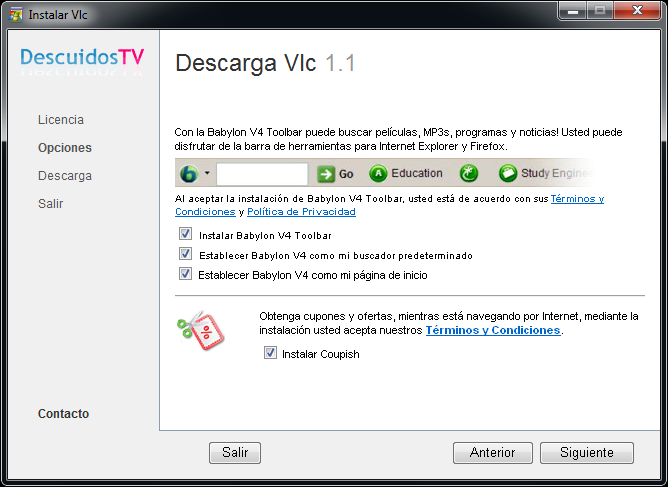
Parasites and PUAs
We are dealing with download software wrapper, which actually ends up downloading a legitimate copy of VLC player, but offers you the installation of a couple of “extras” on the way, namely a dubious toolbar and a “special offer deliverer” – ahh, yet again the topic of “Possibly Unwanted Applications rears its head J. We have mentioned this on the blog a few times already – here we can see examples of applications that are not malicious per se, but have distribution methods that are not exactly kosher. For more on the subject of dubious Potentially Unwanted Applications, refer to our Virus Bulletin presentation Fake but free and worth every cent (particularly, the section “A Parasite or Added Value?” refers to download wrappers such as this one) and Aryeh Goretsky’s whitepaper Problematic, Unloved and Argumentative: What is a potentially unwanted application (PUA)?
The ESET detection names that would show up in this case are HTML/Iframe.B for the generic detection of malicious HTML injections and JS/TrojanClicker.Agent.NCX for the specific malicious plugins.
Codec and Coda
One last note to finish off: As David Harley mentioned here, reports of similar scams to [email protected] are greatly appreciated. Thank you for helping us remove this garbage from the web.
Robert Lipovsky
Malware Researcher