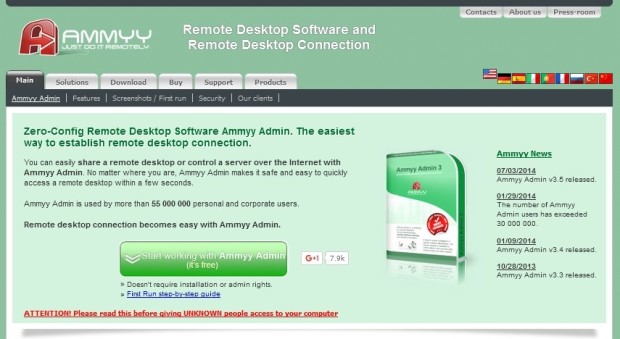
It may be a good idea to stay away from this software. The website of the Ammyy Admin remote desktop management utility has been abused over and over again by malware distributors to spread six different malware families in the past year.
The first signs that something was wrong came to light last November, when ESET discovered that, in the months of October and November 2015, crooks had compromised the website and infected the Ammyy Admin installer with five different malware variants, not all at a time, but at different intervals.
They first distributed the Lurk malware dropper, then the CoreBot infostealer, the Buhtrap banking trojan, the Ranbyus banking trojan, and the NetWire RAT.
ESET informed the website’s owners, who responded by saying they cleaned the website and removed the malicious versions of the Ammyy Admin installers that also contained malware.
Malware distribution operations resumed in February 2016
According to a new report released by Kaspersky today, the incident repeated in February 2016, when the company’s experts detected the same website spreading malware-laced installers once again.
This time around, the crooks used the Lurk trojan, a malware dropper that infects victims and then downloads other types of malware, at the crook’s behest.
Kaspersky informed the Ammyy Admin creators of their issues, and they said they fixed the compromised website. Kaspersky explained this happened three times in that month alone.
… and then in April and June
The scenario repeated in April, when the website was once again compromised. The crooks used the Lurk trojan again, but this time around, the trojan activated only if the infected computer was part of a corporate network.
Again, Kaspersky notified the website owners of their issue, who moved to clean the website, for the fourth time this year. Nevertheless, the same site kept getting compromised in the following months.
After Russian authorities had announced they had managed to arrest the hackers behind the Lurk trojan, on June 1, the very same day of the announcement, the Ammyy Admin website switched from distributing the Lurk trojan to the Fareit infostealer. Again, Kaspersky notified the Ammyy Admin creators of their issue.
At this point in time, seeing that the Ammyy Admin webmasters cannot secure their website even if their life depended on it, it may be a good idea to find an alternative to their software and stay away from their website.
Source:http://news.softpedia.com/