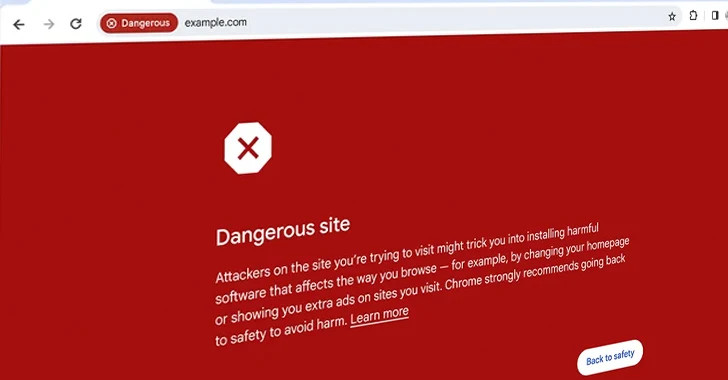
Google will ban logins from embedded browser frameworks, starting June 2019. The reason is the increased risk of phishing hacks using the man-in-the-middle attack. In this exploit, the conversation between the two parties is intercepted by a third unknown entity, who can change its content.
Users are most vulnerable to man-in-the-middle attacks when they login to their favorite apps via an embedded browser framework. A good example of an embedded browser is Chromium embedded framework, aka, CEF. It is used for logging in to Steam client, Evernote, and Amazon music.
Man-In-The-Middle Attack: How Will the ban help?
Currently, Google is unable to detect a MITM attack whenever you log in via an embedded browser. Thus, it treats a successful login and a compromised one in the same way.
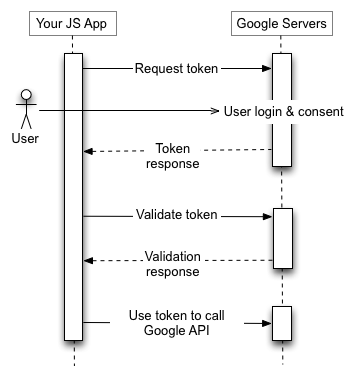
The solution to this is to ban logins via such embedded browsers and use OAuth authentication instead. In this process, the users will be taken to another browser, Safari, Chrome etc., whenever a login is requested. It’d easily allow Google to make sure that the login is not under attack. Furthermore, it’d also reveal the complete URL of the login page, thus giving the user more information.
In OAuth authentication, the three parties are involved: OAuth Client (the app you’re trying to login), OAuth provider (Facebook, Twitter, Instagram) and the owner themselves.
OAuth is a secure way to grant permission to OAuth clients to your data without the risk of exposing your password. It is a good move by Google because several users still don’t use 2 Factor Authentication.
Man-In-The-Middle Attacks On The Rise
This is not the only step taken by Google to prevent man-in-the-middle attacks. Recently Google updated its Gmail service with the MTA-STS standard, which is a huge step up from SMTP (Simple Mail Transfer Protocol). This update prevents hackers from accessing e-mails sent to and from Gmail.
The severity of the man-in-the-middle attacks can range from none to catastrophic. Stealing credentials via this attack is the most profitable in the financial sector. Only last month, IBM reported that hackers are collaborating to increase the intensity of their attacks. The latest example is the collaboration between Tikbot and Bokbot to install illegitimate Secure Socket Layer (SSL) certificate in their victim’s PCs.
Fake certificates can trick Anti-virus into thinking a malicious app as harmless, which can further cause massive damage.
In the meantime, it is advised to enable 2-Factor Authentication for all your social apps.