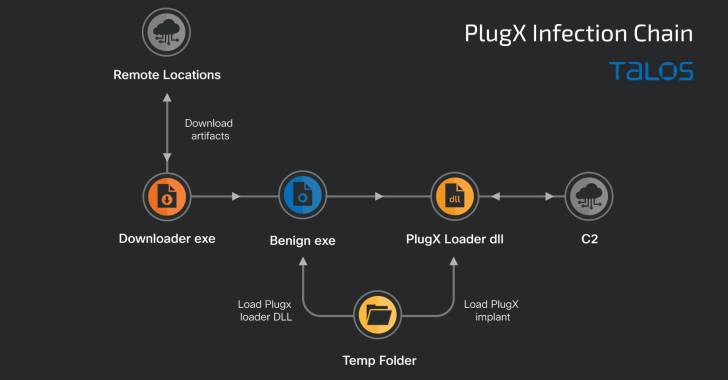
Researchers uncovered a new malware dropper called AndroMut from one of the infamous APT group TA505 to drop the FlawedAmmyy Remote Access Trojan gain the remote access from the infected victim’s computer.
TA505 hacking group believed to reside in Russia and the threat actors from this group involved in various high profile cyber attacks including infamous Dridex, Locky ransomware, ServHelper malware, FlawedAmmyy, delivered through malicious email campaigns.
FlawedAmmyy is a full-featured RAT that was first observed in early 2016, since then it was used by various cybercrime groups to attack thousands of victims around the world.
This campaign that observed by Proofpoint researchers through a spam email campaign that delivered Word or Excel file used macros to execute a Msiexec command.


Once the command is executed, Macro download and execute either the FlawedAmmyy loader or AndroMut.
Another campaign targeted recipients at financial institutions in Singapore, UAE, and the USA.
According to Proofpoint researchers, “AndroMut is a new downloader malware written in C++ that Proofpoint researchers began observing in the wild in June 2019. The “Andro” part of the name comes from some of the pieces which bear resemblance to another downloader malware known as Andromeda [1] and “Mut” is based off a mutex that the analyzed sample creates: “mutshellmy777”.”
Based on the malware observation, it resolves most of the Windows API calls at run time by hash and it using two ways to decrypt the strings.
In this case, The encrypted string is base64-decoded then decrypted with AES-256 in ECB mode.
Also, AndroMut using various anti-analysis technique and persistence technique to evade detection and make the analysis process hard to experts.
Researchers also observed some low-confidence overlaps between it and two other malware downloaders: Andromeda and QtLoader.
“Proofpoint researchers have observed TA505 and a number of other actors focus on downloaders, RATs, information stealers, and banking Trojans. The new AndroMut downloader, when combined with the FlawedAmmy RAT as its payload appears to be TA505’s new pet for the summer of 2019.”
Indicators of Compromise (IOCs)
| IOC | IOC Type |
| hxxp://greenthumbsup[.]jp/20.06.2019_746.38.doc | URL |
| hxxp://fakers[.]co[.]jp/20.06.2019_130.22.doc | URL |
| hxxp://nagomi-753[.]jp/20.06.2019_800.77.doc | URL |
| hxxp://nanepashemet[.]com/20.06.2019_781.37.xls | URL |
| 52f0aaff3654110e82586d21b07c8a3de23dc9efb3f4001daf412286282315c0 | SHA256 |
| d0aaf465a2569abbdcbafc049be1c1a643572f4ca185058833310435bfa53358 | SHA256 |
| eb3792fc83cd65823bc466e7253caf12064826b058230666d2ed51542ac59275 | SHA256 |
| f21039af47e7660bf8ef002dfcdb0c0f779210482ee1778ab7e7f51e8233e35c | SHA256 |
| 3e3eb26211459eb2d8b52a2429a52e7e12d2145d7733823d7415663537a0b6ca | SHA256 |
| 8621fa54946096ed38aee5cbcc068c0620416a05c17328a527673e808847850d | SHA256 |
| c4963dcf6b32459740f6a3d3b4d06d9dc06f15087ca01775956df36206543301 | SHA256 |
| a905838db6e6617edd9d25baaaaee9c209381d456e809081977e27c3e0b15793 | SHA256 |
| 59af9102a921130fd1d120f6cee7fc7cdfc28292a7a4a8c24233126604aa9443 | SHA256 |
| 98b584b31457b21d0d48fcc78093439638e15dd1705e54182d9aa4ffad014c3a | SHA256 |
| bb5054f0ec4e6980f65fb9329a0b5acec1ed936053c3ef0938b5fa02a9daf7ee | SHA256 |
| hxxp://kreewalk[.com:80/viewforum.php | URL |
| 5eddc55c0c445baf2752d56229fa384b7e3f1c7e76b22f43e389c6a711aa713a | SHA256 |