Another day, another trove of medical records leaked online, thanks to a misconfigured AWS S3 bucket.
Medical records are considered to be sensitive documents and when a malicious third party has access to them it is a bad news as these records can be used for fraud, blackmailing and marketing purposes against patients’ will. However, recently, IT security researchers at cyber resilience firm Upguard discovered a massive trove of highly sensitive data that was available for public access.
According to Upguard’s blog post, the data belonged to Medcall Healthcare Advisors (CSTAR score: 342), a “Workers Compensation and Healthcare Solutions” provider and the reason for it to be exposed was a misconfigured Amazon Web Service (AWS) bucket.
Those who are following HackRead, probably know that misconfigured AWS buckets are the major cause of data leaks for the last couple of years and so far major firms like AOL, GoDaddy, LocalBox, Tesla, GM, Toyota, Pentagon, NSA, US Military, Viacom and Verizon. etc, have become victims of it.
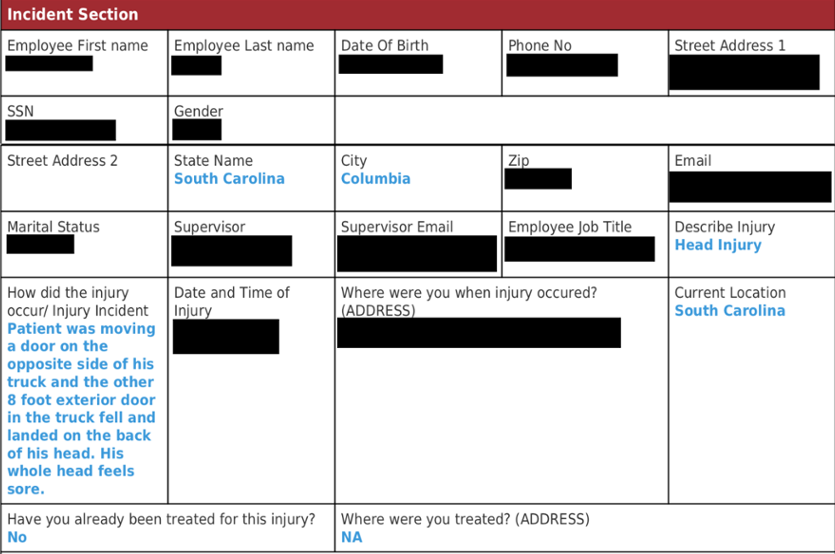
As for the latest breach; the exposed data contained 7 gigabytes of files including medical records, injury forms for 181 different business locations across the United States with personally identifiable information (PII), descriptions of injury and sickness, details about the patient’s employment and employer, 715 files of phone call recording between patients, doctors and Medcall operators and Social Security Numbers of around 3,000 individuals.
The data was discovered on August 24th, and most of the affected companies were transportation businesses, while the others are comprised of a variety of different industries, including local government entities like county boards and school districts, and individual locations of large franchise chains, like Piggly Wiggly, KFC, and Hampton Inn.”
Although the number of affected individuals is not big, the Upguard’s team determined that the breach was “extremely sensitive.”
“The PII present in the Medcall data is more than enough for the individuals within to have had their identities stolen, if a malicious actor were to have accessed it. The medical details reveal an even more private world, that of individuals dealing with their own bodies, and the specialists who help with them,” concluded Upguard.
If you are using an AWS bucket make sure it is not secured and not misconfigured for public access. To protect your AWS bucket follow this guide with screenshots.