On 7th Match 2017, the whistle-blowing organization Wikileaks published a series of new documents code-named “Vault 7” allegedly belonging to the U.S. Central Intelligence Agency (CIA). These documents not only revealed the existence of a large-scale cyber espionage campaign but also show how the agency used zero days security flaws in Windows, macOS, Linux, iPhones, Android devices, several other high-profile software and utilities including Notepad and video player VLC (“VideoLAN”).
Now, VLC has issued an official statement on the matter while Notepad++ has released patches since its name was on the list of hacking tools used by the CIA to target unsuspecting Windows users.
Notepad++ statement:
In their official blog post Notepad++ said that:
The issue of a hijacked DLL concerns scilexer.dll (needed by Notepad++) on a compromised PC, which is replaced by a modified scilexer.dll built by the CIA. When Notepad++ is launched, the modified scilexer.dll is loaded instead of the original one.
It doesn’t mean that CIA is interested in your coding skill or your sex message content in Notepad++, but rather it prevents raising any red flags while the DLL does data collection in the background.
It’s not a vulnerability/security issue in Notepad++, but for remedying this issue, from this release (v7.3.3) forward, notepad++.exe checks the certificate validation in scilexer.dll before loading it. If the certificate is missing or invalid, then it just won’t be loaded, and Notepad++ will fail to launch.
Checking the certificate of DLL makes it harder to hack. Note that once users’ PCs are compromised, the hackers can do anything on the PCs. This solution only prevents from Notepad++ loading a CIA homemade DLL. It doesn’t prevent your original notepad++.exe from being replaced by modified notepad++.exe while the CIA is controlling your PC.
Just like knowing the lock is useless for people who are willing to go into my house, I still shut the door and lock it every morning when I leave home. We are in a f**king corrupted world, unfortunately.
Otherwise, there are a lot of enhancements and bug fixes which improve your Notepad++ experience. For all the detail change log, please check on the Download page.”
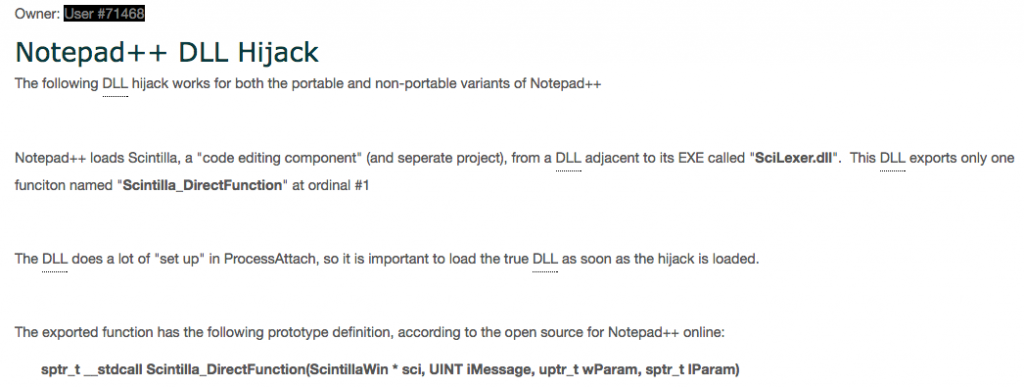
Screenshot from Vault 7 leaks about Notepad ++ / Source: Wikileaks
Notepad users are advised to download its latest 7.3.3 version from here and also report any bug they find on Notepad++ forum.
VideoLAN’s statement:
One of the leaked Vault7 documents revealed that CIA is using fake VLC players to steal data from an infected device. The document further revealed that CIA agents used a tool to exploit a modified old version of VLC media player. The described tool gathers documents from a computer or network and, to hide its activity, runs inside VLC Portable 2.1.5 on Microsoft Windows platforms. Such modified software provides a legitimate appearance (plays media files) while scanning the computer or the network for its intelligence purpose.
In their official statement [Pdf], the developers of VLC player VideoLAN said that the company is taking the revelation seriously. However, it must be noted that this is not an actual vulnerability in VLC but a result of downloading the set up from untrusted sources.
VideoLAN further explains that:
The technique used is a modification of the software’s manifest to force the loading of a fake dynamic library “psapi.dll,” instead of using the official Windows version. This DLL contains the malware’s executable code. The attack described in the leaked document requires • physical access to the targeted computer, • Microsoft Windows XP or later host system, • and execution of the tool allegedly developed by the CIA (provided on “thumb drive”, but not exclusively).
[…]
We would like to bring to your attention that this exploit is nothing different than installing a trojaned software from an untrusted source. The only safe source for getting VLC media player is the official VideoLAN website. Security of our users’ data is of prime importance. As a consequence, we have taken countermeasures to prevent malware from hiding their activity behind VLC media player.
The used attack vector modification will not be possible starting from the next minor release, 2.2.5. We are also working on hardening the VLC security for the next major releases (3.x.x).
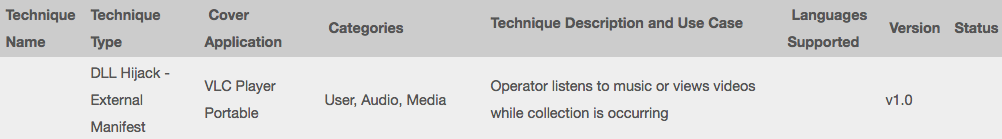
Screenshot from Vault 7 leaks about VLC player / Source: Wikileaks
If you are using VLC player make sure you have its updated version and if you plan to download its setup do that from VideoLan’s official website.








