A security researcher has published the proof-of-concept code which demonstrates how to create a fully functional Facebook worm.
It’s a clickjack bomb that can spam your wall by exploiting a vulnerability on Facebook. The researcher, who works under the pseudonym of Lasq, says he has seen this flaw getting abused on the platform by a Facebook spammer group.
According to Lasq, the clickjacking vulnerability exists in this mobile version of Facebook sharing dialog (popup), but the desktop version remains unaffected.
He noticed that many of his Facebook friends had posted a link to French comic site hosted on an Amazon Web Services (AWS) bucket.
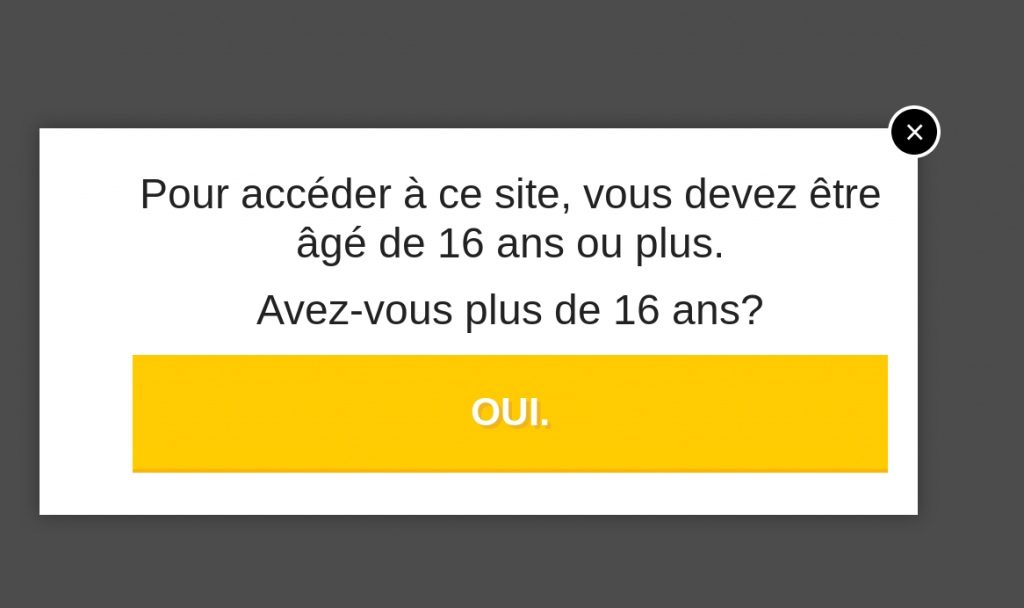
On clicking the link, users were asked in French to verify their age and redirected to page with comics and ads. But the same link was posted on a user’s Facebook wall after they clicked on it.
So Lasq dug around a bit and found that the spammers were using codes to exploit the IFrame element of Facebook’s mobile sharing dialog.
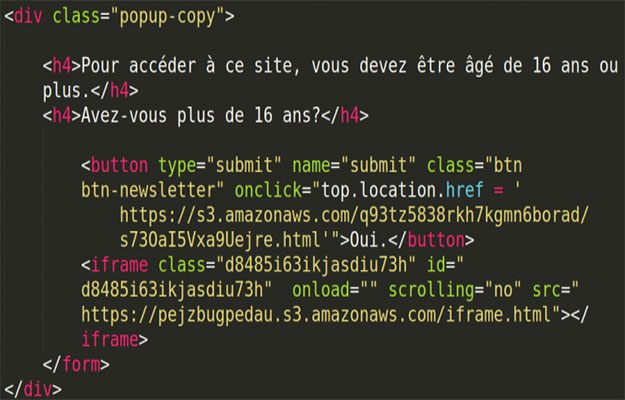
An “IFrame” also known as “inline frame” is simply an HTML document embedded inside another HTML document. IFrames are commonly used to directly insert content from one source into another.
However, Facebook had ignored the X-Frame-Options header for the mobile sharing dialog.
An X-Frame-Options header is used to decides whether a browser should be allowed to render a page. It is typically used to prevent code from being loaded inside IFrames and stop clickjacking.
Instead, Facebook allows mobile developers to open the share dialogue in an Iframe on top of the website. A pop-up confirmation is then supposed to ask whether the user wants to share the link — but it clearly didn’t happen in this case.
Maybe the “age verification” popup which appeared earlier, bypassed Facebook’s system.
Even though Lasq contacted Facebook, they refused to fix this issue. Facebook argued that clickjacking is an issue only when an attacker somehow changes the state of the account (e.g., disable security options, or remove the account).
On being contacted by ZDNet, Facebook simply stressed on the part that they are continuously improving their “clickjacking detection systems” to prevent spam.
But Lasq fears that the attacker can do more damage in the future: “This time it was only exploited to spread spam, but I can easily think of much more sophisticated usage of this technique.”