A group of Russian-speaking hackers has been attacking multiple governments for years now. Not only that, but they also experimented with different methods of conducting those attacks with the help of the social media websites. Their approach was pretty clever, and they used those sites for concealment of the espionage malware.
Antivirus provider called Eset has reported a backdoor Trojan that was discovered recently. Apparently, Eset’s researchers have discovered that the Trojan used Britney Spears’s Instagram account in order to find the control server that was receiving data and sending instructions to the devices infected with the Trojan.
This new approach, allegedly by the hacker group called Turla, has made malware attacks even harder to predict and discover, since the servers controlled by the group were never directly referenced by anyone.
Turla is a group of hackers who are known to be Russian-speakers infamous for their use of the newest and most modern espionage malware.
During 2014, Symantec’s researchers found and noted a malware named Wipbot. It was discovered that this malware was used for infection of Windows systems in multiple governments and embassies of several European countries. Many of these countries belonged to the Eastern Bloc.
Several months after the discovery, Kaspersky Lab’s researchers have uncovered a stealthy Linux allegedly used in the same campaign.
It’s also known that Turla has a capability of using the satellite-based Internet so that they could cover their tracks. On top of that, the group was also discovered to be using a zero-day Windows vulnerability back in March. Once again, they tried to infiltrate the computers of European militaries and governments.
Eset’s report also mentioned an extension in the Firefox browser that posed as a security feature. Of course, it was a fake and allowed a third party to take control over the infected device.
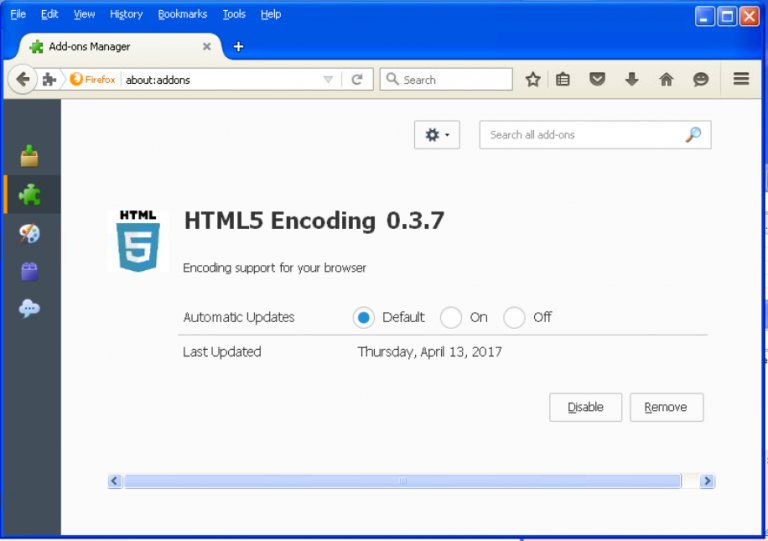
Firefox extension (Image Credit: WeLiveSecurity)
Researchers further explained the process and said that the extension uses a bit.ly URL to reach the C&C. However, the path can’t be discovered by the extension code and that it can only be detected by using comments found on Britney Spears‘s Instagram posts. The extension scans comments on each photo and then computes a custom hash value searching for the one that matches 183. It can then find a path to the URL.
There was only one comment that served this purpose and it was left on February 6, 2017, while the photo was posted earlier in January. The examination of the data from the URL has uncovered that the URL itself had 17 visits only in February. This means that the malware is still in its testing phase, or that it was used against highly targeted people.
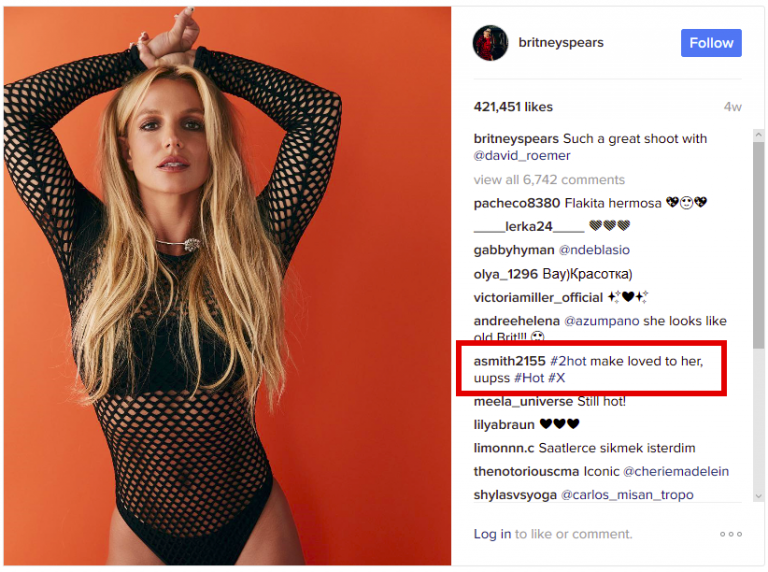
Screenshot of the picture where malware infected link was posted / Image Source: Instagram (https://www.instagram.com/p/BO8gU41A45g/)
The extension itself was spread by a certain security company that wasn’t named, but that’s known to be located in Switzerland. It’s even believed that the extension could, in fact, be an update to another one from an earlier campaign.
The backdoor in the newest extension has several abilities, including the execution of arbitrary files, downloads and uploads to C&C, as well as reading directory content. This includes sending file listings, and even its dates and sizes to the same C&C.
Eset also notes that the developers from Firefox are trying to patch up the browser so that this and similar extensions wouldn’t be able to operate anymore. It’s expected that the next version of this extension won’t look anything like its previous versions.