In today’s world, it is becoming difficult each day to keep your privacy safe. A new Sim card attack: Simjacker wants to make your life even more difficult by exploiting a vulnerability in mobile sim.
The Simjacker attack utilizes an inbuilt dynamic sim toolkit called the [email protected] browser. It is a legacy technology embedded in mobile SIM cards since 2009.
The Simjacker vulnerability is allowing hackers to execute Denial of Service (DoS) attack, leak your personal information, send misinformation using your contact number, etc.
What’s even worse is that reports claim that a private company is working closely with government agencies to spy on a billion users present in 30 countries worldwide with the help of the Sijmacker attack.
Almost all the users affected have no idea that their security has been compromised.
SIM card Attack: “Simjacker” — How Is It Executed?
Since the Simjacker flaw attacks the SIM irrespective of the smartphone brand. Thus, almost every manufacturer including Apple, Motorola, Samsung, Goole, Huawei, and ZTE has been affected by this vulnerability.
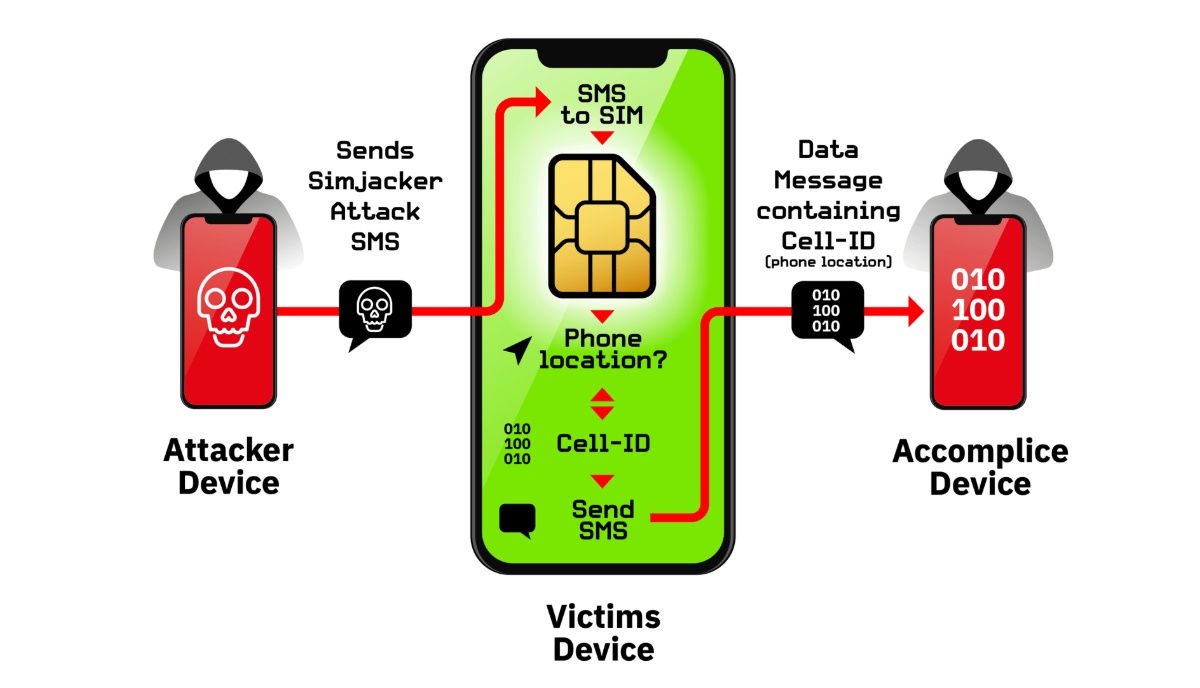
The main process of executing a Simjacker attack involves the following steps:
- An SMS containing a spyware code is sent into the phone’s message box.
- This message instructs the SIM to execute and retrieve sensitive information from the data.
Throughout this process, the owner of the phone is completely unaware that his information is being leaked or he is being spied on.
When a hacker successfully performs the Simjacker attack, they can force the user’s phone to open malicious software, steal their information, spread information using owners’ phones, etc.
This type of vulnerability can incite some serious violence in the era of fake news. Instances of riots and mob violence have been reported in several places in India due to fake messages on WhatsApp.
According to Cybersecurity researchers, the Simjacker vulnerability is also being evolved to perform new additional types of malicious hacks on the user’s phone.
People living in countries like America, Europe, Middle-east, West Africa have been affected the most. However, considering the scale of this attack, it is not wrong to assume that almost everyone in the world has been an unwilling victim of this attack for the past two years.
According to the report, the user carrying the defective SIM card is attacked 5 times on an average per week. At its worst, a single user is attacked almost 250 times per week using the Simjacker attack.
Adaptive Mobile Security, which identified the attack, said that they’re working closely with the mobile industry in stopping this attack. According to them, the Simjacker attack represents a massive increase in the “complexity” and “sophistication” of attacks over mobile core networks.
The security firm claims that the Simjacker was created by a private company in association with the government to spy on the users. There is no information on their names yet.
What Is Being Done To Stop Simjacker Attack?
Authorities representing the mobile networks industry including the GSM Association and the SIM alliance have been notified about the Simjacker attack.
The SIM alliance, a non-profit industry organization that works to make mobiles safe, has taken the necessary steps to halt push messages on mobile phones. These steps include stopping binary messages at the network level and also at the SIM card level.
There’s no solid way to tell whether you’ve been affected by the Simjacker attack. However, you can help avoid any potential future attacks by using a SIM card without the [email protected] dynamic sim tool kit.