Featured News
-

 286Android
286AndroidAndroid bug in most smartphones could let rogue apps run wild
Nearly all Android smartphones contain bugs which can allow rogue apps to ignore the Permissions used to control them, according to German...
-

 111Privacy
111PrivacyGoogle Glass wearers can steal passwords from 10ft away
A new computer vision attack could allow Google Glass wearers to steal passwords typed in on nearby tablet or smartphones - even...
-

 110Scams
110ScamsSilk Road Bitcoin auction bidders targeted in phishing scam
A leaked list of people who had enquired about the auction for bitcoins from the “dark market” Silk Road provided a target...
-

 367Cyber Crime
367Cyber CrimeWi‑Fi light bulbs in security alert over wireless blackout hack
A high-profile ‘connected’ lighting system had a critical vulnerability which allowed attackers to take control of the entire system, switching off light...
-

 179Privacy
179PrivacyFacebook may face FTC fines over research into users’ emotions
With EPIC filing an FTC privacy complaint against Facebook, which is already the subject of a Consent Order due to a previous...
-

 115Opinion
115OpinionSupport Scam: Old Racket Still in Service
One of the support scam sites used to mislead victims may be down, but the scam definitely isn’t about to go away.
-

 150Cyber Crime
150Cyber CrimeElite force of ‘cyber cops’ to be trained by Europol
Top police cybercrime experts from 22 European countries are to participate in a 10-day intensive training course in Spain starting this week...
-

 390Privacy
390PrivacyAndroid Wi‑Fi bug broadcasts where you’ve been
A feature in newer Android phones puts users' privacy at risk - effectively broadcasting an accurate location history over the air even...
-

 73Cyber Crime
73Cyber CrimeBrazilian payment malware may have skimmed up to $4 billion
Banking malware built to misdirect a Brazilian form of bank payment method targeted $3.75 billion of transactions over the past two years...
-

 165Password
165PasswordFidelys smartwatch: Could iris scans replace passwords?
A new smartwatch, Fidelys, aims to bring a new level of biometric security to our lives with an ultra-secure infrared iris-scanning camera...
-

 113Opinion
113OpinionCriminals target school data: top 10 security measures for educational institutions
Every educational institution should be aware that cyber criminals make money by stealing personal information and selling it on the black market...
-

 419Cyber Crime
419Cyber CrimeCredit card breach warning from point‑of‑sale terminal vendor
A point-of-sale and security system vendor used by restaurants including Taco Bell and Dairy Queen has warned its customers that customer credit...
-

 142Privacy
142PrivacyFacebook privacy policy in European probe
European privacy regulators have demanded an explanation from Facebook over its alleged “psychological experiment”, in which thousands of unknowing site users’ News...
-
 378News
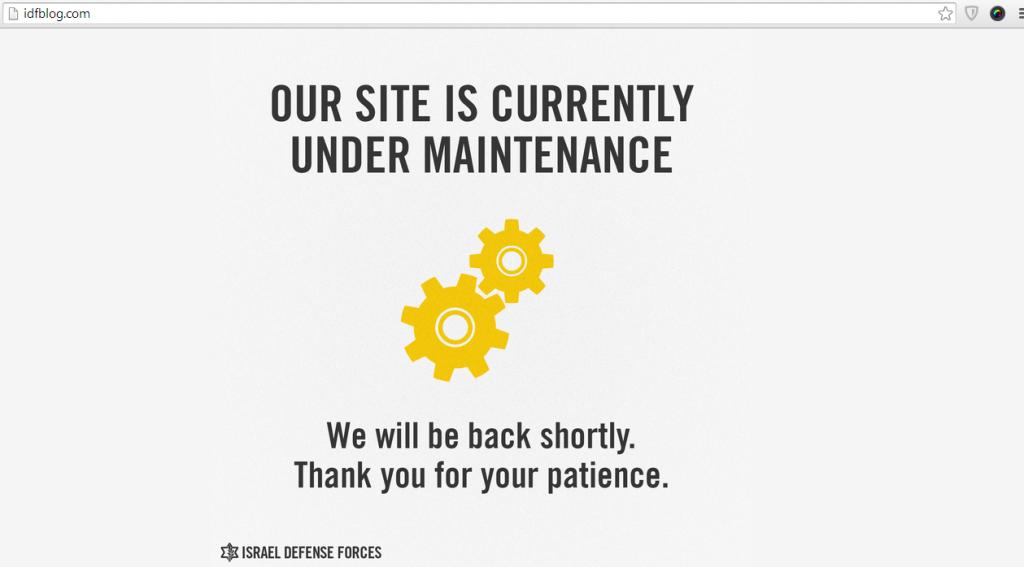
378NewsIsraeli Defense Forces official Blog Hacked by Syrian Electronic Army
Syrian Electronic Army has made a major comeback by hacking and defacing the official blog of Israel Defense Forces (IDF) yesterday. The high profile...
-

 148Scams
148ScamsiPhone 6 launch used as bait in scam emails
Eager Apple fans waiting for the latest update on the iPhone 6 launch and the rumored iWatch have been targeted with a...
-

 478Privacy
478PrivacyBlackphone ultra‑secure Android handset goes on sale
The Blackphone, a new super-secure Android handset is now on sale. The Blackphone offers encryption technology that makes snooping on calls or...
-

 137Cyber Crime
137Cyber CrimeKrebs heroin plotter arrested selling credit cards in Italy
A Ukrainian criminal who claimed to be behind a plot to send packages of heroin purchased from an online ‘dark market’ to...
-

 509Opinion
509OpinionChip & PIN & Signature, Magstripes and EMV Go‑Faster Stripes
The US is still perceived as a hotspot for card fraud: what difference will the ongoing roll-out of Chip & Signature EMV...
-

 80Cyber Crime
80Cyber CrimeBitcoin extortion letters threaten pizza restaurants
Extorted for Bitcoin? Some U.S. pizza restaurant owners have been receiving letters threatening them with bad reviews, fake pizza orders, food contamination...
-

 81Password
81PasswordA clever fix for Android L passwords issue
Handing out Wi-Fi passwords to Android L users just got easier, thanks to a secure NFC method of password sharing, meaning the...
The Latest
-
 Malware
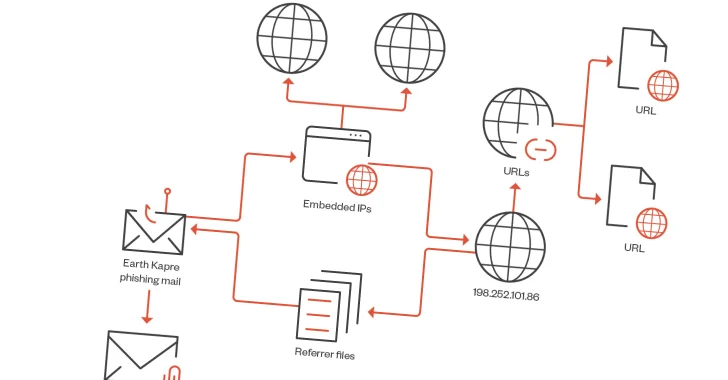
MalwareRussian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
-
 Vulnerabilities
VulnerabilitiesCritical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
-
 Vulnerabilities
VulnerabilitiesHackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
-
 Malware
MalwareTA558 Hackers Weaponize Images for Wide-Scale Malware Attacks
-
 Vulnerabilities
VulnerabilitiesAWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs
-
 Vulnerabilities
VulnerabilitiesWidely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
-
 Malware
MalwareHive RAT Creators and $3.5M Cryptojacking Mastermind Arrested in Global Crackdown
-
 Vulnerabilities
VulnerabilitiesIntel and Lenovo BMCs Contain Unpatched Lighttpd Server Flaw
-
 Vulnerabilities
VulnerabilitiesAI Copilot: Launching Innovation Rockets, But Beware of the Darkness Ahead
-
 Malware
MalwareChinese-Linked LightSpy iOS Spyware Targets South Asian iPhone Users
-
 Vulnerabilities
VulnerabilitiesPalo Alto Networks Releases Urgent Fixes for Exploited PAN-OS Vulnerability
-
 Cyber Attack
Cyber AttackU.S. Treasury Hamas Spokesperson for Cyber Influence Operations
-
 Cyber Attack
Cyber AttackHackers Deploy Python Backdoor in Palo Alto Zero-Day Attack
-
 Malware
MalwarePopular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files
-
 Malware
MalwareIranian MuddyWater Hackers Adopt New C2 Tool ‘DarkBeatC2’ in Latest Campaign
-
 Cyber Attack
Cyber AttackZero-Day Alert: Critical Palo Alto Networks PAN-OS Flaw Under Active Attack
-
 Malware
MalwareSneaky Credit Card Skimmer Disguised as Harmless Facebook Tracker
-
 Data Breach
Data BreachU.S. Federal Agencies Ordered to Hunt for Signs of Microsoft Breach and Mitigate Risks
-
 Malware
MalwareTA547 Phishing Attack Hits German Firms with Rhadamanthys Stealer
-
 Vulnerabilities
VulnerabilitiesPython’s PyPI Reveals Its Secrets