Featured News
-

 66Cyber Crime
66Cyber CrimeBanks to work with UK government experts to ‘predict’ cyber attacks
A new intelligence-sharing network aims to protect financial institutions by sharing information between government, security firms and financial institutions to “predict” vulnerabilities.
-

 107Privacy
107PrivacyFacial recognition camera used to convict robber for first time
In a world-first case, biometric facial recognition software has been used to convict an armed robber, with a Chicago robber “matched” from...
-

 347Opinion
347OpinionEncryption essential for cyber security: A million reasons to encrypt sensitive data
Encryption is essential to cyber security today, with encryption of personally identifiable information (PII) being a top priority for organizations large and...
-
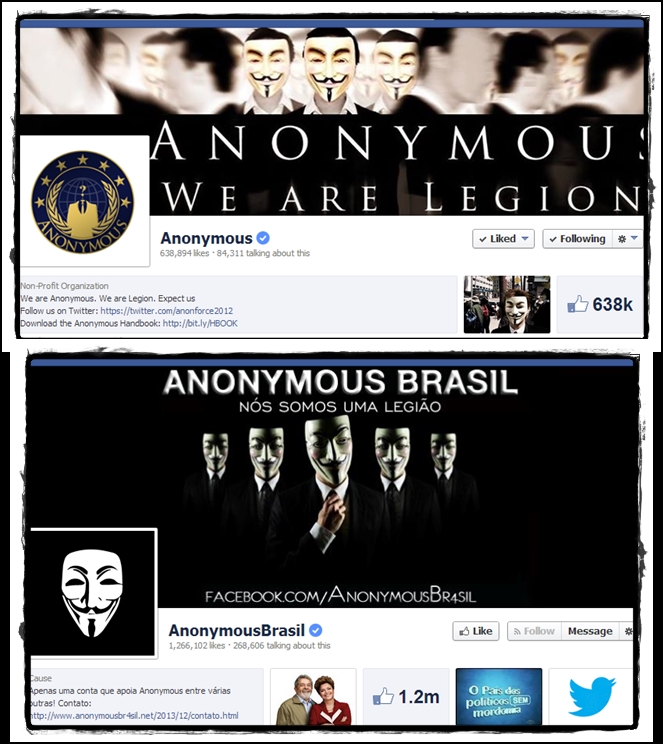
 195News
195NewsTwo Big Anonymous Hacktivist Pages on Facebook get Verified Badges
While surfing Facebook, you must have seen a blue badge indicating verified pages and profiles of famous people such as celebrities, journalists...
-

 253News
253NewsiOS 8 Safari Browser on iPhone and iPad Can Read Your Credit Card Details
Your iPad or iPhone’s camera has become immensely powerful after the emergence of iOS 8 Safari’s new version. Its most astounding feature...
-

 91Malware
91MalwareRansomware 101: FAQ for computer users and smartphone owners
Do you know what ransomware is? Do you know a filecoder from a lockscreen? Read our FAQ to become more clued-up about...
-

 83Password
83PasswordDrawing “signature” on screen could replace passwords, study finds
Even smartphone and tablet users who choose a four-digit PIN to protect their device are vulnerable to “shoulder surfers” glimpsing the code...
-

 99How To
99How ToAndroid malware: how to keep your device safe from filecoders (and everything else)
When ESET researchers analyzed the first Android ransomware controlled via Tor, it showed how quickly Android malware is evolving to match its...
-

 172Privacy
172PrivacyNSA faces fresh revelations as Snowden anniversary arrives
On the one year anniversary of Edward Snowden's public revelations of mass surveillance conducted by the U.S. National Security Agency we look...
-
 201Cyber Crime
201Cyber CrimeDARPA to hold $2m Grand Challenge for “fully automated” cyber defense systems
The hi-tech research wing of the US military DARPA (Defence Advanced Research Projects Agency) is to offer a $2 million prize offered...
-

 117Privacy
117PrivacyEngland footballers have their passport details leaked on Twitter
In an embarrassing breach of security, the passport numbers of members of the England Football squad have been accidentally tweeted out by...
-
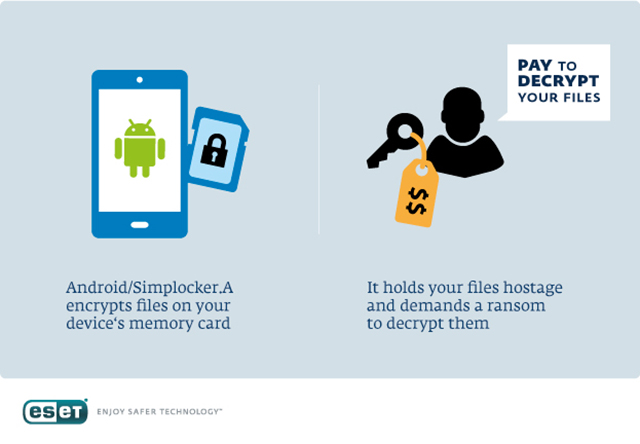
 415Malware
415MalwareESET Analyzes Simplocker – First Android File‑Encrypting, TOR‑enabled Ransomware
Last weekend saw the (somewhat anticipated) discovery of an interesting mobile trojan – the first spotting of a file-encrypting ransomware for Android...
-
 87Malware
87MalwareWindows XP users slow to upgrade despite risks
Users of Windows XP are not upgrading to safer versions of the operating system after the April 8 deadline when Microsoft stopped...
-

 142Scams
142ScamsPhishers turn to Dropbox links as fresh bait for victims
Convincing-looking emails where the victim is directed to click on a Dropbox link to download a supposedly unpaid invoice (and other classic...
-

 304Data Security
304Data SecurityHeartbleed now reforms into “Cupid” attack targeting Wi-Fi networks and Android
If you thought that Heartbleed is out of date now, and the whole cyber world is secure, then you have to change...
-

 207Cyber Crime
207Cyber CrimeGameOver Zeus and Cryptolocker: Law enforcement hits gang responsible
FBI names as "Most Wanted" the leader of cyber criminal gang based in Russia and Ukraine responsible for both GameOver Zeus and...
-

 210Surveillance
210SurveillanceScarface Writer Oliver Stone to Make Film on Snowden’s Whistleblowing
Oliver Stone is known for depicting famous [rather infamous] real life stories on screen. And the list of his highly successful real-life...
-

 115Cyber Crime
115Cyber Crime“Hacking” cars on the road wirelessly is easy, claims expert
It is perfectly possible to “hack” a car while it is driving on the road, seize control, and force the vehicle into...
-

 247News
247NewsExclusive: Linkin Park official Facebook Page Hacked! Spammed with adverts
In an exclusive report, we are updating that the official verified Facebook fan page of famous rock band Linkin Park (LP) with...
-
 209News
209NewsRedHack hacks Ankara Chamber of Industry website against Nuclear Summit
The famous Turkish Anonymous hacktivist group RedHack has hacked and defaced the official website of Ankara Chamber of Industry ASO, Turkey website (www.aso.org.tr). According...
The Latest
-
 Malware
MalwareU.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks
-
 Malware
MalwareResearchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt Strike
-
 Malware
MalwareeScan Antivirus Update Mechanism Exploited to Spread Backdoors and Miners
-
 Malware
MalwareCoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers
-
 Vulnerabilities
VulnerabilitiesApache Cordova App Harness Targeted in Dependency Confusion Attack
-
 Vulnerabilities
VulnerabilitiesRussia’s APT28 Exploited Windows Print Spooler Flaw to Deploy ‘GooseEgg’ Malware
-
 Vulnerabilities
VulnerabilitiesRansomware Double-Dip: Re-Victimization in Cyber Extortion
-
 Vulnerabilities
VulnerabilitiesResearchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
-
 Malware
MalwareMicrosoft Warns: North Korean Hackers Turn to AI-Fueled Cyber Espionage
-
 Malware
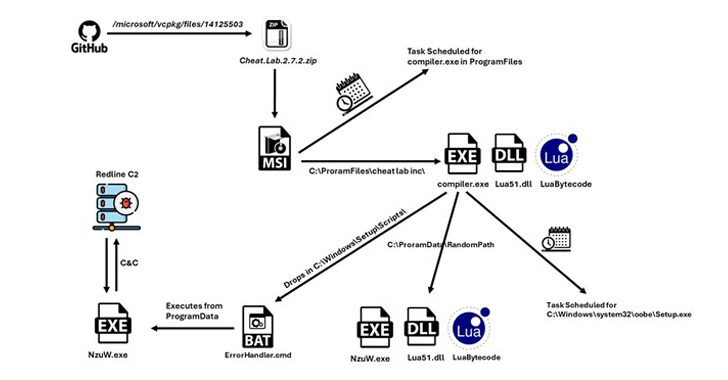
MalwareNew RedLine Stealer Variant Disguised as Game Cheats Using Lua Bytecode for Stealth
-
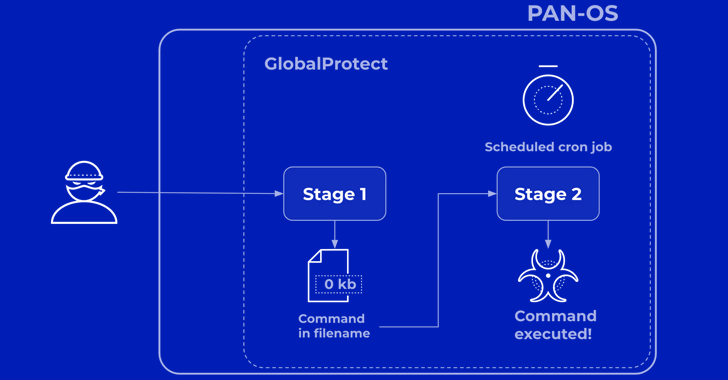 Vulnerabilities
VulnerabilitiesPalo Alto Networks Discloses More Details on Critical PAN-OS Flaw Under Attack
-
 Data Breach
Data BreachCritical Update: CrushFTP Zero-Day Flaw Exploited in Targeted Attacks
-
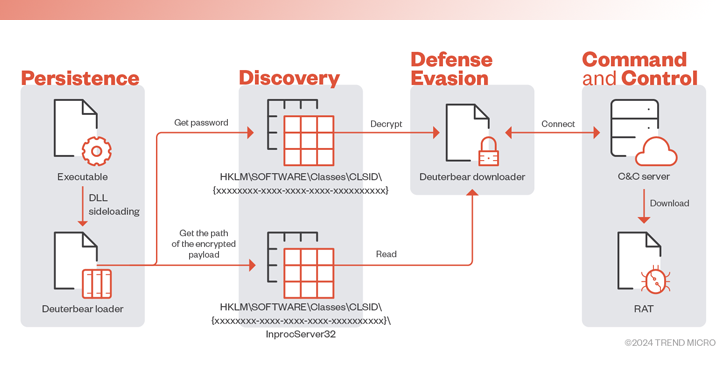 Malware
MalwareBlackTech Targets Tech, Research, and Gov Sectors New ‘Deuterbear’ Tool
-
 Malware
MalwareHackers Target Middle East Governments with Evasive “CR4T” Backdoor
-
 Malware
MalwareOfflRouter Malware Evades Detection in Ukraine for Almost a Decade
-
 Malware
MalwareFIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor
-
 Data Breach
Data BreachNew Android Trojan ‘SoumniBot’ Evades Detection with Clever Tricks
-
 Malware
MalwareMalicious Google Ads Pushing Fake IP Scanner Software with Hidden Backdoor
-
 Malware
MalwareRussian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
-
 Vulnerabilities
VulnerabilitiesGenAI: A New Headache for SaaS Security Teams