Featured News
-

 430Cyber Crime
430Cyber CrimeHeart‑breaking – or side‑splitting? Online video offers worst Heartbleed advice possible
Many mainstream news outlets offered advice on dealing with the Heartbleed bug - some misleading. This week, a spoof video has finally...
-

 311Cyber Events
311Cyber Events#OpJustina: Anonymous allegedly Targets Boston Children’s Hospital against Justina Pelletier custody.
The online collective Anonymous has attacked the Boston Children’s Hospital over the recent Justina Pelletier child-custody case, said a recent report by The Boston Globe. The...
-

 192News
192NewsEgyptian Ministry of Information Website Hacked by Libyan Hackers
The official website of Egyptian Ministry of Information has been hacked and defaced by hackers from a group going with the handle of Libyan...
-
 232Opinion
232OpinionMicrosoft Internet Explorer zero day flaw will be even worse for XP users
Microsoft announces a zero-day security flaw in many versions of Internet Explorer, the first to hit Windows users since XP support was...
-

 87Cyber Crime
87Cyber CrimeNetwork structure must change to resist cyber attacks, warns Dr. Eric Cole
Infosecurity expert Dr Eric Cole is to urge companies to take a close look at their network structure, and change it to...
-

 96Password
96PasswordNew iPad could be latest to add fingerprint security
New evidence has emerged that the new iPad will have fingerprint security built in, as found on the Apple iPhone 5S.
-

 236Cyber Crime
236Cyber CrimeEdward Snowden’s Leaks Helped Terrorists: Hillary Clinton
Hillary Clinton, former Secretary of State, a Senator and the First Lady, is not yet convinced that Snowden leaked the classified documents...
-
 202News
202NewsOfficial Website of City of Westminster, California hacked by Saudi Hackers
Two Saudi Arabian hackers going with the handle of NeT-DeViL and Dr-TaiGaR from Group Hp-Hack have hacked and defaced the official website...
-

 276Surveillance
276SurveillanceInternet is a CIA project, be careful before making Google searches: Putin
Russian president Vladimir Putin has said that Internet is a CIA project and Russians should be careful while making Google searches. While...
-

 239News
239NewsSyrian hacker hacks and defaces UNICEF New Zealand Official blog for Free Syria
A Syrian hacker going with the handle of Dr.SHA6H has hacked and defaced the official blog of The United Nations Children’s Fund (UNICEF) designated for...
-

 277Cyber Events
277Cyber EventsSnowden Delivers his Maiden Speech as Glasgow University Rector
The whistleblower kept the students glued as he addressed them via a video link from Russia stressing on “speaking out” for human...
-

 293Cyber Crime
293Cyber CrimeThe perfect job? Dream on! Five signs a job offer is a scam
Job scams are a permanent fixture in cyberspace. Anyone who has posted their resume online has offered cyber gangs two crucial pieces...
-

 72Cyber Crime
72Cyber CrimeBad business: ALL major companies are hosting malware – Cisco
Every single one of 30 major companies tested by Cisco over the course of 2013 had malicious traffic on their networks, according...
-

 94Privacy
94PrivacyYoung people fear internet of things will give away their secrets
Young people are seriously worrried about connected gadgets when it comes to privacy - worrying that 'connected' gadgets such as Smart TVs...
-

 204Cyber Events
204Cyber EventsAnonymous Exposes How Rothschild Family Profited from missing Malaysian Airliner MH 370
A couple of weeks ago, a video was uploaded on YouTube by online hacktivist group Anonymous. In the video anonymous gives an depth...
-

 234Data Security
234Data SecurityAndroid Trojan Virus: iBanking Malware ‘Qadars’ Targets Facebook Users via Webinjects
Cyber criminals have targeted millions of Facebook users through a sophisticated Android Trojan app that can bypass the two-factor authentication shield used...
-

 70Cyber Crime
70Cyber CrimeGoogle offers refunds for buyers of fake Virus Shield app
Google is offering full refunds to buyers of the Virus Shield app which briefly topped the Android charts last week - but...
-

 72Cyber Crime
72Cyber CrimeLack of cyber risk insurance could lead to “global financial shock”
The financial damage caused by a large data breach or malicious employee activity can be enormous, but the lack of financial protection...
-

 98Kids Online
98Kids OnlineHow do you know if your child’s ID has been stolen?
When it comes to identity theft, the most successful attack is on the person least likely to be aware of activity being...
-

 124Privacy
124PrivacyCybercrime evolves as criminal gangs join forces with spies – report
Hackers targeting sensitive information or stealing from retailers work at such speed that customers often notice data breaches first - and for...
The Latest
-
 Cyber Attack
Cyber AttackU.S. Treasury Hamas Spokesperson for Cyber Influence Operations
-
 Cyber Attack
Cyber AttackHackers Deploy Python Backdoor in Palo Alto Zero-Day Attack
-
 Cyber Attack
Cyber AttackZero-Day Alert: Critical Palo Alto Networks PAN-OS Flaw Under Active Attack
-
 Data Breach
Data BreachU.S. Federal Agencies Ordered to Hunt for Signs of Microsoft Breach and Mitigate Risks
-
 Malware
MalwareTA547 Phishing Attack Hits German Firms with Rhadamanthys Stealer
-
 Vulnerabilities
VulnerabilitiesPython’s PyPI Reveals Its Secrets
-
 Vulnerabilities
VulnerabilitiesFortinet Rolls Out Critical Security Patches for FortiClientLinux Vulnerability
-
 Malware
Malware‘eXotic Visit’ Spyware Campaign Targets Android Users in India and Pakistan
-
 Malware
MalwareRaspberry Robin Returns: New Malware Campaign Spreading Through WSF Files
-
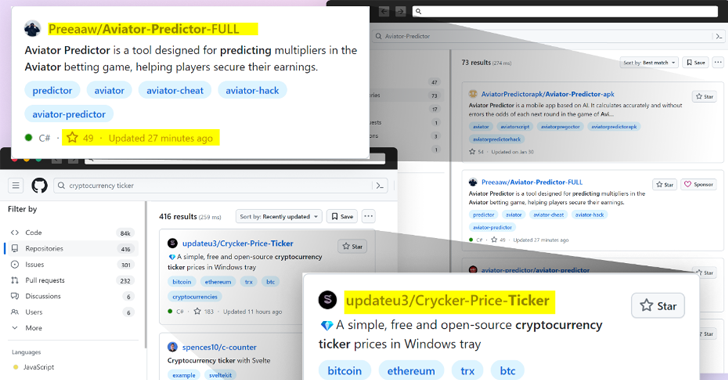 Malware
MalwareBeware: GitHub’s Fake Popularity Scam Tricking Developers into Downloading Malware
-
 Vulnerabilities
VulnerabilitiesWebinar: Learn How to Stop Hackers from Exploiting Hidden Identity Weaknesses
-
 Vulnerabilities
VulnerabilitiesMicrosoft Fixes 149 Flaws in Huge April Patch Release, Zero-Days Included
-
 Vulnerabilities
VulnerabilitiesCritical ‘BatBadBut’ Rust Vulnerability Exposes Windows Systems to Attacks
-
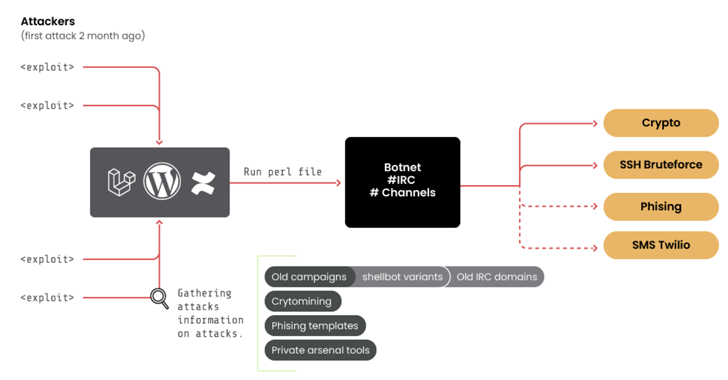 Vulnerabilities
Vulnerabilities10-Year-Old ‘RUBYCARP’ Romanian Hacker Group Surfaces with Botnet
-
 Malware
MalwareHackers Targeting Human Rights Activists in Morocco and Western Sahara
-
 Vulnerabilities
VulnerabilitiesResearchers Discover LG Smart TV Vulnerabilities Allowing Root Access
-
 Malware
MalwareCL0P’s Ransomware Rampage – Security Measures for 2024
-
 Malware
MalwareAttackers Using Obfuscation Tools to Deliver Multi-Stage Malware via Invoice Phishing
-
 Vulnerabilities
VulnerabilitiesCritical Flaws Leave 92,000 D-Link NAS Devices Vulnerable to Malware Attacks
-
 Malware
MalwareWatch Out for ‘Latrodectus’ – This Malware Could Be In Your Inbox