Featured News
-

 186Cyber Crime
186Cyber CrimeLiberty Reserve Payment Processor Busted, Owner arrested for Money Laundering
The official website of Liberty Reserve (), known for its services such as payment processing and transfer has been shutdown by the...
-

 245News
245News#usaOPERATION1: Akron Canton Airport Hacked, 15,000 credentials leaked by Turkish Ajan Hacking Group
Online hackavists from Turkish Ajan hacking group have hacked and defaced the official website of Akron Canton Airport (http://www.akroncantonairport.com), as a result information of...
-
 121News
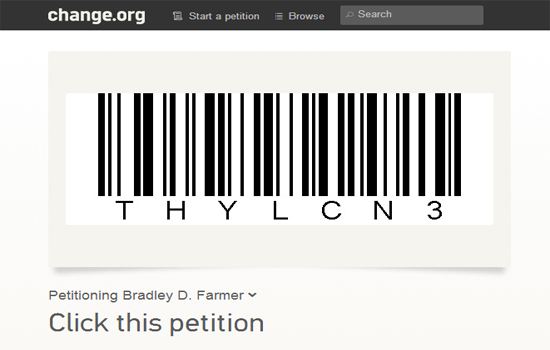
121NewsPetitions Website Change.org Hacked and Edited by Terminal hacker
A hacker going with the handle of Terminal Hacker has hacked famous petition site Change.org, as a result the hacker successfully changed and at some...
-
 382News
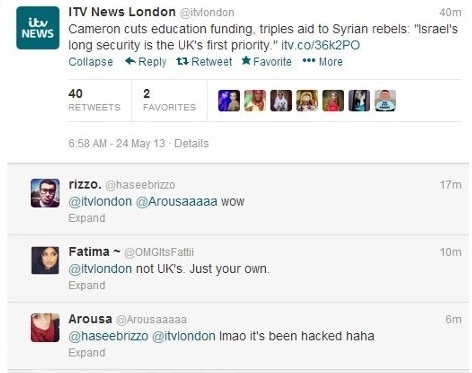
382NewsITV News London Twitter account Hacked by Syrian Electronic Army
The Pro Syrian President Bashar al-Assad hackers from Syrian Electronic Army has hacked the official Twitter account of British broadcaster ITV News,...
-

 253News
253NewsUnited Nations Information Center Jakarta Websites Hacked by Dr.SHA6H
Famous hackavist Dr.SHA6H who is known for his high profile is back with another one, this time by hacking and defacing 3 official...
-

 98Malware
98MalwareTax returns: Slovakian spyware campaign
ESET’s Security Research Lab details a malware-spreading campaign leveraging the deadline for tax returns in Slovakia and examines a case of infection...
-

 228News
228News50 Israeli Websites Hacked by CapoO_TunisiAnoO
Israeli cyber space is always under attack by hackers from all aver the world, one of those hackers is known as World...
-

 73Cyber Crime
73Cyber Crime“Stronger action” urged in face of IP theft from American companies
American companies are facing an “unprecedented” onslaught of data theft, costing “hundreds of billions”, according to a report by a private group...
-

 248News
248NewsOfficial UNICEF and UNDP Croatia Websites Hacked by Turkish Hackers
Three Turkish hackers going with the handles of eboz , flowchart and Vezir.04, collectively have hacked and defaced the official websites of United Nations...
-

 91Cyber Crime
91Cyber CrimeElectrical grids “woefully prepared” for cyber attacks, warns analyst
Electrical grids worldwide have become more susceptible to cyber attacks, due to the use of industrial control systems, according to market analysts...
-

 231News
231News49 Israeli Websites Hacked by The key40 from Algeria
An Algerian hacker going with the handle of ‘the key40’ has hacked and defaced total 49 Israeli websites. The sites were left...
-

 246Surveillance
246SurveillanceChinese Hackers who breached Google in 2010, gained access to massive Spy Data: US officials
Back in the year 2010, the Breach performed by Chinese hackers that was a part of the operation termed as Operation Aurora...
-

 76Cyber Crime
76Cyber CrimeTwitter beefs up security after wave of attacks on media sites
Twitter has introduced a new two-factor security system - an optional "extra layer" of security which should help to prevent unauthorised access...
-

 77Cyber Crime
77Cyber CrimeSmall business cybercrime costs $6,000 a year, says British group
Cybercrime is costing small businesses an average of £4,000 ($6000) a year, according to the British Federation of Small Businesses (FSB). A...
-

 95Privacy
95PrivacyXbox One Kinect microphone “always on” security fears
The Xbox One Kinect microphone – one of the hi-tech new features of Microsoft’s new Xbox One console – has raised security...
-

 239News
239NewsOfficial United Nation Pacific Website Hacked by Pakistani Hacker
H4x0r HuSsY from Pakistan who was in news for his high profile hacks against India and Sri Lankan is back with another one, this...
-

 146News
146NewsMicrosoft Warns of New Trojan Hijacking Facebook Accounts
Microsoft has released a warning of a new malware disguised extension for Google Chrome and Firefox add-on, began circulating on Facebook, targeting...
-

 175Surveillance
175SurveillanceHow Brazilian Government is Spying on its Citizens
The federal government of Brazil may indeed have access to private data that citizens may have provided to any private company. More...
-

 164News
164NewsCNN International Breached, Accounts Leaked, Claims to Post Fake Article By @Reckz0r
A hacker going with the Twitter handle of @Reckz0r has claimed to hack the official website of CNN’s International Edition website (http://edition.cnn.com/) for...
-

 95Cyber Crime
95Cyber CrimeCyber attacks on America “will get worse”, warns NSA director
Cyber attacks on America will continue to escalate, according to National Security Director Keith Alexander, speaking to the Reuters Cybersecurity Summit in...
The Latest
-
 Malware
MalwareU.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks
-
 Malware
MalwareResearchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt Strike
-
 Malware
MalwareeScan Antivirus Update Mechanism Exploited to Spread Backdoors and Miners
-
 Malware
MalwareCoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers
-
 Vulnerabilities
VulnerabilitiesApache Cordova App Harness Targeted in Dependency Confusion Attack
-
 Vulnerabilities
VulnerabilitiesRussia’s APT28 Exploited Windows Print Spooler Flaw to Deploy ‘GooseEgg’ Malware
-
 Vulnerabilities
VulnerabilitiesRansomware Double-Dip: Re-Victimization in Cyber Extortion
-
 Vulnerabilities
VulnerabilitiesResearchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
-
 Malware
MalwareMicrosoft Warns: North Korean Hackers Turn to AI-Fueled Cyber Espionage
-
 Malware
MalwareNew RedLine Stealer Variant Disguised as Game Cheats Using Lua Bytecode for Stealth
-
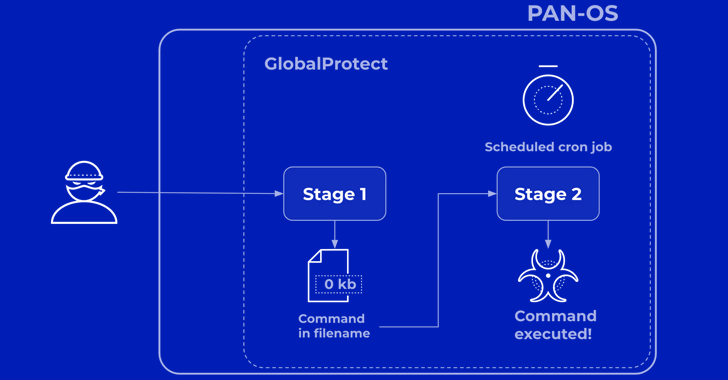 Vulnerabilities
VulnerabilitiesPalo Alto Networks Discloses More Details on Critical PAN-OS Flaw Under Attack
-
 Data Breach
Data BreachCritical Update: CrushFTP Zero-Day Flaw Exploited in Targeted Attacks
-
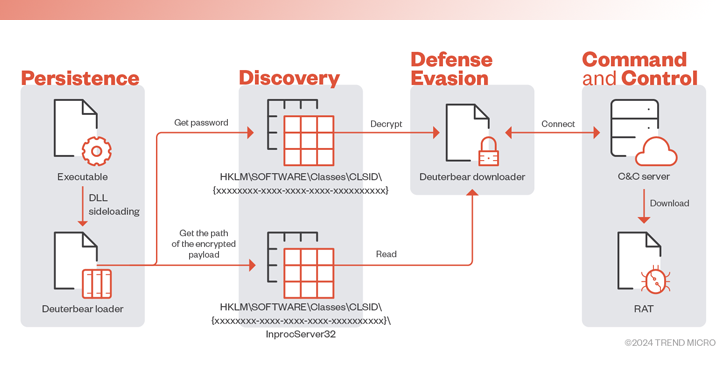 Malware
MalwareBlackTech Targets Tech, Research, and Gov Sectors New ‘Deuterbear’ Tool
-
 Malware
MalwareHackers Target Middle East Governments with Evasive “CR4T” Backdoor
-
 Malware
MalwareOfflRouter Malware Evades Detection in Ukraine for Almost a Decade
-
 Malware
MalwareFIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor
-
 Data Breach
Data BreachNew Android Trojan ‘SoumniBot’ Evades Detection with Clever Tricks
-
 Malware
MalwareMalicious Google Ads Pushing Fake IP Scanner Software with Hidden Backdoor
-
 Malware
MalwareRussian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
-
 Vulnerabilities
VulnerabilitiesGenAI: A New Headache for SaaS Security Teams