Featured News
-

 1.8KMalware
1.8KMalwareVietnam-Based Hackers Steal Financial Data Across Asia with Malware
A suspected Vietnamese-origin threat actor has been observed targeting victims in several Asian and Southeast Asian countries with malware designed to harvest...
-

 136Malware
136MalwareNew Phishing Campaign Targets Oil & Gas with Evolved Data-Stealing Malware
An updated version of an information-stealing malware called Rhadamanthys is being used in phishing campaigns targeting the oil and gas sector. “The...
-

 777Vulnerabilities
777VulnerabilitiesConsiderations for Operational Technology Cybersecurity
Operational Technology (OT) refers to the hardware and software used to change, monitor, or control the enterprise’s physical devices, processes, and events....
-

 1.4KVulnerabilities
1.4KVulnerabilitiesNew HTTP/2 Vulnerability Exposes Web Servers to DoS Attacks
New research has found that the CONTINUATION frame in the HTTP/2 protocol can be exploited to conduct denial-of-service (DoS) attacks. The technique...
-

 3.9KVulnerabilities
3.9KVulnerabilitiesU.S. Cyber Safety Board Slams Microsoft Over Breach by China-Based Hackers
The U.S. Cyber Safety Review Board (CSRB) has criticized Microsoft for a series of security lapses that led to the breach of...
-

 3.1KMalware
3.1KMalwareGoogle Chrome Beta Tests New DBSC Protection Against Cookie-Stealing Attacks
Google on Tuesday said it’s piloting a new feature in Chrome called Device Bound Session Credentials (DBSC) to help protect users against...
-
 3.8KMalware
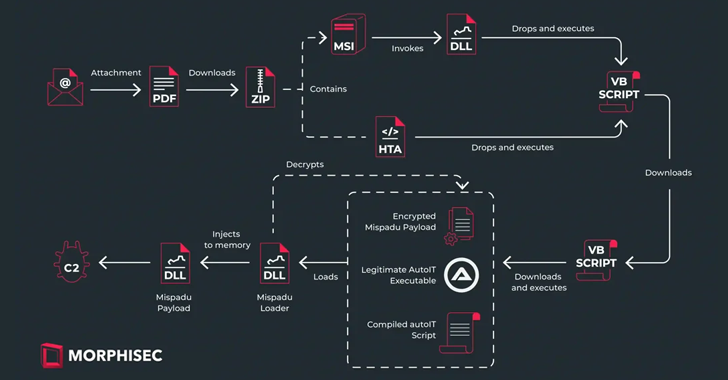
3.8KMalwareMispadu Trojan Targets Europe, Thousands of Credentials Compromised
The banking trojan known as Mispadu has expanded its focus beyond Latin America (LATAM) and Spanish-speaking individuals to target users in Italy,...
-

 4.2KVulnerabilities
4.2KVulnerabilitiesCritical Security Flaw Found in Popular LayerSlider WordPress Plugin
A critical security flaw impacting the LayerSlider plugin for WordPress could be abused to extract sensitive information from databases, such as password...
-

 595Data Security
595Data SecurityHow to Check if a Linux Distribution is Compromised by the XZ Utils Backdoor in 6 Steps
In an unsettling development that emerged late last week, the open-source community was thrust into a state of high alert following the...
-
 5.0KVulnerabilities
5.0KVulnerabilitiesMalicious Code in XZ Utils for Linux Systems Enables Remote Code Execution
The malicious code inserted into the open-source library XZ Utils, a widely used package present in major Linux distributions, is also capable...
-

 4.2KMalware
4.2KMalwareChina-linked Hackers Deploy New ‘UNAPIMON’ Malware for Stealthy Operations
A threat activity cluster tracked as Earth Freybug has been observed using a new malware called UNAPIMON to fly under the radar....
-
 892Malware
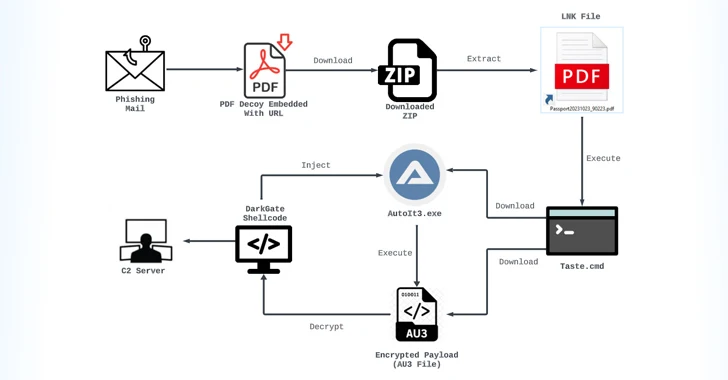
892MalwareMassive Phishing Campaign Strikes Latin America: Venom RAT Targeting Multiple Sectors
The threat actor known as TA558 has been attributed to a new massive phishing campaign that targets a wide range of sectors...
-

 4.9KMalware
4.9KMalwareDetecting Windows-based Malware Through Better Visibility
Despite a plethora of available security solutions, more and more organizations fall victim to Ransomware and other threats. These continued threats aren’t...
-
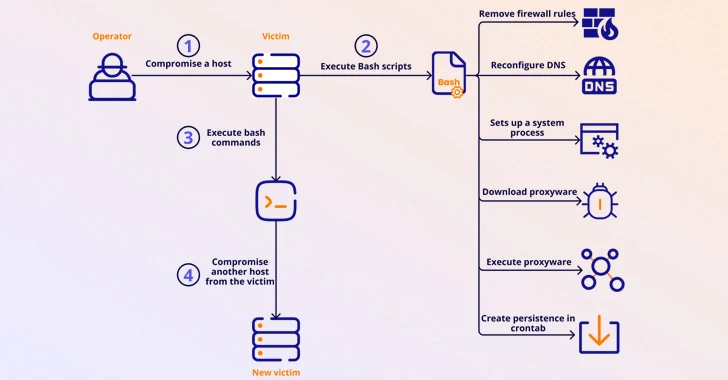
 490Malware
490MalwareMalicious Apps Caught Secretly Turning Android Phones into Proxies for Cybercriminals
Several malicious Android apps that turn mobile devices running the operating system into residential proxies (RESIPs) for other threat actors have been...
-

 3.8KMalware
3.8KMalwareVultur Android Banking Trojan Returns with Upgraded Remote Control Capabilities
The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and detection evasion techniques,...
-

 4.6KMalware
4.6KMalwareHackers Target macOS Users with Malicious Ads Spreading Stealer Malware
Malicious ads and bogus websites are acting as a conduit to deliver two different stealer malware, including Atomic Stealer, targeting Apple macOS...
-

 5.0KVulnerabilities
5.0KVulnerabilitiesUrgent: Secret Backdoor Found in XZ Utils Library, Impacts Major Linux Distros
Red Hat on Friday released an “urgent security alert” warning that two versions of a popular data compression library called XZ Utils...
-

 963Malware
963MalwareTheMoon Botnet Resurfaces, Exploiting EoL Devices to Power Criminal Proxy
A botnet previously considered to be rendered inert has been observed enslaving end-of-life (EoL) small home/small office (SOHO) routers and IoT devices...
-

 2.1KVulnerabilities
2.1KVulnerabilitiesThe Golden Age of Automated Penetration Testing is Here
Network penetration testing plays a vital role in detecting vulnerabilities that can be exploited. The current method of performing pen testing is...
-

 1.2KVulnerabilities
1.2KVulnerabilitiesNew Linux Bug Could Lead to User Password Leaks and Clipboard Hijacking
Details have emerged about a vulnerability impacting the “wall” command of the util-linux package that could be potentially exploited by a bad...
The Latest
-
 Malware
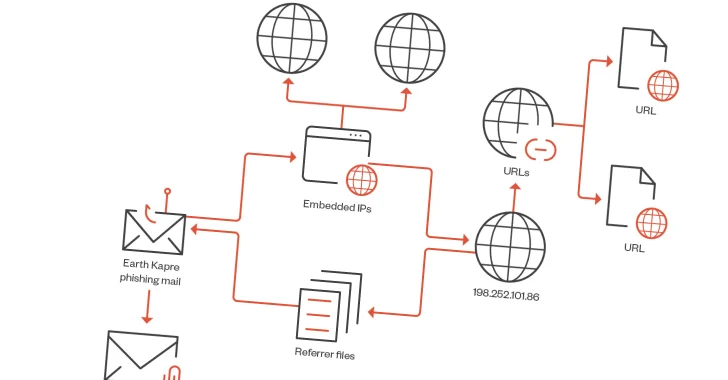
MalwareRussian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
-
 Vulnerabilities
VulnerabilitiesCritical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
-
 Vulnerabilities
VulnerabilitiesHackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
-
 Malware
MalwareTA558 Hackers Weaponize Images for Wide-Scale Malware Attacks
-
 Vulnerabilities
VulnerabilitiesAWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs
-
 Vulnerabilities
VulnerabilitiesWidely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
-
 Malware
MalwareHive RAT Creators and $3.5M Cryptojacking Mastermind Arrested in Global Crackdown
-
 Vulnerabilities
VulnerabilitiesIntel and Lenovo BMCs Contain Unpatched Lighttpd Server Flaw
-
 Vulnerabilities
VulnerabilitiesAI Copilot: Launching Innovation Rockets, But Beware of the Darkness Ahead
-
 Malware
MalwareChinese-Linked LightSpy iOS Spyware Targets South Asian iPhone Users
-
 Vulnerabilities
VulnerabilitiesPalo Alto Networks Releases Urgent Fixes for Exploited PAN-OS Vulnerability
-
 Cyber Attack
Cyber AttackU.S. Treasury Hamas Spokesperson for Cyber Influence Operations
-
 Cyber Attack
Cyber AttackHackers Deploy Python Backdoor in Palo Alto Zero-Day Attack
-
 Malware
MalwarePopular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files
-
 Malware
MalwareIranian MuddyWater Hackers Adopt New C2 Tool ‘DarkBeatC2’ in Latest Campaign
-
 Cyber Attack
Cyber AttackZero-Day Alert: Critical Palo Alto Networks PAN-OS Flaw Under Active Attack
-
 Malware
MalwareSneaky Credit Card Skimmer Disguised as Harmless Facebook Tracker
-
 Data Breach
Data BreachU.S. Federal Agencies Ordered to Hunt for Signs of Microsoft Breach and Mitigate Risks
-
 Malware
MalwareTA547 Phishing Attack Hits German Firms with Rhadamanthys Stealer
-
 Vulnerabilities
VulnerabilitiesPython’s PyPI Reveals Its Secrets