Featured News
-
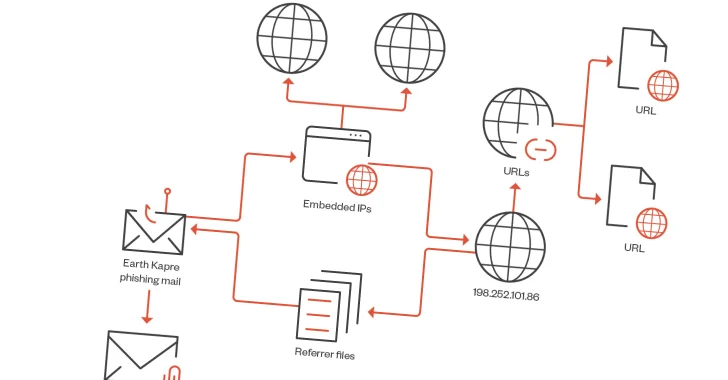
 491Malware
491MalwareMalicious Apps Caught Secretly Turning Android Phones into Proxies for Cybercriminals
Several malicious Android apps that turn mobile devices running the operating system into residential proxies (RESIPs) for other threat actors have been...
-

 3.8KMalware
3.8KMalwareVultur Android Banking Trojan Returns with Upgraded Remote Control Capabilities
The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and detection evasion techniques,...
-

 4.6KMalware
4.6KMalwareHackers Target macOS Users with Malicious Ads Spreading Stealer Malware
Malicious ads and bogus websites are acting as a conduit to deliver two different stealer malware, including Atomic Stealer, targeting Apple macOS...
-

 5.0KVulnerabilities
5.0KVulnerabilitiesUrgent: Secret Backdoor Found in XZ Utils Library, Impacts Major Linux Distros
Red Hat on Friday released an “urgent security alert” warning that two versions of a popular data compression library called XZ Utils...
-

 964Malware
964MalwareTheMoon Botnet Resurfaces, Exploiting EoL Devices to Power Criminal Proxy
A botnet previously considered to be rendered inert has been observed enslaving end-of-life (EoL) small home/small office (SOHO) routers and IoT devices...
-

 2.1KVulnerabilities
2.1KVulnerabilitiesThe Golden Age of Automated Penetration Testing is Here
Network penetration testing plays a vital role in detecting vulnerabilities that can be exploited. The current method of performing pen testing is...
-

 1.2KVulnerabilities
1.2KVulnerabilitiesNew Linux Bug Could Lead to User Password Leaks and Clipboard Hijacking
Details have emerged about a vulnerability impacting the “wall” command of the util-linux package that could be potentially exploited by a bad...
-

 1.8KMalware
1.8KMalwarePyPI Halts Sign-Ups Amid Surge of Malicious Package Uploads Targeting Developers
The maintainers of the Python Package Index (PyPI) repository briefly suspended new user sign-ups following an influx of malicious projects uploaded as...
-

 2.1KVulnerabilities
2.1KVulnerabilitiesLinux Version of DinodasRAT Spotted in Cyber Attacks Across Several Countries
A Linux version of a multi-platform backdoor called DinodasRAT has been detected in the wild targeting China, Taiwan, Turkey, and Uzbekistan, new...
-

 1.7KMalware
1.7KMalwareFinland Blames Chinese Hacking Group APT31 for Parliament Cyber Attack
The Police of Finland (aka Poliisi) has formally accused a Chinese nation-state actor tracked as APT31 for orchestrating a cyber attack targeting...
-

 1.2KVulnerabilities
1.2KVulnerabilitiesNew ZenHammer Attack Bypasses RowHammer Defenses on AMD CPUs
Cybersecurity researchers from ETH Zurich have developed a new variant of the RowHammer DRAM (dynamic random-access memory) attack that, for the first...
-

 3.4KMalware
3.4KMalwareNew Webinar: Avoiding Application Security Blind Spots with OPSWAT and F5
Considering the ever-changing state of cybersecurity, it’s never too late to ask yourself, “am I doing what’s necessary to keep my organization’s...
-

 3.0KVulnerabilities
3.0KVulnerabilitiesBehind the Scenes: The Art of Safeguarding Non-Human Identities
In the whirlwind of modern software development, teams race against time, constantly pushing the boundaries of innovation and efficiency. This relentless pace...
-

 4.0KMalware
4.0KMalwareHackers Hit Indian Defense, Energy Sectors with Malware Posing as Air Force Invite
Indian government entities and energy companies have been targeted by unknown threat actors with an aim to deliver a modified version of...
-
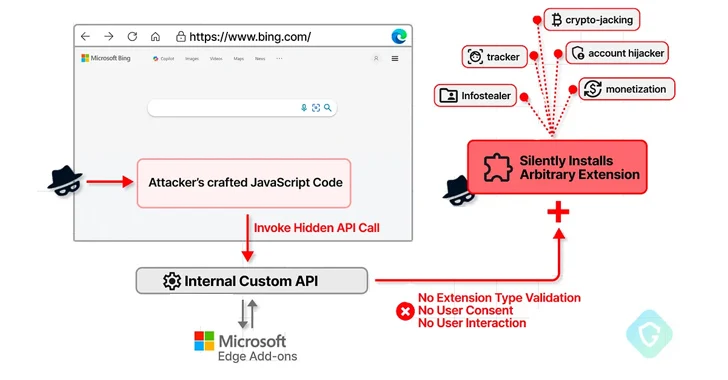
 2.7KVulnerabilities
2.7KVulnerabilitiesMicrosoft Edge Bug Could Have Allowed Attackers to Silently Install Malicious Extensions
A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users’ systems and...
-

 4.6KVulnerabilities
4.6KVulnerabilitiesSASE Solutions Fall Short Without Enterprise Browser Extensions, New Report Reveals
As SaaS applications dominate the business landscape, organizations need optimized network speed and robust security measures. Many of them have been turning...
-

 2.0KVulnerabilities
2.0KVulnerabilitiesCritical Unpatched Ray AI Platform Vulnerability Exploited for Cryptocurrency Mining
Cybersecurity researchers are warning that threat actors are actively exploiting a “disputed” and unpatched vulnerability in an open-source artificial intelligence (AI) platform...
-
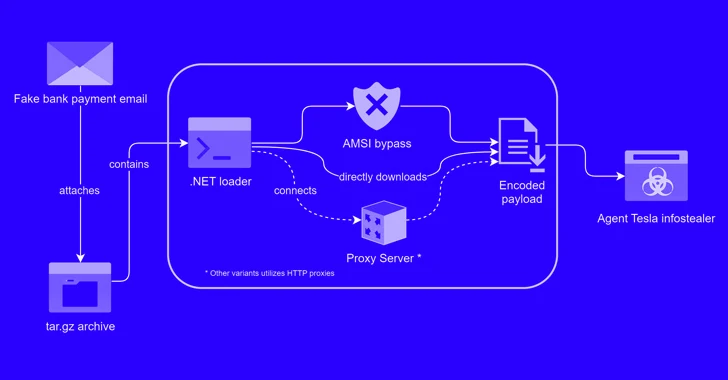
 313Vulnerabilities
313VulnerabilitiesAlert: New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla....
-

 2.1KVulnerabilities
2.1KVulnerabilitiesTwo Chinese APT Groups Ramp Up Cyber Espionage Against ASEAN Countries
Two China-linked advanced persistent threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian...
-

 4.5KData Security
4.5KData SecuritySocial Media Conspiracy Theory: Was the Baltimore Bridge Collision a Result of Cyber Attack?
On an unexpected Tuesday, the collision of a container ship with the Francis Scott Key Bridge in Baltimore not only disrupted the...
The Latest
-
 Data Breach
Data BreachCritical Update: CrushFTP Zero-Day Flaw Exploited in Targeted Attacks
-
 Data Breach
Data BreachNew Android Trojan ‘SoumniBot’ Evades Detection with Clever Tricks
-
 Malware
MalwareRussian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
-
 Vulnerabilities
VulnerabilitiesCritical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
-
 Vulnerabilities
VulnerabilitiesHackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
-
 Vulnerabilities
VulnerabilitiesCompromising Cryptographic Key Security Through PuTTY: A Deep Dive into CVE-2024-31497
-
 Malware
MalwareTA558 Hackers Weaponize Images for Wide-Scale Malware Attacks
-
 Vulnerabilities
VulnerabilitiesAWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs
-
 Vulnerabilities
VulnerabilitiesWidely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
-
 Data Breach
Data BreachFTC Fines Mental Health Startup Cerebral $7 Million for Major Privacy Violations
-
 Malware
MalwareHive RAT Creators and $3.5M Cryptojacking Mastermind Arrested in Global Crackdown
-
 Vulnerabilities
VulnerabilitiesIntel and Lenovo BMCs Contain Unpatched Lighttpd Server Flaw
-
 Vulnerabilities
VulnerabilitiesAI Copilot: Launching Innovation Rockets, But Beware of the Darkness Ahead
-
 Data Breach
Data BreachMuddled Libra Shifts Focus to SaaS and Cloud for Extortion and Data Theft Attacks
-
 Data Breach
Data BreachTiming is Everything: The Role of Just-in-Time Privileged Access in Security Evolution
-
 Malware
MalwareChinese-Linked LightSpy iOS Spyware Targets South Asian iPhone Users
-
 Vulnerabilities
VulnerabilitiesPalo Alto Networks Releases Urgent Fixes for Exploited PAN-OS Vulnerability
-
 Cyber Attack
Cyber AttackU.S. Treasury Hamas Spokesperson for Cyber Influence Operations
-
 Cyber Attack
Cyber AttackHackers Deploy Python Backdoor in Palo Alto Zero-Day Attack
-
 Malware
MalwarePopular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files