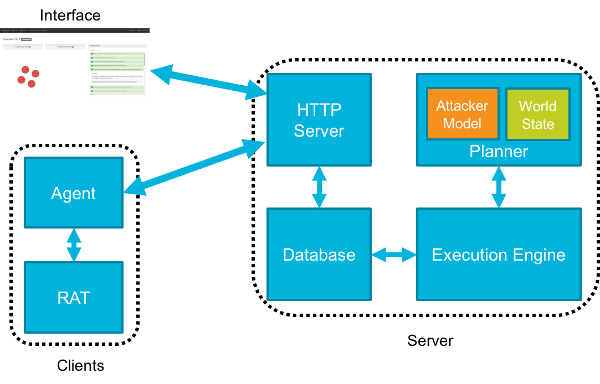
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during operation using a planning system and a pre-configured adversary model based on the Adversarial Tactics, Techniques & Common Knowledge (ATT&CK™) project. These features allow CALDERA to dynamically operate over a set of systems using variable behavior, which better represents how human adversaries perform operations than systems that follow prescribed sequences of actions.
CALDERA is useful for defenders who want to generate real data that represents how an adversary would typically behave within their networks. Since CALDERA’s knowledge about a network is gathered during its operation and is used to drive its use of techniques to reach a goal, defenders can get a glimpse into how the intrinsic security dependencies of their network allow an adversary to be successful. CALDERA is useful for identifying new data sources, creating and refining behavioral-based intrusion detection analytics, testing defenses and security configurations, and generating experience for training.
Considerations and Limitations
The path chaining problems CALDERA’s planning system is designed to solve are computationally intensive. While CALDERA’s server does not have hardware requirements beyond a typical software developer’s system, there are limitations on the number of systems CALDERA can operate over before the planning time between actions will cause significant delays or the system to fail. Thus it is not recommended that CALDERA be used against sets of systems larger than 20.
CALDERA performs real actions on systems when operating. If it is being used in a production network, beyond an isolated lab network, then care should be taken to inform any network security staff, administrators, or users who may be impacted prior to using CALDERA to deconflict any issues that may arise.
CALDERA uses other open source tools as part of its repository of techniques. Some of these tools are categorized as penetration testing or security auditing tools. See Security for more information.
CALDERA does not use or repurpose known adversary malware. It focuses on using adversary behavior documented within ATT&CK, which can be employed in many different ways regardless of specific pieces of malware an adversary may use.
CALDERA does not emulate adversary command and control (C2) channels. The variation in adversary C2 protocols and communication methods is vast and is considered out of scope.
CALDERA also does not use software exploitation. There are many free and commercial tools that can be used to assess software weakness and exploitability. CALDERA should not be used for this purpose.
Requirements
Operating System Requirements
CALDERA has both a Server and an Agent, the requirements for each are different.
The agent is installed on each computer that will be involved in the emulation exercise. The agent supports 64 bit versions of Windows 7 and higher.
The server must be installed on a computer that is accessible over the network to all agents. Both Windows and Linux are supported.
Network Requirements
CALDERA operates in a Windows Enterprise network environment. At a minimum this will contain a Domain Controller running Windows Server 2008 R2 through 2016 and two Windows Enterprise computers joined to that domain.
Internet Requirements
An Internet connection is required to install CALDERA, however once installation is complete an Internet connection is no longer required. It is possible to install CALDERA without Internet by manually copying CALDERA’s dependencies to the install server. Contact CALDERA’s developers for more information.

Research
CALDERA is a MITRE research project and is an implementation of some of the ideas described in the following papers:
Intelligent, Automated Red Team Emulation
Analysis of Automated Adversary Emulation Techniques