A new research methodology has allowed specialists to track active vendors in several dark web platformsbased solely on how they write their ads and posts. Using stylometry, the experts were able to analyze thousands of identities of various suppliers in black markets and identify if these profiles correspond to specific people.
This study involved the collection of nodes of information extracted from vendor profiles on four now-shutdown cybercriminal platforms, including Valhalla, Dream Market, Evolution, and Silk Road 2.
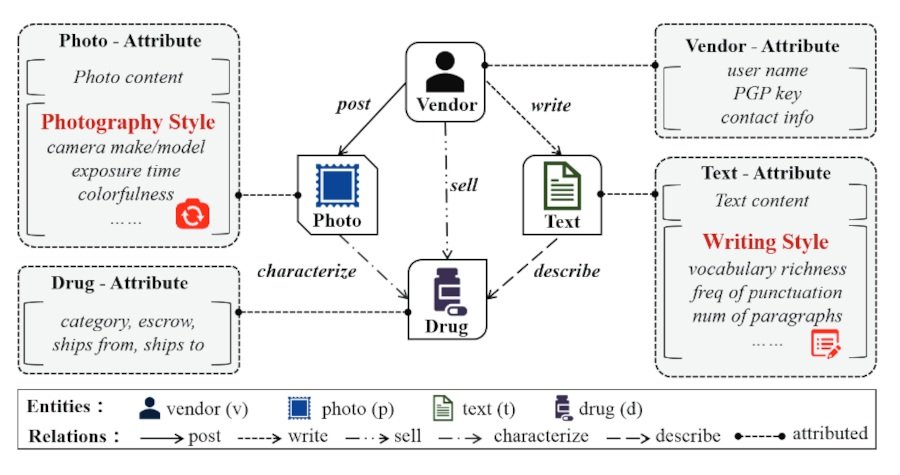
The analysis begins with the collection of various sets of characteristics of the profiles of these sellers; to identify a specific marketer, researchers analyze the content of the publication and the style of writing. Overall, the research required analysis of certain characteristics, including:
- Lexicon: Number of characters and digits; number of words; average length of words; richness of language
- Syntax: Use of punctuation marks; frequency of functional words; number of sentences beginning with a capital letter; n-gram frequency
- Structure: Total number of paragraphs; use of indentation and other separators between paragraphs; number of words/phrases/characters per paragraph
The analysis allowed grouping the publications according to their characteristics, thus identifying which profiles could be operated by the same person. In addition to the use of language, other characteristics, such as metadata in the photographs attached to these publications, underwent similar analysis.
To obtain the final results, the researchers divided the analyzed publications into pairs, concluding that among the 789 pairs analyzed more than 90% could be attributed to the same author, while the process was considered inconclusive for only 2.7% of the pairs analyzed.
In the future this could prove beneficial for law enforcement agencies, which in every investigation related to the sale of illegal items on the dark web experience problems trying to find all possible profiles operated by the same threat actor. In some cases, such as Canna_Bars, agents have already resorted to stylometry to support their hypotheses, although this is not yet a widespread practice.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















