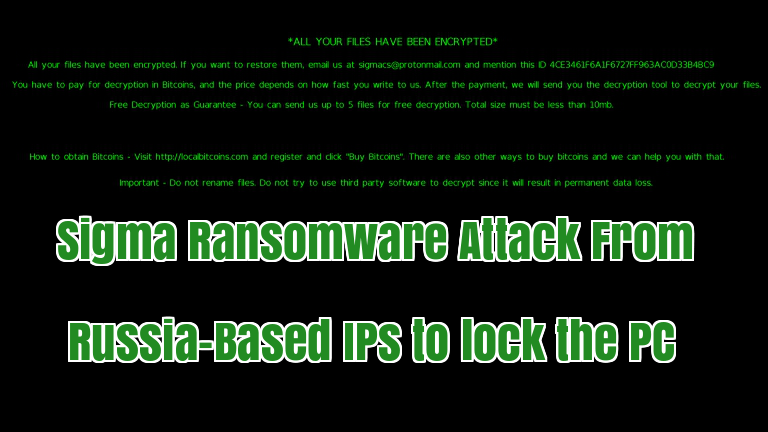
Newly discovered Sigma Ransomware spreading from Russia-based IP’s with the variety of social engineering techniques to compromise victims and lock the infected computer.
Users Targeting via malicious SPAM Emails that contain a statement which comes from “United States District Court” with a malicious attachment.

Nowadays attackers using the Email scam to target the victim to perform various malicious activities and playing with the user by some emergency strings of fear and increase the victim’s curiosity.
Sigma Ransomware Attack conducted from around 32 Russian based IP’s and the attacker registered the specific domain which is specified using to perform various attacks.
Malware authors used more obfustication functions by requesting the password to open the file evade the detection.
Sigma Ransomware Working Function
Initially, the Malicious files required a password to open because it tricks the user to download the attachment that should be protected since the mail come from the court, a clever trick used by an attacker.
If it Finds the Macros are turned off on the victim’s machine then it convenience the users to turn it on which contains malicious VBScript.
Later on, VBScript will download the original Sigma Ransomware payload from attack command and control server and save it into %TEMP% folder.
Downloaded malware mimics as a legitimate svchost.exe process which helps to download one more malware.
The Malware used various of obfuscation technique to hide it and evade the detection and it kills itself if it finds ay virtual machine or sandboxes.
According to Comodo Research, Unlike some of its close ransomware relatives, Sigma does not act immediately but lurks and makes covert reconnaissance first. It creates a list of valuable files, counts them and sends this value to its C&C server along with other information about the victim’s machine.
Also if the sigma Ransomware finds no files then it deletes itself and it stops the infection if it finds the country location of Russian Federation or Ukraine.
Later it connects to its command & control servers and establishes the Tor Connection and Sigma Ransomware begins to encrypt files on the machine.
After complete encryption, it will display the ransom notes that contains the detailed information of the attack and the attack request the victims to contact them via [email protected] and also victim need to mention the infection ID.