Support scams and fake alerts are still big business. We look at scammer psychology and a little parapsychology.
Here are some recent variations on the support scam theme. If you’re unfamiliar with the whole tech support plan phenomenon, I maintain a list of resources on the AVIEN resource page, which includes all the papers and all but the very earliest blog articles on the topic that I’ve written for ESET and other sites, along with some excellent articles from some of our friends in the industry. If you are well acquainted with support scams, you may nevertheless find it useful – and even entertaining – to see what kinds of alert the scammers are currently using in the hope of luring potential victims into calling a call centre number, seeking help for problems they don’t actually have.
Security and Anti-Security
Our support team recently received a message from an ESET user saying they’d had a pop-up warning from one of our competitors. The warning claimed that the recipient’s system was infected with malware or adware and that they should call the number given on the pop-up screen and not restart the computer. Fortunately, he or she was suspicious of the legitimacy of the pop-up, not least because they don’t use the product in question.
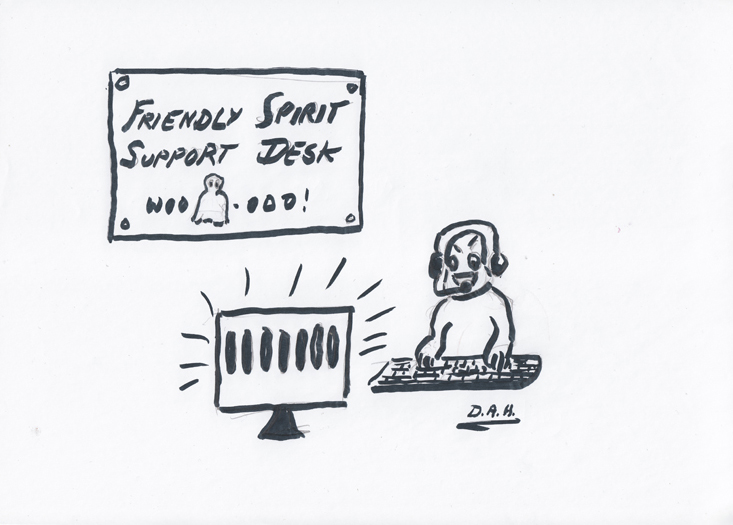
The recipient was subsequently able to send us the screenshot below. The message appears to be from McAfee, but of course it isn’t. Scammers, malware authors, purveyors of fake security software and the rest are all too ready to pass themselves off as legitimate security companies. After all, damaging the reputation of companies whose products detect malicious software and links is a welcome bonus for the malevolent. In fact my introduction to the wacky world of support scams came about because a colleague from another company reported a deceptive cold-call from someone claiming to represent ESET in some way. Looking at more recent support scamming, I don’t have a screenshot of a fake ESET alert, but I’ve seen several that pass themselves off as being from Norton/Symantec, AVG, and many that claim to be from Microsoft Security Essentials, Windows Defender or even Windows Firewall.
Fake alert passed off as being from McAfee
One of the reasons this particular example is so interesting is that it’s the sort of thing we’ve been seeing targeting OS X/iOS/Android users, but of course there was never any reason it shouldn’t be used against Windows users, and since seeing this example I’ve come across plenty that are.
Masquerades and Mailboxes
However, it’s not all about masquerading as first-tier security vendors. Other organizations whose brands are misused by support scammers include providers such as Gmail, Yahoo and BT. It’s not all Windows either: we’re seeing pop-ups and fake alerts that essentially take the same approach, but are targeting users of OS X, iOS and Android. Sometimes the message is claimed to be a browser alert message (as you might expect, Safari is frequently specified, and other Mac browsers are not spared).
Besides the scam pop-ups, there are many sites that simply claim to offer various types of 24/7 ‘help’ and ‘support’ for systems ranging from Windows (of course) to Macs to smartphones and tablets, even for Kindles, printers and routers. In general, these are pages waiting passively for someone to find them, perhaps having been directed by scam pop-ups or cold calls, or perhaps by using a search engine in the hope of finding help with a genuine problem. Typically, they offer help via a toll-free number with diagnostics, virus removal (of course), setup, networking and (of course) optimization. They may offer services directly related to specific products and brands such as Adobe, AOL, specific browsers and mail services, and so on.
Walking the Plank
Many offer generic ‘antivirus’ help (it’s curious how scammers are still hung up on self-replicating malware when the real security industry waxes quite nostalgic about the viruses it hardly ever sees any more), some offer ‘help’ for a single big-name brand, while others offer multiple links for individual products.
But where can you go on the web that’s safe from this kind of pop-up? Unfortunately, they may appear while you’re passing by the most surprising sites, though Darren Pauli’s article for The Register suggests that one site worth avoiding is a well-known pirate torrent site where there are reports of fake Blue Screens of Death (BSODs).
But I thought it would be interesting (and maybe even useful) to take a look at some typical pop-ups to see if we can isolate some typical features, pour cold water on some of the more extreme scaremongering, and perhaps enjoy a little comic relief. In fact, especially for the comic relief.
Blue Screen Blues
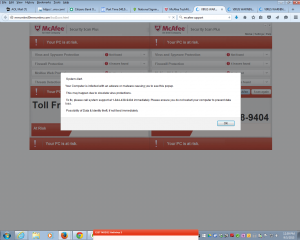
Here’s a typical fake BSOD warning. The error is, of course, mythical, though it probably looks convincing to a non-techie (apart from the misspelling of TECHNICIANSS – a serpentine hint of the Disney version of Kaa, there, perhaps J). Let’s be clear: a true Windows BSOD is not going to give you a convenient (for the scammer) toll-free number to call. The really instructive content is in the panel on the left, though.
Firstly, the message appears to come ‘from webpage’. Who would have guessed that so many web pages are able and willing to check a visitor’s system for malware, and even to diagnose ‘…a .net frame work file missing due to some harmful virus’? Even more interesting are the repeated (ad nauseam) warnings not to open a browser or shut down/restart the system, but to contact ‘microsoft technicians’ [sic] immediately. Of course, this has nothing to do with avoiding corruption to the Registry, data loss, or catastrophic failure of the operating system leading to an inability to reboot. It’s to stop the victim realizing that the system is actually working as usual (somewhat unusual in a BSOD situation) and should reboot quite normally.
Jérôme Segura, who’s done a lot of useful work in researching and reporting support scammers, cites an instance where the scammers used Malvertising Via Google AdWords to lure victims towards a somewhat similar error message/malicious site, but they are, frankly, all over the place.
You may also note that this (and most of the other screenshots displayed here) are referring potential victims to toll-free numbers apparently in the US.
Androids and Ectoplasm
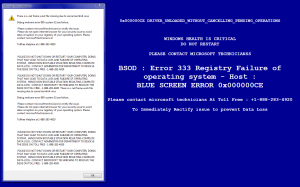
Here’s one for Android users.
Well, I know that Google/Android isn’t/aren’t very keen on anti-malware companies, and in any case there is apparently no Android malware, but I don’t know how the company feels about using a medium to scan for viruses. Should we all join hands and wait for a spirit guide? Hit the scammers with an Ouija board? And who would have believed that ectoplasm could have such a devastating effect on a SIM card? (And, if you’ll forgive me putting on my editorial hat for a moment, doesn’t destruction imply a certain amount of damage by definition?) This actually reminds me of the hoax virus that was supposed to eat the coating off hard disk platters. But that’s enough nostalgia.
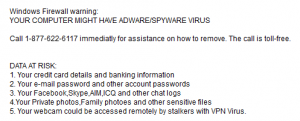
Here’s one that is fractionally lighter on the panic pedal, claiming to be generated by the Windows firewall:
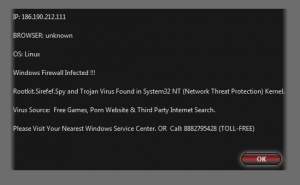
Well, we should be concerned about some of these risks, though ‘stalkers with VPN Virus’ is sheer technobabble. But don’t underestimate the Windows Firewall. Apparently, not only does it know about adware and spyware, but it can warn you about threats affecting Linux:
The threat-name is interesting, managing to combine the sinister-sounding rootkit and spyware threat-types with the real threat-name Sirefef. In fact, this generation of scammers seems rather fond of using Sirefef to frighten us with. But who knew that Linux distros used the NT Kernel? (More technobabble, meant to impress and confuse the technologically-challenged.) That’ll teach us all to mess with free games, porn sites, and search engines.
Stalked by a Web Site
How do these miraculous pop-ups know that our systems are under threat, apart from using the mythical Network Threat Protection Kernel? Why, by detecting ‘suspicious’ (or in one case ‘anonymous’) activity. One somewhat linguistically-challenged example refers to ‘Suspicious activity of intrusions detected which is trying to redirect you to an attack site.’ Apparently ‘This may happen due to obsolete virus protections.’ Let that be a warning to you, and keep your ESET products updated. 😉 Another warns that your system is running slowly because of unwanted programs, Rootkit.malware and Trojan.malware. Scary. By comparison, those that diagnose ‘a major security glitch’ sound almost cuddly. A scam aimed at iGadget users claims that iOS has crashed due to ‘third party application in your phone’.
There is some clever software out there, though. One program knows that our devices are ‘infected dangerously’ even before it ‘scans’.
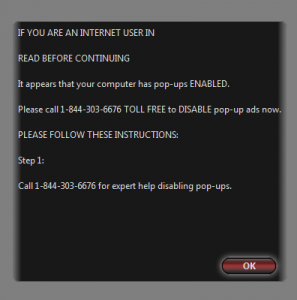
But the screenshot below is my favourite of favourites. (Apart from the one that recommends contacting a Microsoft Certified Live Technician: much better than contacting a dead one, with the resulting risk to your SIM card from aggressive ectoplasm.)
While the whole support scam ethos is reminiscent of a protection racket, this particular example demonstrates breathtaking chutzpah. ‘Call us to get your pop-ups disabled and you’ll never hear from us again. Because you won’t be able to see our pop-ups.’ Yeah, I bet.
Conclusion
To change our own angle of attack slightly, I noticed recently a comment to one of my ESET articles, which may be of some interest. (I discussed it in more detail on the AVIEN blog, but the comment is one of nearly 500 attached to this article: Support desk scams: CLSID not unique.)
I know these are scams, and I work in IT, but I had only heard these stories from my mom about them calling her. I wondered if this was a scam targeting older people, since I had never been called. Now they have started calling.
While these scammers certainly seem more than happy to defraud older people, probably because they expect them to be less conversant with technology and therefore likelier to fall for the pitch, I doubt if the cold calls are, in general, specifically targeting my generation: not because of the guilt factor, but because it would take more research than simply working through a directory of residential numbers.
I string him along for a little bit when I finally tell him, politely, that I know this is BS. At first he denies it, then he actually acknowledges it, acknowledges that he is in Calcutta. Tells me a little about his family, and that he is in school. Tells me that work is hard to find, and asks if it’s as hard here as it is there. He tells me that the scam jobs make 14,000 a year, but the legit ones that he can find only make 7,500 a year. At the end of the call, he thanked me for not yelling and screaming profanities at him. Overall I was on the phone for 40 minutes and 20 of that was after I told him I knew.
My friend and former colleague Craig Johnston recounted a similar encounter in Virus Bulletin back in 2011, which he also talked about in our joint presentation at Virus Bulletin with Steve Burn and Martijn Grooten. As Craig said, ‘While the caller admitted that the methods used to convince the ‘customer’ were dodgy, he was keen to assure me that the product being sold was legitimate and that it would benefit the customer.’
We’ve long known that in some cases at least, the scam calls are coming from call centres that also provide legitimate support services: in one case, one of ESET’s competitors changed its support model when the call-centre in India to which it had outsourced support services turned out to be using the same cold-call scamming techniques that I’ve described so often here.
I’ve talked before about scammer motivation, and my research and speculations haven’t inspired me to greater admiration of the breed, but apparently not all support scammers are bullies and worse (like the unspeakable monsters who try to block their victim’s access to their own systems if they allow the scammer access and then decide not to purchase his ‘services’). Some may even have the grace to be less than proud of the way they make their living. It is, I guess, understandable that some people will compromise their principles in order to keep their jobs, knowing how easily they can be replaced.
Footnote
As ever, I’d like to acknowledge the insight and practical help of Steve Burn, without whose knowledge and persistence in tracking the perpetrators we’d know a lot less about this type of scam. I’d also like to draw your attention to some excellent and very informative articles by Jérôme Segura on these and other types of scam. I’ll also mention once more the AVIEN resource page.