Search results for "Injection"
-
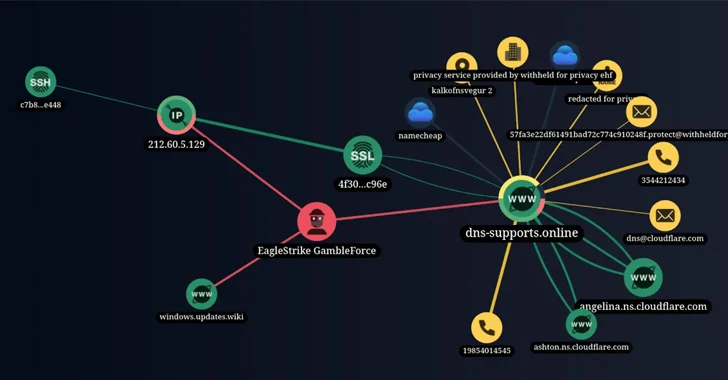
 2.3KVulnerabilities
2.3KVulnerabilitiesNew Hacker Group ‘GambleForce’ Tageting APAC Firms Using SQL Injection Attacks
A previously unknown hacker outfit called GambleForce has been attributed to a series of SQL injection attacks against companies primarily in the...
-

 4.8KTutorials
4.8KTutorialsHow to Bypass EDRs, AV with Ease using 8 New Process Injection Attacks
In the ever-evolving landscape of cybersecurity, researchers are continually uncovering new methods that challenge existing defense mechanisms. A recent study by SafeBreach,...
-
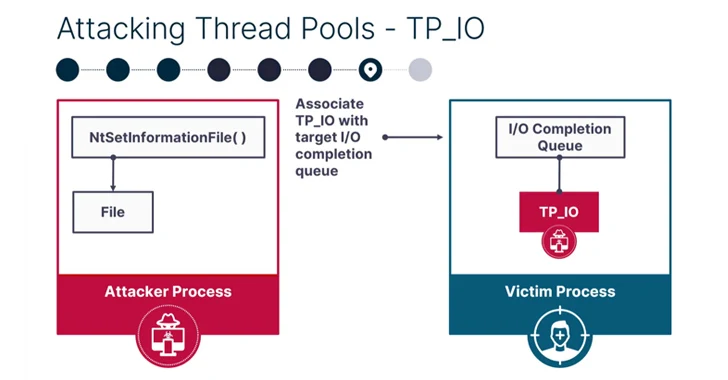
 4.2KMalware
4.2KMalwareNew PoolParty Process Injection Techniques Outsmart Top EDR Solutions
A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while...
-
 1.0KData Security
1.0KData Security“Prompt injection”attack allows hacking into LLM AI chatbots like ChatGPT, Bard
A kind of attack known as prompt injection is directed against LLMs, which are the language models that are the driving force...
-

 3.4KData Security
3.4KData SecurityHacking PostgreSQL applications with a SQL Injection vulnerability
Those that work with databases on a regular basis will know that PostgreSQL is more than just a name. It has an...
-
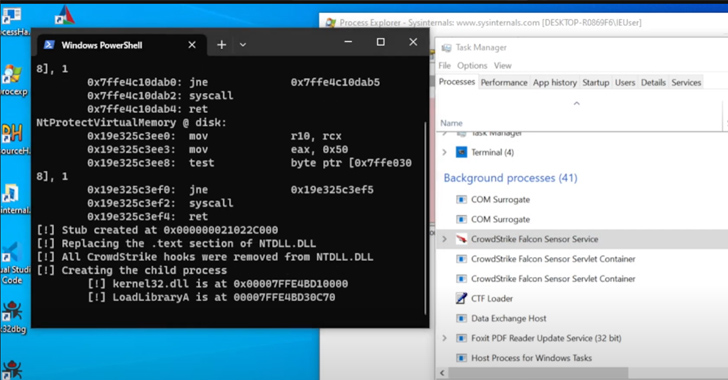
 3.7KMalware
3.7KMalwareNew Mockingjay Process Injection Technique Could Let Malware Evade Detection
A new process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on...
-

 1.1KVulnerabilities
1.1KVulnerabilitiesCritical Flaw in Cisco IP Phone Series Exposes Users to Command Injection Attack
Cisco on Wednesday rolled out security updates to address a critical flaw impacting its IP Phone 6800, 7800, 7900, and 8800 Series...
-
 5.0KMalware
5.0KMalwareParallax RAT Targeting Cryptocurrency Firms with Sophisticated Injection Techniques
Cryptocurrency companies are being targeted as part of a new campaign that delivers a remote access trojan called Parallax RAT. The malware...
-

 608Malware
608MalwareRansomware gangs are exploiting Fortinet Devices vulnerabilities. Patch these high-severity command injection flaws
Fortinet, a company that develops next-generation firewalls, VPNs, antivirus, and endpoint solutions, among other products, issued a public security advisory on October...
-

 3.6KData Security
3.6KData SecurityNew JSON-Based SQL Injection attacks allow bypassing Palo Alto, F5, AWS, Cloudflare, and Imperva WAF
Web application firewalls, also known as WAFs, are intended to protect web-based applications and application programming interfaces (APIs) from malicious HTTPS traffic...
-

 4.4KVulnerabilities
4.4KVulnerabilitiesCritical SonicWall Vulnerability Allows SQL Injection – Patch Now!
A critical SQL injection (SQLi) vulnerability was recently patched by the network security company SonicWall as a result of a new update. ...
-

 4.0KVulnerabilities
4.0KVulnerabilitiesCritical (CVSS 9.4) SQL Injection vulnerability in SonicWall GMS & SonicWall Analytics On-Prem
SonicWall has published a hotpatch to fix two SQL injection vulnerabilities impacting the GMS (Global Management System) and Analytics On-Prem products. CVE-2022-22280...
-
 2.4KVulnerabilities
2.4KVulnerabilitiesCritical SQL injection vulnerability in Django
The Django project, an open source web framework based on Python, has fixed a high severity vulnerability in its latest versions. Identified...
-

 1.6KVulnerabilities
1.6KVulnerabilitiesTwo critical command injection vulnerabilities in Fujitsu cloud storage system allow remote encryption or deletion of files
Two bugs in the web interface of a Fujitsu cloud storage system would allow authenticated threat actors to read, write, and even...
-

 2.8KVulnerabilities
2.8KVulnerabilitiesZyxel Releases Patch for Critical Firewall OS Command Injection Vulnerability
Zyxel has moved to address a critical security vulnerability affecting Zyxel firewall devices that enables unauthenticated and remote attackers to gain arbitrary...
-

 1.4KVulnerabilities
1.4KVulnerabilitiesCVE-2022-0757: Rapid7 Nexpose SQL injection vulnerability, also known as security console: Patch immediately
Rapid7 security teams announced the fix of a critical SQL injection vulnerability in Nexpose, a popular local vulnerabilities management software. The flaw...
-

 3.8KVulnerabilities
3.8KVulnerabilitiesCritical code injection vulnerabilities in VMware Spring Cloud Gateway
Cybersecurity specialists report the detection of two vulnerabilities in VMware Spring Cloud Gateway, a library for creating API gateways over Spring and...
-

 300Vulnerabilities
300VulnerabilitiesVMware Issues Patches for Shell Injection and Privilege Vulnerability
VMware had multiple issues that were privately reported. VMware swiftly acted on the reported issues and released patches for all the critical...
-

 4.0KMalware
4.0KMalwareTrickBot Malware Using New Techniques to Evade Web Injection Attacks
The cybercrime operators behind the notorious TrickBot malware have once again upped the ante by fine-tuning its techniques by adding multiple layers...
-
 1.8KVulnerabilities
1.8KVulnerabilitiesTwo critical SQL injection vulnerabilities in Philips Tasy EMR, used by hospitals worldwide
Cybersecurity specialists report the detection of two critical vulnerabilities in Philips Tasy EMR, a medical record and health services management tool. Tracked...
-

 3.5KVulnerabilities
3.5KVulnerabilitiesCVE-2021-3723: Unpatched command injection vulnerability affects IBM system x3550 M3 and IBM System x 3650 M3
Cybersecurity experts report that two legacy IBM System x server models recalled in 2019 are exposed to multiple attack variants due to...






