Search results for "Research"
-

 1.2KVulnerabilities
1.2KVulnerabilitiesResearchers Discover LG Smart TV Vulnerabilities Allowing Root Access
Multiple security vulnerabilities have been disclosed in LG webOS running on its smart televisions that could be exploited to bypass authorization and...
-

 1.9KVulnerabilities
1.9KVulnerabilitiesResearchers Detail Kubernetes Vulnerability That Enables Windows Node Takeover
Details have been made public about a now-patched high-severity flaw in Kubernetes that could allow a malicious attacker to achieve remote code...
-
 341Vulnerabilities
341VulnerabilitiesHow Nation-State Actors Target Your Business: New Research Exposes Major SaaS Vulnerabilities
With many of the highly publicized 2023 cyber attacks revolving around one or more SaaS applications, SaaS has become a cause for...
-
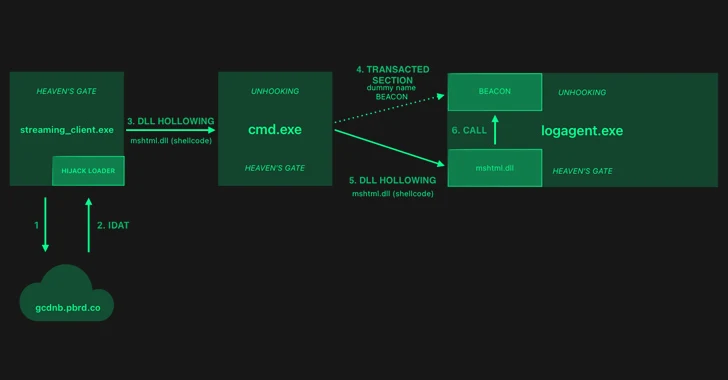
 1.8KMalware
1.8KMalwareHijackLoader Evolves: Researchers Decode the Latest Evasion Methods
The threat actors behind a loader malware called HijackLoader have added new techniques for defense evasion, as the malware continues to be...
-
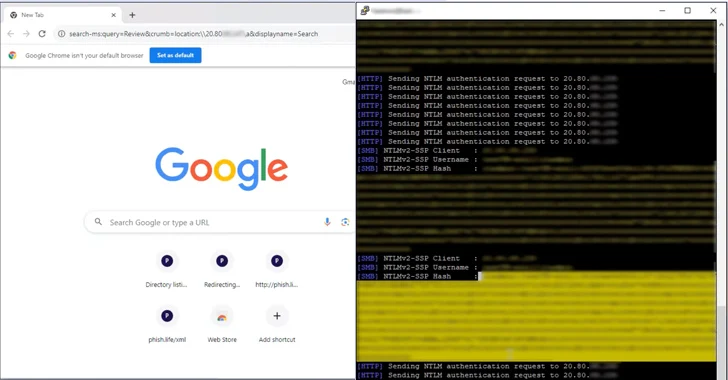
 2.3KVulnerabilities
2.3KVulnerabilitiesResearchers Uncover How Outlook Vulnerability Could Leak Your NTLM Passwords
A now-patched security flaw in Microsoft Outlook could be exploited by threat actors to access NT LAN Manager (NTLM) v2 hashed passwords...
-

 878Malware
878MalwareNorth Korean Hackers Weaponize Research Lures to Deliver RokRAT Backdoor
Media organizations and high-profile experts in North Korean affairs have been at the receiving end of a new campaign orchestrated by a...
-
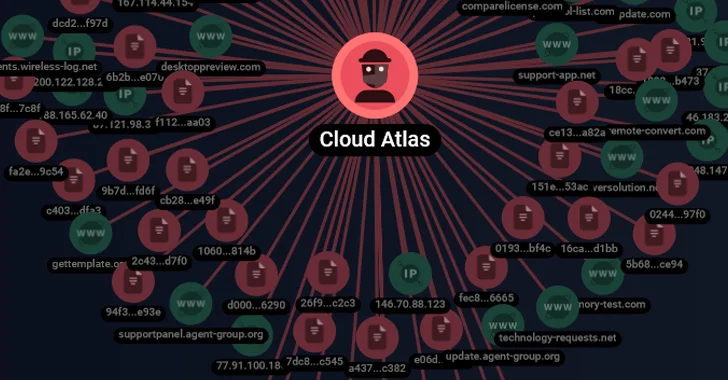
 834Malware
834MalwareCloud Atlas’ Spear-Phishing Attacks Target Russian Agro and Research Companies
The threat actor referred to as Cloud Atlas has been linked to a set of spear-phishing attacks on Russian enterprises. Targets included...
-

 3.4KMalware
3.4KMalwareResearchers Unmask Sandman APT’s Hidden Link to China-Based KEYPLUG Backdoor
Tactical and targeting overlaps have been discovered between the enigmatic advanced persistent threat (APT) called Sandman and a China-based threat cluster that’s...
-

 3.9KMalware
3.9KMalwareResearchers Unveal GuLoader Malware’s Latest Anti-Analysis Techniques
Threat hunters have unmasked the latest tricks adopted by a malware strain called GuLoader in an effort to make analysis more challenging....
-

 4.5KMalware
4.5KMalwareResearchers Find 34 Windows Drivers Vulnerable to Full Device Takeover
As many as 34 unique vulnerable Windows Driver Model (WDM) and Windows Driver Frameworks (WDF) drivers could be exploited by non-privileged threat...
-
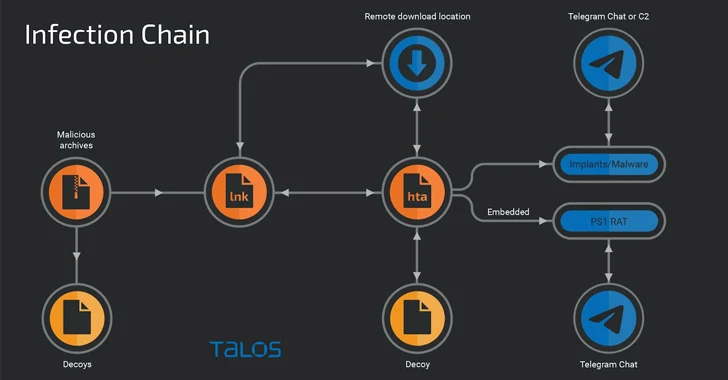
 4.5KMalware
4.5KMalwareYoroTrooper: Researchers Warn of Kazakhstan’s Stealthy Cyber Espionage Group
A relatively new threat actor known as YoroTrooper is likely made up of operators originating from Kazakhstan. The assessment, which comes from...
-

 1.9KMalware
1.9KMalwareResearchers Unveil ToddyCat’s New Set of Tools for Data Exfiltration
The advanced persistent threat (APT) actor known as ToddyCat has been linked to a new set of malicious tools that are designed...
-
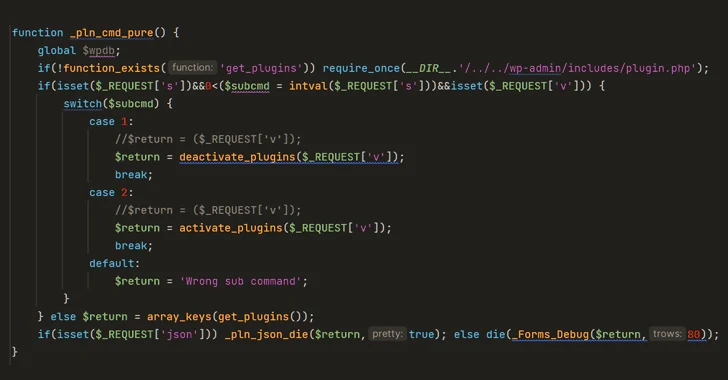
 1.2KMalware
1.2KMalwareResearchers Uncover Malware Posing as WordPress Caching Plugin
Cybersecurity researchers have shed light on a new sophisticated strain of malware that masquerades as a WordPress plugin to stealthily create administrator...
-

 4.4KCyber Attack
4.4KCyber AttackResearchers Uncover Ongoing Attacks Targeting Asian Governments and Telecom Giants
High-profile government and telecom entities in Asia have been targeted as part of an ongoing campaign since 2021 that’s designed to deploy...
-

 557Malware
557MalwareResearchers Uncover Grayling APT’s Ongoing Attack Campaign Across Industries
A previously undocumented threat actor of unknown provenance has been linked to a number of attacks targeting organizations in the manufacturing, IT,...
-

 4.8KVulnerabilities
4.8KVulnerabilitiesNorth Korean Hackers Exploit Zero-Day Bug to Target Cybersecurity Researchers
Threat actors associated with North Korea are continuing to target the cybersecurity community using a zero-day bug in an unspecified software over...
-
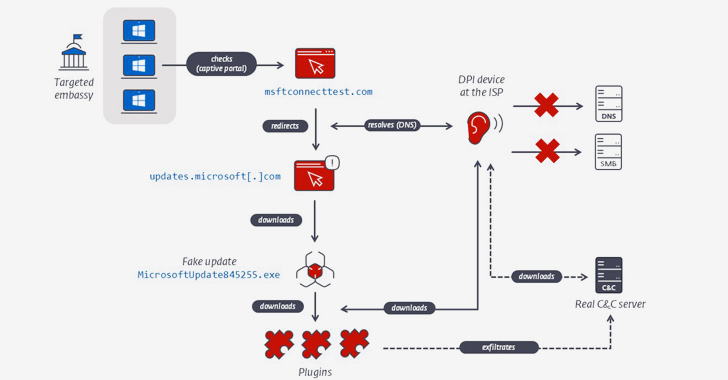
 4.7KCyber Attack
4.7KCyber AttackResearchers Uncover Years-Long Cyber Espionage on Foreign Embassies in Belarus
A hitherto undocumented threat actor operating for nearly a decade and codenamed MoustachedBouncer has been attributed to cyber espionage attacks aimed at...
-

 1.2KRansomware
1.2KRansomwareResearchers Uncover Series of Ransomware Attacks that Follow Same Pattern
Ransomware groups often recycle tools, techniques, and procedures. Even some of them also provide playbooks for affiliates as well. Numerous use Cobalt...
-

 1.6KData Security
1.6KData SecurityResearchers find a way to get unlimited airlines miles and hotels nights for free
The benefits of joining a particular club over others are highlighted in travel rewards programs like those run by airlines and hotels....
-

 2.8KCyber Attack
2.8KCyber AttackResearchers Expose Space Pirates’ Cyber Campaign Across Russia and Serbia
The threat actor known as Space Pirates has been linked to attacks against at least 16 organizations in Russia and Serbia over...
-

 4.7KCyber Attack
4.7KCyber AttackPatchwork Hackers Target Chinese Research Organizations Using EyeShell Backdoor
Threat actors associated with the hacking crew known as Patchwork have been spotted targeting universities and research organizations in China as part...






