Search results for "Vulnerability"
-

 1.8KVulnerabilities
1.8KVulnerabilitiesPalo Alto Networks Releases Urgent Fixes for Exploited PAN-OS Vulnerability
Palo Alto Networks has released hotfixes to address a maximum-severity security flaw impacting PAN-OS software that has come under active exploitation in...
-

 3.2KVulnerabilities
3.2KVulnerabilitiesFortinet Rolls Out Critical Security Patches for FortiClientLinux Vulnerability
Fortinet has released patches to address a critical security flaw impacting FortiClientLinux that could be exploited to achieve arbitrary code execution. Tracked...
-

 4.3KVulnerabilities
4.3KVulnerabilitiesCritical ‘BatBadBut’ Rust Vulnerability Exposes Windows Systems to Attacks
A critical security flaw in the Rust standard library could be exploited to target Windows users and stage command injection attacks. The...
-

 1.4KVulnerabilities
1.4KVulnerabilitiesNew HTTP/2 Vulnerability Exposes Web Servers to DoS Attacks
New research has found that the CONTINUATION frame in the HTTP/2 protocol can be exploited to conduct denial-of-service (DoS) attacks. The technique...
-

 2.0KVulnerabilities
2.0KVulnerabilitiesCritical Unpatched Ray AI Platform Vulnerability Exploited for Cryptocurrency Mining
Cybersecurity researchers are warning that threat actors are actively exploiting a “disputed” and unpatched vulnerability in an open-source artificial intelligence (AI) platform...
-

 4.4KVulnerabilities
4.4KVulnerabilitiesNew “GoFetch” Vulnerability in Apple M-Series Chips Leaks Secret Encryption Keys
A new security shortcoming discovered in Apple M-series chips could be exploited to extract secret keys used during cryptographic operations. Dubbed GoFetch,...
-

 2.6KVulnerabilities
2.6KVulnerabilitiesIvanti Releases Urgent Fix for Critical Sentry RCE Vulnerability
Ivanti has disclosed details of a critical remote code execution flaw impacting Standalone Sentry, urging customers to apply the fixes immediately to...
-

 4.4KVulnerabilities
4.4KVulnerabilitiesFortra Patches Critical RCE Vulnerability in FileCatalyst Transfer Tool
Fortra has released details of a now-patched critical security flaw impacting its FileCatalyst file transfer solution that could allow unauthenticated attackers to...
-

 1.9KVulnerabilities
1.9KVulnerabilitiesResearchers Detail Kubernetes Vulnerability That Enables Windows Node Takeover
Details have been made public about a now-patched high-severity flaw in Kubernetes that could allow a malicious attacker to achieve remote code...
-

 749Vulnerabilities
749VulnerabilitiesFortinet Warns of Severe SQLi Vulnerability in FortiClientEMS Software
Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected...
-

 1.5KVulnerabilities
1.5KVulnerabilitiesProof-of-Concept Exploit Released for Progress Software OpenEdge Vulnerability
Technical specifics and a proof-of-concept (PoC) exploit have been made available for a recently disclosed critical security flaw in Progress Software OpenEdge...
-

 2.3KVulnerabilities
2.3KVulnerabilitiesCISA Warns of Actively Exploited JetBrains TeamCity Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting JetBrains TeamCity On-Premises software to its...
-
 5.1KVulnerabilities
5.1KVulnerabilitiesWordPress LiteSpeed Plugin Vulnerability Puts 5 Million Sites at Risk
A security vulnerability has been disclosed in the LiteSpeed Cache plugin for WordPress that could enable unauthenticated users to escalate their privileges....
-

 1.2KVulnerabilities
1.2KVulnerabilitiesNew Hugging Face Vulnerability Exposes AI Models to Supply Chain Attacks
Cybersecurity researchers have found that it’s possible to compromise the Hugging Face Safetensors conversion service to ultimately hijack the models submitted by...
-

 2.8KVulnerabilities
2.8KVulnerabilitiesWordPress Plugin Alert – Critical SQLi Vulnerability Threatens 200K+ Websites
A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate Member that has more than 200,000 active installations....
-
 2.2KMalware
2.2KMalwareDarkMe Malware Targets Traders Using Microsoft SmartScreen Zero-Day Vulnerability
A newly disclosed security flaw in the Microsoft Defender SmartScreen has been exploited as a zero-day by an advanced persistent threat actor...
-

 368Vulnerabilities
368VulnerabilitiesIvanti Vulnerability Exploited to Install ‘DSLog’ Backdoor on 670+ IT Infrastructures
Threat actors are leveraging a recently disclosed security flaw impacting Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy a backdoor...
-

 3.2KData Security
3.2KData SecurityHacking Debian, Ubuntu, Redhat& Fedora servers using a single vulnerability in 2024
The recent discovery of a significant flaw in the GNU C Library (glibc), a fundamental component of major Linux distributions, has raised...
-

 1.1KVulnerabilities
1.1KVulnerabilitiesCISA Warns of Active Exploitation Apple iOS and macOS Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a high-severity flaw impacting iOS, iPadOS, macOS, tvOS, and watchOS to...
-

 685Data Security
685Data SecurityExploit code: How the New Jenkins Vulnerability Could Compromise Your Data
Recent news about a critical vulnerability in Jenkins, identified as CVE-2024-23897, has raised significant concerns in the cybersecurity community. This vulnerability has...
-
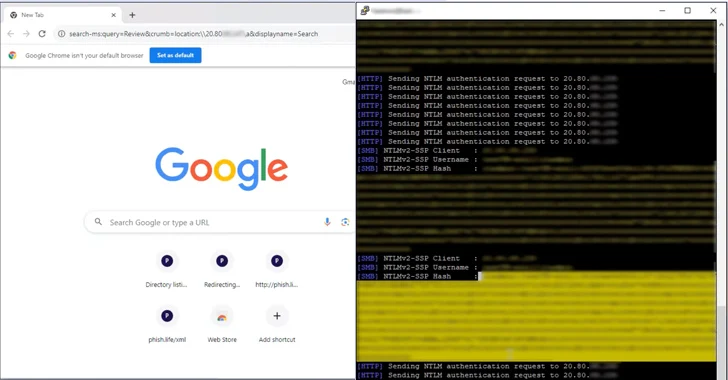
 2.3KVulnerabilities
2.3KVulnerabilitiesResearchers Uncover How Outlook Vulnerability Could Leak Your NTLM Passwords
A now-patched security flaw in Microsoft Outlook could be exploited by threat actors to access NT LAN Manager (NTLM) v2 hashed passwords...






