The IT security researchers at Kaspersky Labs have identified that hackers have launched a new campaign against financial organizations where they can access their infrastructure and keep accessing it for an extended period without getting detected to understand the internal processes for stealing cash.
Through exploiting the system for a longer duration, hackers can easily detect and learn the behavior of financial firms. The malware was discovered in September, and it was identified in the networks of banks from Malaysia, Armenia, and Russia. However, researchers believe that attackers will most likely extend the attack’s scope to other locations.
“The analysis of this case provides us with a new Trojan, apparently being used in multiple international locations, which suggests it is an expanding activity of the group. The Trojan provides monitoring capabilities similar to the ones used by the Carbanak group,” read the blog post from Kaspersky researchers.
The Trojan has been dubbed as “Silence” because of the way it attacks. The hackers responsible for launching Silence start their malicious operation by firstly compromising some of the machines at their targeted firm. The methods with which the hackers compromise the machines is yet unknown. The objective is to gain access to employee email accounts.
The second step is to exploit the compromised accounts to send phishing emails to other employees. Thus, a multi-stage attack is launched. Attackers using Silence use phishing emails as initial infection vectors using addresses of employees from an organization that already has been attacked while the email contains a request to open an account on the affected bank. The message is created using a standard social engineering trick and seems legit.
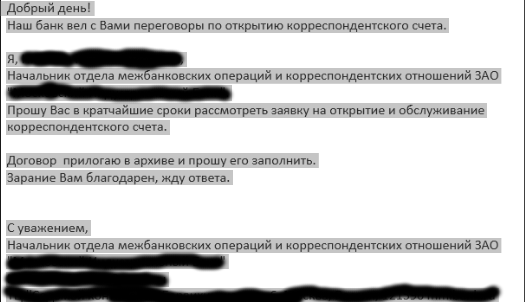
Phishing email in Russia language (Credit: Kaspersky)
Kaspersky Lab researchers noticed that the rogue emails contain Microsoft Compiled HTML Help (CHM) files. This means hackers have embedded malicious coding in CHM files. When the recipient of the email finds and opens the infected CHM file, it executes a rogue JavaScript code. After which a malicious VBS script is downloaded from a URL.
It is then launched to install malware dropper to connect with the C&C server to download multiple payloads, which serve as modules with different functionalities such as one module captures screenshots from the victim’s desktop and creates a real-time video stream for attackers to track employee’s activity. Similarly, the other module lets attackers execute Windows Shell commands.
[q]Silence Malware Targeting Financial Institutions In Russia, Malaysia, and Armenia[/q]
Attackers using Silence use phishing emails as initial infection vectors using addresses of employees from an organization that already has been attacked while the email contains a request to open an account on the affected bank. The message is created using a standard social engineering trick and seems legit.
“This kind of attack has become widespread in recent years. The spear-phishing infection vector is still the most popular way to initiate targeted campaigns. When used with already compromised infrastructure, and combined with .chm attachments, it seems to be an effective way of spreading, at least among financial organizations,” noted researchers.
[fullsquaread][/fullsquaread]










