Our interim analysis of a version of the malware we detect as Java/Boonana.A or Win32/Boonana.A (depending on the particular component of this multi-binary attack) differs in some characteristics from other reports we’ve seen. The most dramatic difference is in the social engineering hook used in messages sent to an infected user’s friends list. Other reports
Our interim analysis of a version of the malware we detect as Java/Boonana.A or Win32/Boonana.A (depending on the particular component of this multi-binary attack) differs in some characteristics from other reports we’ve seen.
The most dramatic difference is in the social engineering hook used in messages sent to an infected user’s friends list. Other reports (including Randy’s from a couple of days ago) have documented a version that takes the hackneyed “is this you in this video?” approach to tricking a user into clicking on a YouTube link.
This particularly ugly example, however, reads:
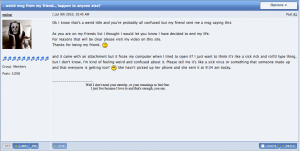
“As you are on my friends list I thought I would let you know I have decided to end my life. For reasons that will be clear please visit my video on this site. Thanks for being my friend. :(“
(Jerome Segura has also reported a similar message.)
As you can see from the screenshot above, illustrating this particular example of the social engineer’s art, this approach has been around for quite a while, though it hasn’t attracted the attention that I’d expect. In fact, examination of the binary header shows a compilation date of March 1st.
In this case it has been sent as an email attachment , rather than as a Facebook message.
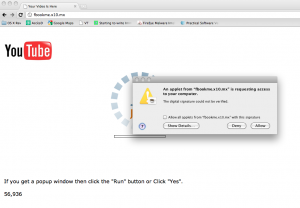
The follow-up to both messages, however, is as described in the earlier post. When the potential victim tries to run the “video”, a message is generated suggesting that the video can’t be watched without the installation of special software.
If the trick works, the Java applet runs happily on Windows or OS X: we can also confirm that it runs on Linux. For Windows systems, however, a registry entry is added, while for OS X files are copied to /Library/StartupItems and a script called OSXUpdates is created. It occurs to me that the mechanism is a little like the cross platform macro viruses of the mid-90s and later, which generally infected Macs as easily as Windows PCs, though the payloads were usually Windows-specific. In this case, though, the target is the user, not the platform. As I’ve said elsewhere:
This is very much social engineering-focused malware: its initial attack is on the user, not on the platform, and it isn’t self-launching in the first instance. If you smell a rat when you get the authorise install prompt, the malware can’t change your system files so as to allow unflagged external access. Actually, most malware (Windows as well as OS X) relies partly or totally on conning the user into running a malicious application.
While the (intended) functionality is not dissimilar, the code doesn’t resemble Koobface particularly, which is why we haven’t used that name as an identifier.
When a computer is infected, it checks a list of 161 hostnames. For each host, the malware does a “HTTP HEAD” query for a file named applet_hosts.txt. When a host responds to the query, it usually sends a 300 redirect HTTP code which in turns points to a link that will be accessed by the malware. This behavior may be intended by the malware author, but the redirects could be caused by domain names that have been taken down over time: the list seems pre-date the current malware.
David Harley
Pierre-Marc Bureau