A recent research published by vulnerability testing specialists from Purdue University details a new exploit that abuses some Android operating system smartphones through the use of malicious peripheral devices (specifically through Bluetooth and USB).
The application processor of almost any
relatively recent smartphone model uses the AT Command Interface to launch
high-level commands to the baseband processor, which performs common cellular
network operations. There are vulnerabilities in this communication that can be
exploited by using peripheral devices controlled by threat actors.
Typically, a smartphone works with two
interconnected processing units:
- Application
processor - Baseband
processor (also called cellular modem)
It is important to mention that most current smartphones accept AT commands via Bluetooth.
The AT interface is an entry point for
accessing the baseband processor, so any anomalous behavior when processing any
AT command could cause unauthorized access to sensitive information stored on
the smartphone, alterations in the operation of the cellular network, among
other flaws.
SOURCE: ATFuzzer: Dynamic Analysis of AT Interface for Android
Some research previously conducted regarding
failures in the AT interface focuses only on finding invalid or malicious AT
commands for manufacturers to blacklist them and prevent possible abuse
behavior; however, vulnerability testing specialists consider the scope of this
approach to be really small, because although there are AT commands used by the
entire mobile communications industry, every single smartphone manufacturer
often include its own sets of AT commands to perform various tasks. In other
words, this approach is too specific.
Instead, experts propose to design a method of
analyzing processes related to the execution of any AT command to detect any
possible anomalous activity that may become an exploitable vulnerability.
Indicators of abnormal
activity:
- Syntactic
code errors: A device could accept invalid AT commands - Semantic
errors: Targeted devices process a properly grammar AT command, but the generated
response does not match to the expected behavior
When an invalid command gets exploited, a
malicious peripheral device connected to the targeted smartphone might access
sensitive information (such as IMSI key or IMEI), or even degrade the device’s
network protocol (4G to 3G, for example).
AT commands
These are code snippets used to control some tasks
related to cellular network usage. A basic set of commands was established as a
standard in the mobile communications industry; on the other hand, smartphone
manufacturers include their own AT commands to run multiple functions.
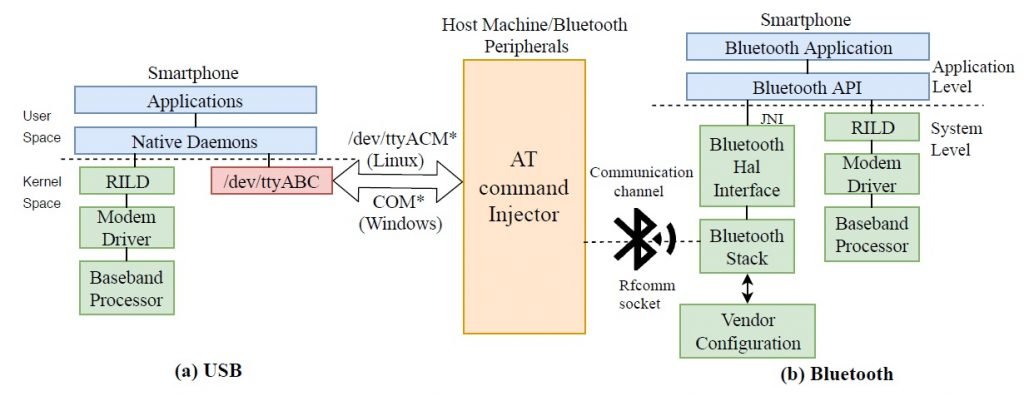
Running AT commands
via Bluetooth
It is required to pair the peripheral device
(speakers, headsets, etc.) with the targeted smartphone, establishing a
communication channel. When receiving an AT command the system-level Bluetooth
component of the device recognizes the command with the prefix “AT”
and contrasts it with a list of legitimate commands. The AT commands is then
sent to the Bluetooth component at the application level, where the action
related to the sent command is completed.

Running AT commands via USB
If a smartphone exposes its USB Abstract
Control Model (ACM) interface, it creates a tty device such as /dev/ttyACM0
that allows the phone to receive AT commands through the USB interface. On the
other hand, on phones for which the USB modem interface is not included in the
default USB configuration, switching to an alternate USB configuration allows
communication to the modem via USB.

For this research, a list of valid AT commands
and their grammar was obtained from 3GPP standards. Not all of these commands
are processed or recognized by all smartphones, as this depends on the
manufacturers.
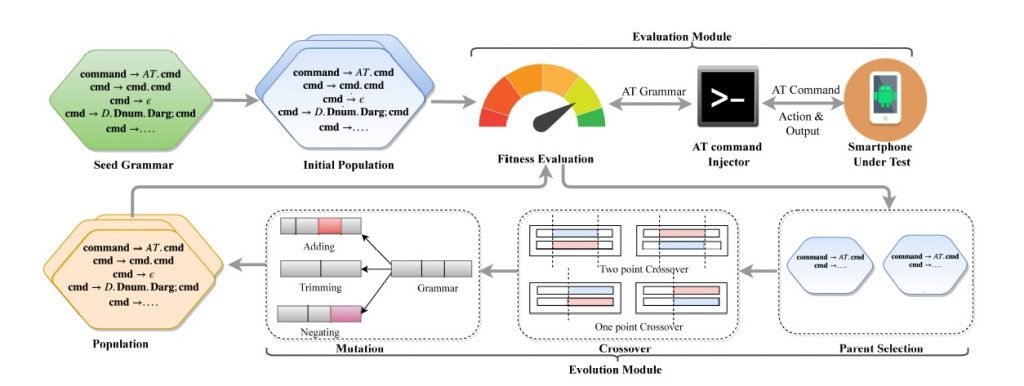
The ATFuzzer approach
ATFuzzer, the analysis method developed by the
researchers, consists of two modules: evolution module and evaluation module,
which interact in a closed way. The evolution module starts with an initial AT
command grammar that mutates to generate Psize (refers to population size, a
parameter for ATFuzzer), different versions of that grammar. Specifically,
ATFuzzer generates new grammars from the main grammar through the following
high-level operations:
- Population
initialization - Parent
select - Grammar
crossing - Grammatical
mutation
SOURCE: ATFuzzer: Dynamic Analysis of AT Interface for Android
To assess the effectiveness and scope of this
approach, 10 different models of Android operating system smartphones (from six
different manufacturers) were analyzed. Upon completion of the analysis,
vulnerability testing specialists discovered 4 misbehaviors in Bluetooth and 13
others on USB.
By exploiting these flaws, threat actors could
deploy malicious activities such as disruption of smartphone connections, denial
of service (DoS), and theft of sensitive information.
Although security for baseband processors and
command interfaces has improved markedly over previous generations of
smartphones, it is obvious that with current security measures it is impossible
to properly analyze and filter an anomalous input. According to the vulnerability
testing specialists from the International Institute of Cyber Security (IICS),
a possible solution to this improper access is the removal of exposure of the
AR modem interface via Bluetooth and USB. It’s also important to remind Android
device users to avoid connecting to chargers, speakers, or other unknown
peripherals.







