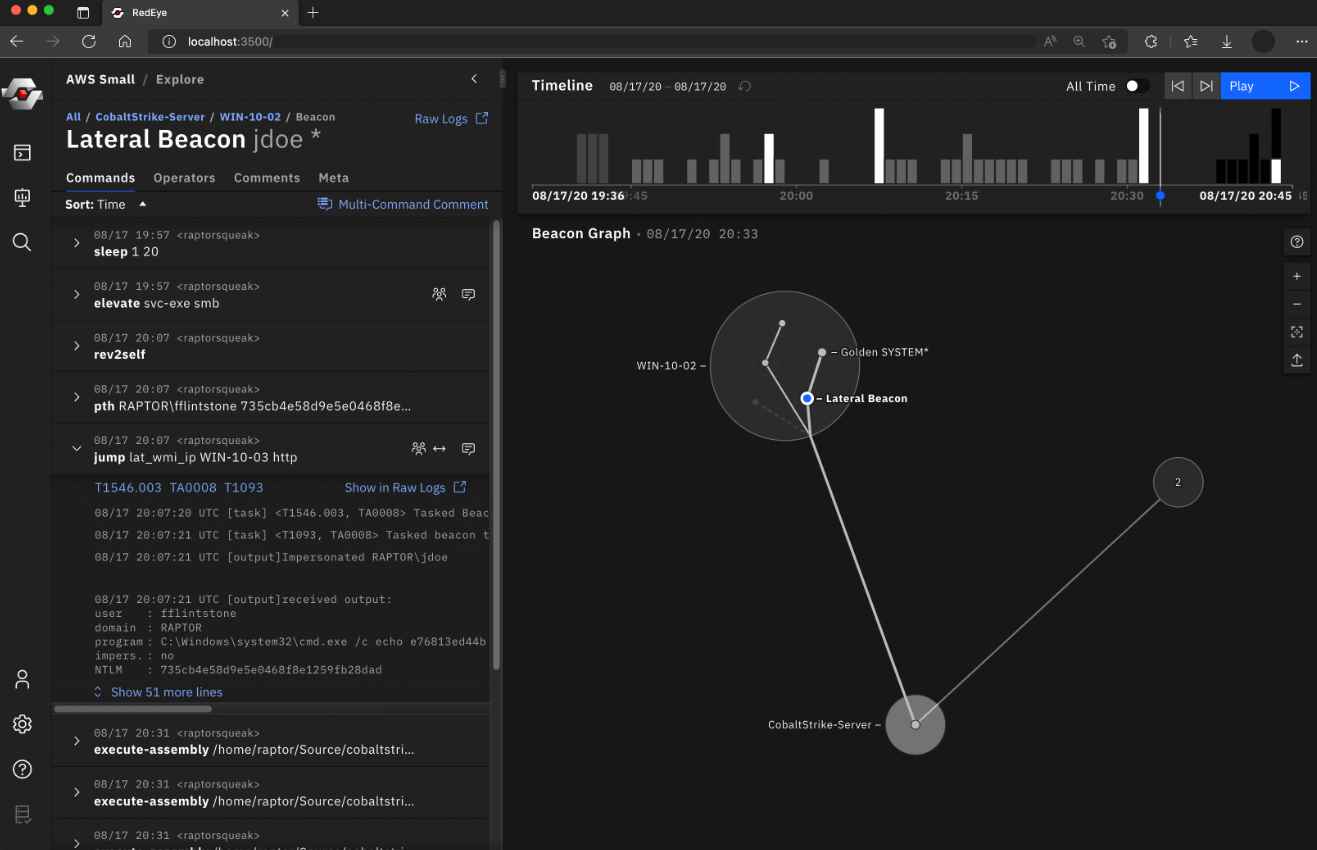
Packers are becoming an increasingly important tool for cybercriminals to use in the commission of illegal acts. On hacker forums, the packer is sometimes referred to as “Crypter” and “FUD.” Its primary function is to make it more difficult for antivirus systems to identify malicious code. Malicious actors are able to disseminate their malware more quickly and with fewer consequences when they use a packer. It doesn’t matter what the payload is, which is one of the primary qualities of a commercial Packer-as-a-Service, which implies that it may be used to pack a variety of different harmful samples. This opens up a lot of opportunities for cybercriminals. Another key quality of the packer is that it is transformational. Because the packer’s wrapper is changed on a frequent basis, it is able to avoid detection by devices designed to enhance security.
According to Checkpoint, TrickGate is an excellent illustration of a robust and resilient packer-as-a-service. It has been able to go under the radar of cyber security researchers for a number of years and is consistently becoming better in a variety of different ways.
Although a lot of very good study was done on the packer itself, TrickGate is a master of disguises and has been given a number of different titles due to the fact that it has so many different characteristics. A number of names have been given to it, including “TrickGate,” “Emotet’s packer,” “new loader,” “Loncom,” and “NSIS-based crypter.”
At the end of 2016, they made our first observation of TrickGate. During that time, it was used to spread the Cerber malware. Since that time, they have been doing ongoing research on TrickGate and have discovered that it is used to propagate many forms of malicious software tools, including ransomware, RATs, information thieves, bankers, and miners. It has come to their attention that a significant number of APT organizations and threat actors often employ TrickGate to wrap their malicious code in order to evade detection by security solutions. Some of the most well-known and top-distribution malware families have been wrapped by TrickGate, including Cerber, Trickbot, Maze, Emotet, REvil, CoinMiner, Cobalt Strike, DarkVNC, BuerLoader, HawkEye, NetWire, AZORult, Formbook, Remcos, Lokibot, AgentTesla, and many more. TrickGate has also been involved in the wrapping of many other malware.
There is tremendous room for variation in the first access made by the packer’s users. They keep an eye on the packed samples that are mostly propagating via phishing emails that include malicious attachments, as well as through malicious URLs.
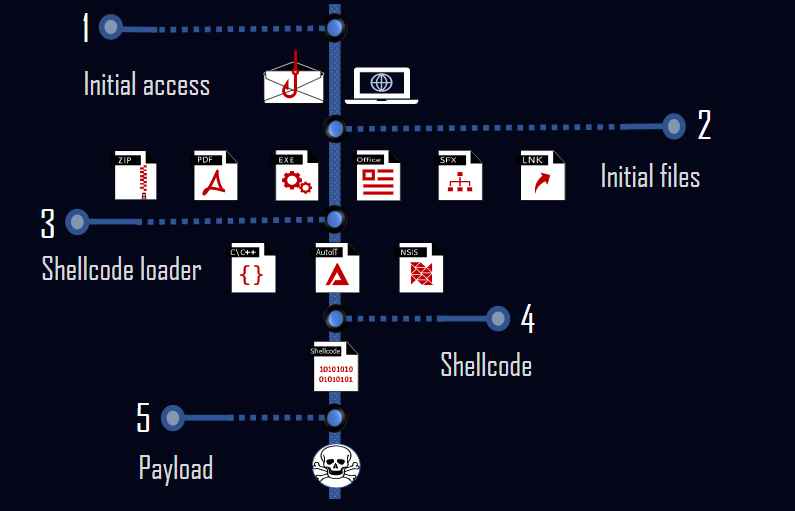
The shellcode loader is the second step, and it is this stage that is accountable for decrypting and executing the shellcode.
There were three distinct programming languages that were used for the shellcode loader, as they discovered. Similar functionality may be achieved via the use of NSIS script, AutoIT script, and C. The packer revolves on the shellcode as its central component. Deciphering the payload and then covertly inserting it into a new process is the responsibility of this component. The payload is the actual code that is harmful, and it is what is responsible for carrying out the action that was meant to be malicious. The payloads are distinct for each actor because of how they used the packer.
It is fascinating to see how TrickGate performs direct-syscalls since it employs a method that is similar to that of Hell’s Gate. Hell’s Gate is a method that was shown in public for the first time in the year 2020 as a mechanism to dynamically obtain and run direct syscall numbers.
They produced strings that correlate the most desired malware over the last six years to a single Packer-as-a-Service called TrickGate. TrickGate’s transformational skills make it difficult to detect and monitor, so they had to construct these strings. When trying to identify a danger, it is essential to have a solid understanding of the components that make up the packer. This is because stopping the packer will provide protection against the threat at an earlier stage, before the payload begins to run.
Researchers have a tendency to concentrate their attention on the actual malware, leaving the packer stub alone, which results in packers receiving less attention than they otherwise would. The detected packer, on the other hand, may now be used as a focus point in order to identify new or previously undisclosed forms of malware.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.