All posts tagged "CLI"
-

 928Exploitation Tools
928Exploitation ToolsMyJWT – A Cli For Cracking, Testing Vulnerabilities On Json Web Token (JWT)
This cli is for pentesters, CTF players, or dev. You can modify your jwt, sign, inject ,etc… Check Documentation for more...
-
 448Exploitation Tools
448Exploitation ToolsPenta – Open Source All-In-One CLI Tool To Automate Pentesting
Penta is is Pentest automation tool using Python3. (Future!) It provides advanced features such as metasploit and nexpose to extract vuln...
-

 236Geek
236GeekStrings Command In Linux: A Simple But Very Useful Tool
We all have to search through text files for strings from time to time. But what about when you need to search...
-

 241Geek
241Geek‘Cut’ Command In Linux: Useful Applications Explained
Linux and other UNIX-like operating systems have many tools for processing text on the command line. Without these tools (find complete Linux command...
-
 263Reverse Engineering
263Reverse EngineeringQBDI – QuarkslaB Dynamic binary Instrumentation
QuarkslaB Dynamic binary Instrumentation (QBDI) is a modular, cross-platform and cross-architecture DBI framework. It aims to support Linux, macOS, Android, iOS and...
-
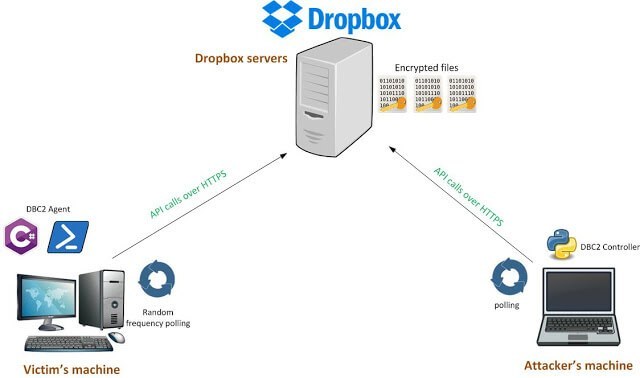
 282Post Exploitation
282Post ExploitationDBC2 (DropboxC2) – A Modular Post-Exploitation Tool, Composed Of An Agent Running On The Victim’S Machine
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine,...
-

 308Geek
308GeekThe Ultimate A To Z List of Linux Commands | Linux Command Line Reference
Short Bytes: Linux distributions can leverage an extensive range of commands to accomplish various tasks. For most Linux distros, Bash (bourne again...
-

 304Geek
304GeekLinux Lexicon — Input And Output With Pipes And Redirection In Linux
Short Bytes: Command output, and input, can be controlled in extremely flexible ways using pipes and redirection. This is much more than...
-
 318Geek
318GeekLinux Lexicon: Introduction To Linux Shell And Terminal | fossBytes
Last time we discussed the Linux Directory Structure and the roles of the various directories that form a part of the Linux...






