All posts tagged "Cloud security"
-

 1.4KData Breach
1.4KData BreachMuddled Libra Shifts Focus to SaaS and Cloud for Extortion and Data Theft Attacks
The threat actor known as Muddled Libra has been observed actively targeting software-as-a-service (SaaS) applications and cloud service provider (CSP) environments in...
-

 1.8KVulnerabilities
1.8KVulnerabilitiesPalo Alto Networks Releases Urgent Fixes for Exploited PAN-OS Vulnerability
Palo Alto Networks has released hotfixes to address a maximum-severity security flaw impacting PAN-OS software that has come under active exploitation in...
-

 1.5KData Breach
1.5KData BreachU.S. Federal Agencies Ordered to Hunt for Signs of Microsoft Breach and Mitigate Risks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday issued an emergency directive (ED 24-02) urging federal agencies to hunt for...
-

 3.2KVulnerabilities
3.2KVulnerabilitiesMicrosoft Fixes 149 Flaws in Huge April Patch Release, Zero-Days Included
Microsoft has released security updates for the month of April 2024 to remediate a record 149 flaws, two of which have come...
-

 3.9KVulnerabilities
3.9KVulnerabilitiesU.S. Cyber Safety Board Slams Microsoft Over Breach by China-Based Hackers
The U.S. Cyber Safety Review Board (CSRB) has criticized Microsoft for a series of security lapses that led to the breach of...
-

 3.4KMalware
3.4KMalwareNew Webinar: Avoiding Application Security Blind Spots with OPSWAT and F5
Considering the ever-changing state of cybersecurity, it’s never too late to ask yourself, “am I doing what’s necessary to keep my organization’s...
-

 2.0KVulnerabilities
2.0KVulnerabilitiesCritical Unpatched Ray AI Platform Vulnerability Exploited for Cryptocurrency Mining
Cybersecurity researchers are warning that threat actors are actively exploiting a “disputed” and unpatched vulnerability in an open-source artificial intelligence (AI) platform...
-

 1.0KVulnerabilities
1.0KVulnerabilitiesAndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials
Cybersecurity researchers have shed light on a tool referred to as AndroxGh0st that’s used to target Laravel applications and steal sensitive data....
-

 2.6KData Breach
2.6KData BreachCrafting and Communicating Your Cybersecurity Strategy for Board Buy-In
In an era where digital transformation drives business across sectors, cybersecurity has transcended its traditional operational role to become a cornerstone of...
-
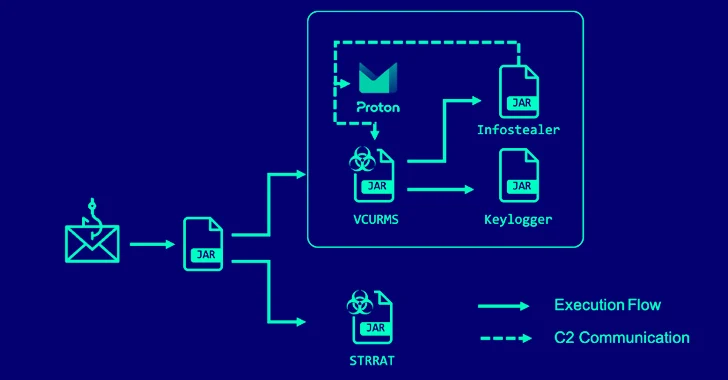
 2.6KData Breach
2.6KData BreachAlert: Cybercriminals Deploying VCURMS and STRRAT Trojans via AWS and GitHub
A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious...
-

 2.9KData Breach
2.9KData BreachFrom 500 to 5000 Employees – Securing 3rd Party App-Usage in Mid-Market Companies
A company’s lifecycle stage, size, and state have a significant impact on its security needs, policies, and priorities. This is particularly true...
-
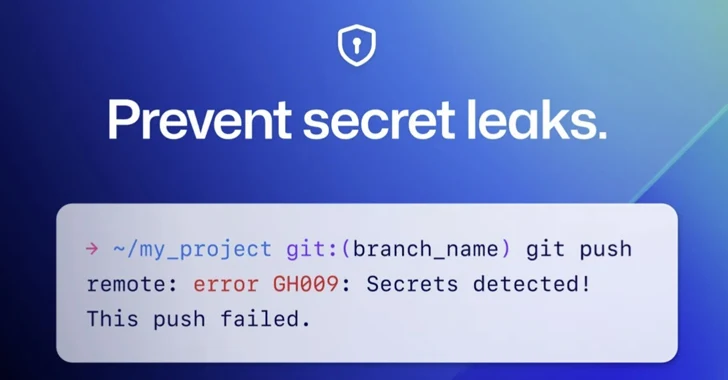
 4.0KMalware
4.0KMalwareGitHub Rolls Out Default Secret Scanning Push Protection for Public Repositories
GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to public repositories. “This means that...
-

 878Vulnerabilities
878VulnerabilitiesWhy We Must Democratize Cybersecurity
With breaches making the headlines on an almost weekly basis, the cybersecurity challenges we face are becoming visible not only to large...
-

 617Data Breach
617Data BreachCybersecurity Tactics FinServ Institutions Can Bank On in 2024
The landscape of cybersecurity in financial services is undergoing a rapid transformation. Cybercriminals are exploiting advanced technologies and methodologies, making traditional security...
-

 3.5KData Breach
3.5KData BreachHands-On Review: SASE-based XDR from Cato Networks
Companies are engaged in a seemingly endless cat-and-mouse game when it comes to cybersecurity and cyber threats. As organizations put up one...
-

 2.5KData Breach
2.5KData BreachCloudflare Breach: Nation-State Hackers Access Source Code and Internal Docs
Cloudflare has revealed that it was the target of a likely nation-state attack in which the threat actor leveraged stolen credentials to...
-

 2.4KData Breach
2.4KData BreachThe SEC Won’t Let CISOs Be: Understanding New SaaS Cybersecurity Rules
The SEC isn’t giving SaaS a free pass. Applicable public companies, known as “registrants,” are now subject to cyber incident disclosure and...
-

 2.2KData Breach
2.2KData Breach29-Year-Old Ukrainian Cryptojacking Kingpin Arrested for Exploiting Cloud Services
A 29-year-old Ukrainian national has been arrested in connection with running a “sophisticated cryptojacking scheme,” netting them over $2 million (€1.8 million)...
-
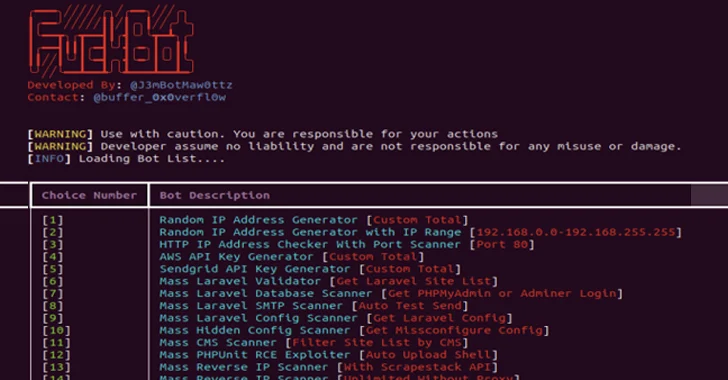
 526Malware
526MalwareNew Python-based FBot Hacking Toolkit Aims at Cloud and SaaS Platforms
A new Python-based hacking tool called FBot has been uncovered targeting web servers, cloud services, content management systems (CMS), and SaaS platforms...
-

 2.8KVulnerabilities
2.8KVulnerabilitiesWhy Public Links Expose Your SaaS Attack Surface
Collaboration is a powerful selling point for SaaS applications. Microsoft, Github, Miro, and others promote the collaborative nature of their software applications...
-

 3.2KVulnerabilities
3.2KVulnerabilitiesGoogle Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service
Google Cloud has addressed a medium-severity security flaw in its platform that could be abused by an attacker who already has access...






