All posts tagged "Keylogger"
-

 3.0KVulnerabilities
3.0KVulnerabilitiesAllaKore RAT Malware Targeting Mexican Firms with Financial Fraud Tricks
Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a modified version of an open-source remote access...
-

 4.3KVulnerabilities
4.3KVulnerabilitiesSystemBC Malware’s C2 Server Analysis Exposes Payload Delivery Tricks
Cybersecurity researchers have shed light on the command-and-control (C2) server workings of a known malware family called SystemBC. “SystemBC can be purchased...
-
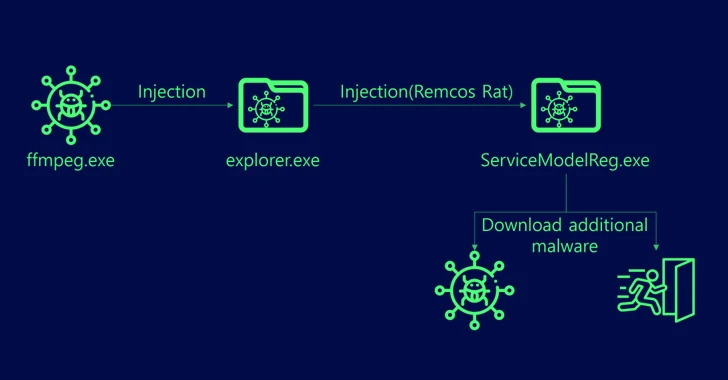
 1.1KMalware
1.1KMalwareRemcos RAT Spreading Through Adult Games in New Attack Wave
The remote access trojan (RAT) known as Remcos RAT has been found being propagated via webhards by disguising it as adult-themed games...
-

 3.1KVulnerabilities
3.1KVulnerabilitiesUAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware
The threat actor known as UAC-0099 has been linked to continued attacks aimed at Ukraine, some of which leverage a high-severity flaw...
-

 4.5KMalware
4.5KMalwareRhadamanthys Malware: Swiss Army Knife of Information Stealers Emerges
The developers of the information stealer malware known as Rhadamanthys are actively iterating on its features, broadening its information-gathering capabilities and also...
-

 4.0KMalware
4.0KMalwareNew Agent Tesla Malware Variant Using ZPAQ Compression in Email Attacks
A new variant of the Agent Tesla malware has been observed delivered via a lure file with the ZPAQ compression format to...
-

 4.8KCyber Attack
4.8KCyber AttackPakistani Hackers Use Linux Malware Poseidon to Target Indian Government Agencies
The Pakistan-based advanced persistent threat (APT) actor known as Transparent Tribe used a two-factor authentication (2FA) tool used by Indian government agencies...
-
 4.9KMalware
4.9KMalwareAgent Tesla’s Successor OriginLogger Keylogger Malware Steals Credentials, Takes Screenshots
The malware called OriginLogger has recently been dissected in detail by security experts from Palo Alto Networks Unit 42. It is believed...
-
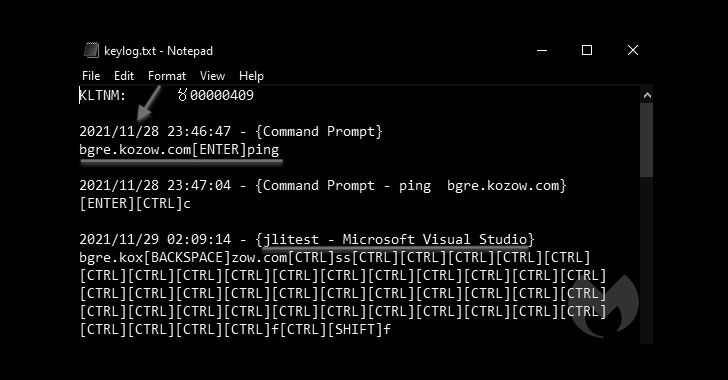
 3.6KMalware
3.6KMalwareBADNEWS! Patchwork APT Hackers Score Own Goal in Recent Malware Attacks
Threat hunters have shed light on the tactics, techniques, and procedures embraced by an Indian-origin hacking group called Patchwork as part of...
-

 3.4KData Security
3.4KData Security$120 charging cable O.MG remotely steals data from Apple devices
Originally, O.MG Cable was introduced in 2019. In 2019, at DEFCON, an IT security researcher going by the online handle of MG...
-

 4.1KNews
4.1KNewsHow to find out the Best iPhone Keylogger?
Picking up the best match for our needs was never as tough as it is these days. The market is flooded with...
-
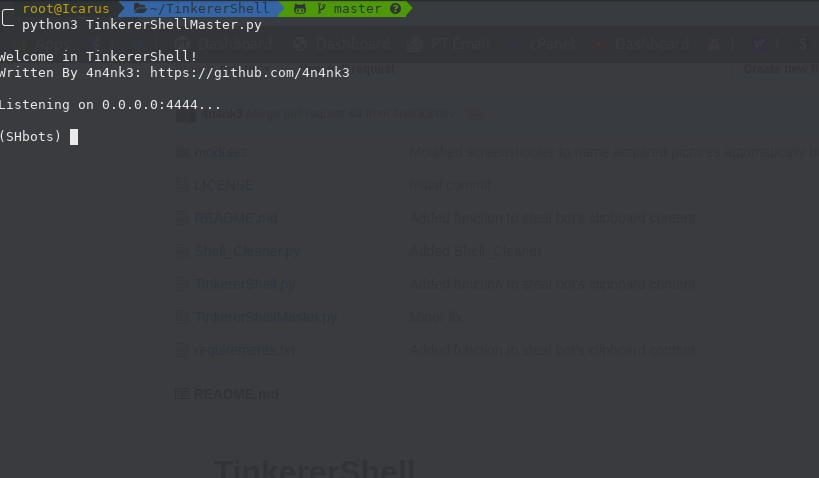
 4.0KExploitation Tools
4.0KExploitation ToolsTinkererShell – A Simple Python Reverse Shell Written Just For Fun
A simple reverse shell written in python 3.7 just for fun. Actually it supports Windows and Linux OS and integrates some...
-

 388Data Security
388Data SecurityEvilGnomes Linux malware record activities & spy on users
The EvilGnomes Linux malware has been linked to infamous Russian threat actors from the Gamaredon Group. The IT security researchers at Intezar...
-

 657Data Breach
657Data BreachCathay Pacific 2014 Breach Fully Disclosed By Hong Kong
The Hong Kong Special Administrative Region in China, through its Privacy Commissioner, Stephen Kai-yi Wong has publicly disclosed a report containing more...
-

 242Malware
242MalwarePopular Video Editing Software Website Hacked to Spread Banking Trojan
If you have downloaded the VSDC multimedia editing software between late February to late March this year, there are high chances that...
-
 259Data Security
259Data SecuritySevere flaws in password managers let hackers extract clear-text passwords
Password Managers aren’t as secure as you might assume – Security researchers claim that hackers can steal master passwords in PC memory....
-

 331Geek
331GeekMalicious apps deploy Anubis banking trojan using motion detection
Google has left no stone unturned in preventing malware and banking trojan from invading the applications uploaded on its official Play Store....
-

 226News
226NewsHave a Safe Holiday Season To All Of You From Hackercombat.com
The holiday season is considered as a season for giving, however, in the age of Information when data is considered wealth, all...
-

 221Ransomware
221RansomwareHackers Spreading New Virobot Ransomware with Powerful Botnet & Keylogging Capabilities
Researchers discovered new Virobot Ransomware that distributed along with botnet futures mainly focusing on victims based on the United States. Attackers using spam email...
-

 449Data Security
449Data SecurityHacking tools & ready-made phishing pages being sold on dark web for $2
Apple Hacking Tools Double the Cost of Other Brands on Dark Web. There was a time when hackers needed to be really...
-

 379Data Security
379Data SecurityHundreds of Android apps on Play Store infected with Windows malware
Yes, malware in Android apps aimed at Windows devices. Palo Alto Networks’ researchers have made a startling new discovery that nearly 145...






