All posts tagged "Linux"
-

 2.1KMalware
2.1KMalwareNew Mirai Botnet Variant ‘V3G4’ Exploiting 13 Flaws to Target Linux and IoT Devices
A new variant of the notorious Mirai botnet has been found leveraging several security vulnerabilities to propagate itself to Linux and IoT...
-

 5.0KCyber Attack
5.0KCyber AttackLinux Variant of Clop Ransomware Spotted, But Uses Faulty Encryption Algorithm
The first-ever Linux variant of the Clop ransomware has been detected in the wild, but with a faulty encryption algorithm that has...
-

 285Malware
285MalwareNew shc-based Linux Malware Targeting Systems with Cryptocurrency Miner
A new Linux malware developed using the shell script compiler (shc) has been observed deploying a cryptocurrency miner on compromised systems. “It...
-

 3.1KMalware
3.1KMalwareWordPress Security Alert: New Linux Malware Exploiting Over Two Dozen CMS Flaws
WordPress sites are being targeted by a previously unknown strain of Linux malware that exploits flaws in over two dozen plugins and...
-

 3.1KMalware
3.1KMalwareCryptocurrency Mining Campaign Hits Linux Users with Go-based CHAOS Malware
A cryptocurrency mining attack targeting the Linux operating system also involved the use of an open source remote access trojan (RAT) dubbed...
-

 2.1KMalware
2.1KMalwareNew Stealthy Shikitega Malware Targeting Linux Systems and IoT Devices
A new piece of stealthy Linux malware called Shikitega has been uncovered adopting a multi-stage infection chain to compromise endpoints and IoT...
-

 3.2KVulnerabilities
3.2KVulnerabilities“As Nasty as Dirty Pipe” — 8 Year Old Linux Kernel Vulnerability Uncovered
Details of an eight-year-old security vulnerability in the Linux kernel have emerged that the researchers say is “as nasty as Dirty Pipe.”...
-

 4.2KCyber Attack
4.2KCyber AttackNew Linux Malware Framework Lets Attackers Install Rootkit on Targeted Systems
A never-before-seen Linux malware has been dubbed a “Swiss Army Knife” for its modular architecture and its capability to install rootkits. This...
-
 1.4KMalware
1.4KMalwareResearchers Warn of New OrBit Linux Malware That Hijacks Execution Flow
Cybersecurity researchers have taken the wraps off a new and entirely undetected Linux threat dubbed OrBit, signally a growing trend of malware...
-
 1.9KVulnerabilities
1.9KVulnerabilitiesCISA Warns of Active Exploitation of ‘PwnKit’ Linux Vulnerability in the Wild
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week moved to add a Linux vulnerability dubbed PwnKit to its Known Exploited...
-
 3.4KMalware
3.4KMalwarePanchan: A New Golang-based Peer-To-Peer Botnet Targeting Linux Servers
A new Golang-based peer-to-peer (P2P) botnet has been spotted actively targeting Linux servers in the education sector since its emergence in March...
-

 1.5KMalware
1.5KMalwareHelloXD Ransomware Installing Backdoor on Targeted Windows and Linux Systems
Windows and Linux systems are being targeted by a ransomware variant called HelloXD, with the infections also involving the deployment of a...
-
 4.2KMalware
4.2KMalwareSymbiote: A Stealthy Linux Malware Targeting Latin American Financial Sector
Cybersecurity researchers have taken the wraps off what they call a “nearly-impossible-to-detect” Linux malware that could be weaponized to backdoor infected systems....
-
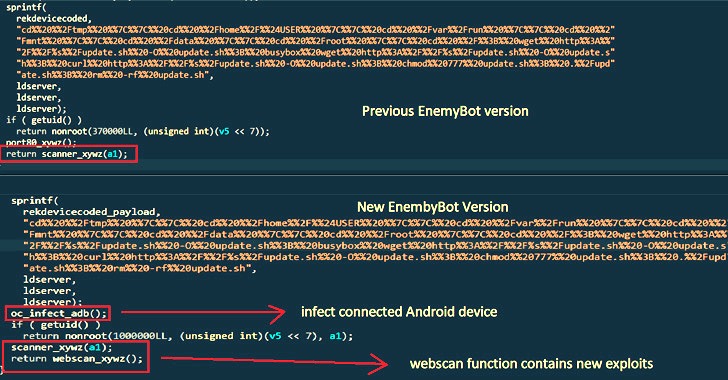
 2.6KMalware
2.6KMalwareEnemyBot Linux Botnet Now Exploits Web Server, Android and CMS Vulnerabilities
A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web...
-
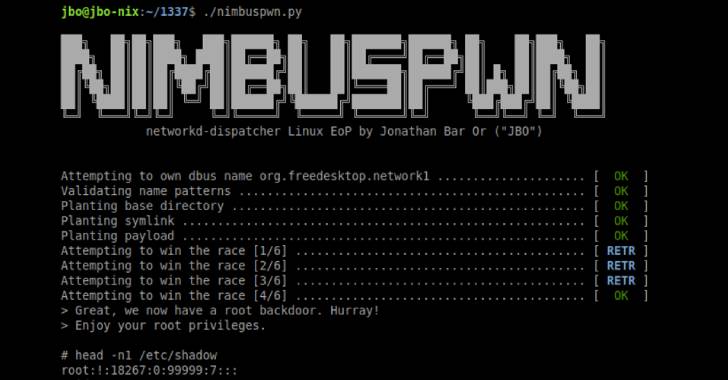
 3.1KVulnerabilities
3.1KVulnerabilitiesMicrosoft Discovers New Privilege Escalation Flaws in Linux Operating System
Microsoft on Tuesday disclosed a set of two privilege escalation vulnerabilities in the Linux operating system that could potentially allow threat actors...
-
 5.1KVulnerabilities
5.1KVulnerabilitiesHackers Exploiting Spring4Shell Vulnerability to Deploy Mirai Botnet Malware
The recently disclosed critical Spring4Shell vulnerability is being actively exploited by threat actors to execute the Mirai botnet malware, particularly in the...
-

 2.8KVulnerabilities
2.8KVulnerabilitiesMuhstik Botnet Targeting Redis Servers Using Recently Disclosed Vulnerability
Muhstik, a botnet infamous for propagating via web application exploits, has been observed targeting Redis servers using a recently disclosed vulnerability in...
-

 4.2KMalware
4.2KMalwareHackers Target Bank Networks with new Rootkit to Steal Money from ATM Machines
A financially motivated threat actor has been observed deploying a previously unknown rootkit targeting Oracle Solaris systems with the goal of compromising...
-

 393Malware
393MalwareNew “B1txor20” Linux Botnet Uses DNS Tunnel and Exploits Log4J Flaw
A previously undocumented backdoor has been observed targeting Linux systems with the goal of corralling the machines into a botnet and acting...
-
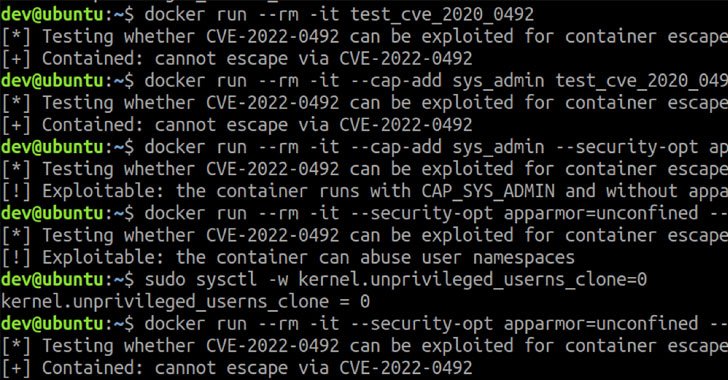
 4.3KVulnerabilities
4.3KVulnerabilitiesNew Linux Kernel cgroups Vulnerability Could Let Attackers Escape Container
Details have emerged about a now-patched high-severity vulnerability in the Linux kernel that could potentially be abused to escape a container in...
-
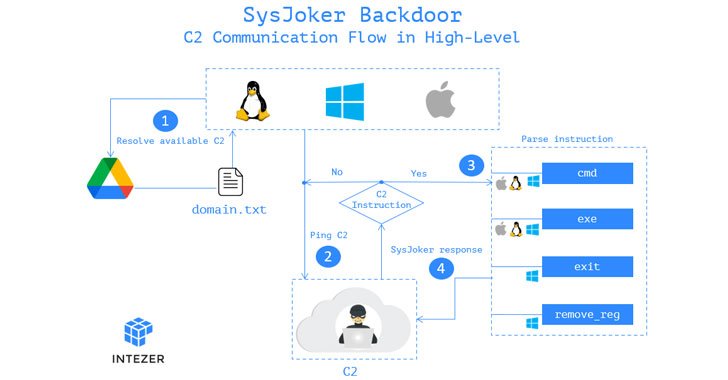
 2.8KMalware
2.8KMalwareNew SysJoker Espionage Malware Targeting Windows, macOS, and Linux Users
A new cross-platform backdoor called “SysJoker” has been observed targeting machines running Windows, Linux, and macOS operating systems as part of an...






