Story of an Advanced Persistent Threat attack against a large corporation that started with a series of blank emails.
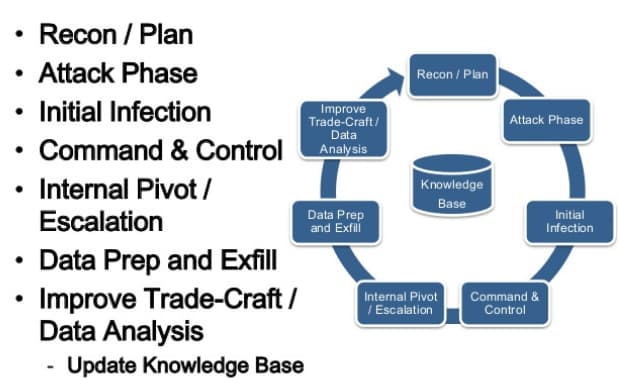
Advanced persistent threats (APTs) are increasingly targeting enterprise networks nowadays. This article highlights a recent attack against a large, well-protected Australian organization that entailed a major data breach.
It’s Monday, 12:55 p.m. In Sydney, Olivia Wilson (name changed) returns from her lunch break and discovers a new email in her inbox with the subject “Are we still on for tonight meeting?” She routinely opens it, and it turns out to be empty. Mary doesn’t think such a trifle is worth reporting to the IT department, so she moves on with her work. This was the first stage of a targeted cyber-attack.
Hundreds of similar messages will have been received by the staff of this company by the end of the workday. This was part of a reconnaissance phase of the incursion, where the adversaries tried to figure out which mailboxes were real and which recipients might reply.
This milestone, in general, also gives the malefactors an idea of what the organization’s IT environment is like and allows them to gauge its defenses to a certain extent. For instance, the intruders can scan for open ports, identify sandboxing tools that are easy to get around, and spot other vulnerabilities in the enterprise network. Additionally, they can collect and analyze background data on the key employees.
The next stage of the attack involves direct damage as the crooks send targeted messages to employees.
It was a long day for Sam and he can’t wait to go home, which makes him a little bit incautious. He sees an email from his son’s soccer coach with updates in the training schedule attached to it. He goes ahead and opens the file that really resembles the schedule his son’s coach typically sends. By doing so, he unwittingly launches the adversaries’ payload.
If this stratagem doesn’t work out as the attackers expect, they have a plan B. They had previously hacked a website of the company’s contractor that Sam often logs into. Therefore, the next time he logs in, the similar malicious code will be deposited onto his computer.
Sam wasn’t the only target. The spear phishing messages reached more than 150 mailboxes across the organization, enticing several dozen employees to log in and thereby unknowingly allow the crooks to get hold of their credentials. Henceforth, the malefactors could access those mail accounts and potentially expand the attack surface from there.
As soon as the intruders have access to the enterprise network, they can look for specific vulnerabilities in deployed software and install backdoors or RATs (remote access Trojans), which allows them to maintain persistence even if passwords are reset. This activity is referred to as the installation stage.
During the next few months, the adversaries will persevere in the host environment, scouring the company’s network for different types of information. All data they harvest will be encrypted and gradually exfiltrated outside the company without giving anyone a heads-up. It’s quite likely that they will also try to eliminate all evidence of the trespass to increase the odds of being undetected for a longer period of time.
Attacks of this kind tend to circumvent traditional defenses, such as end-point antivirus, firewalls, sandboxes, and most high-end VPN solutions. If this particular organization had leveraged a custom defense solution from a reputable vendor, the attack described above could have never succeeded beyond the reconnaissance phase.
Remember, effective custom defense solutions are constantly inspecting the enterprise network from multiple different angles. They are capable of monitoring more than 100 protocols and all network ports for outright attacks and anomalous activity, such as known and uncatalogued malware, documented and zero-day exploits, as well as telltale signs of command and control.
Additionally, the Australian company in question could have set up a customized sandbox to scrutinize dodgy payloads, files, URLs, email and mobile apps. Given that many organizations already use basic security mechanisms, custom protection can complement them with refined sandbox features. Another benefit of using it is that the built-in forensic modules can identify and neutralize emerging strains of targeted malware on every end-point.
Advanced persistent threat attacks, such as the one covered above, are on the rise these days. A particularly disconcerting thing is that most businesses (not only in Australia) are unprepared for them, so it’s high time this started changing.