CloudTrail is the tool that AWS administrators rely on to keep track of all API activity inside their accounts. CloudTrail helps teams to identify unusual behavior in AWS environments, spot attacks quicker, and get a better understanding of what occurred after security events. This is accomplished by monitoring the use of APIs.
CloudTrail is an event recording service that offers a source of truth for the activities that occur inside an Amazon Web Services (AWS) account. In addition to recording control plane and data plane API requests (the latter of which may be optional for some services), it also logs other sorts of events. In general, all activities that are performed through the API are logged, regardless of whether those actions were generated via the command line interface provided by AWS, the management console, or software that makes use of the SDKs. CloudTrail “helps you provide operational and risk audits, governance, and compliance of your AWS account,” as stated by Amazon Web Services (AWS).
Because of these characteristics, CloudTrail has become the resource that engineers turn to first when they need to discover what actions an attacker took during a security event. If an attacker were able to carry out activities via the AWS API while simultaneously avoiding CloudTrail’s monitoring, then defenders would have no means of understanding what had taken place. CloudTrail is an event recording service that offers a source of truth for the activities that occur inside an Amazon Web Services (AWS) account. In addition to recording control plane and data plane API requests (the latter of which may be optional for some services), it also logs other sorts of events. In general, all activities that are performed through the API are logged, regardless of whether those actions were generated via the command line interface provided by AWS, the management console, or software that makes use of the SDKs. CloudTrail “helps you provide operational and risk audits, governance, and compliance of your AWS account,” as stated by Amazon Web Services (AWS).
Because of these characteristics, CloudTrail has become the resource that engineers turn to first when they need to discover what actions an attacker took during a security event. If an attacker were able to carry out activities via the AWS API while simultaneously avoiding CloudTrail’s monitoring, then defenders would have no means of understanding what had taken place.
The Datadog Security Research Team came up with a way to sidestep the logging done by CloudTrail for certain IAM API queries by using undocumented APIs. After obtaining a foothold in an AWS account, an attacker might use this approach to execute reconnaissance operations in the IAM service without leaving any record of their activity in CloudTrail. This would enable the opponent to perform these activities without being detected by AWS.
The team performed tests on two services known as iam and iamadmi, both of which are used in the AWS Console to accept requests. Datadog discovered that iamadmin was an undocumented API, and it was discovered that when endpoints were called, such as ListMFADevicesForMultipleUsers, which is a wrapper for iam:ListMFADevices, there was no event log in CloudTrail.
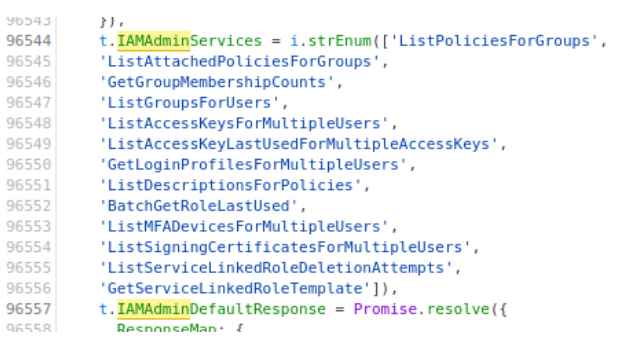
The group discovered a total of 13 different AIM methods that might be invoked, some of which resulted in unexpected results.
Having the ability to circumvent CloudTrail logging and get the outcomes of those calls has significant repercussions for defenders. This is because it reduces their capacity to monitor what an adversary has done inside an environment and what actions they have made.
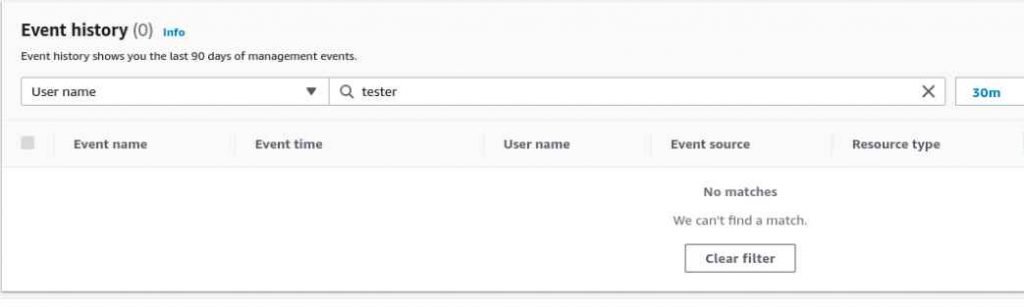
In addition, using this method makes it possible to avoid being alerted by GuardDuty for discoveries such as IAMUser/AnomalousBehavior. This is due to the fact that GuardDuty utilizes CloudTrail as a data source, and it is unable to generate an alert for something that it is unable to see.
They reached out to AWS to inform them of this discovery, and they immediately started the process of addressing the vulnerability they discovered. This loophole in the logging system has been closed.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.