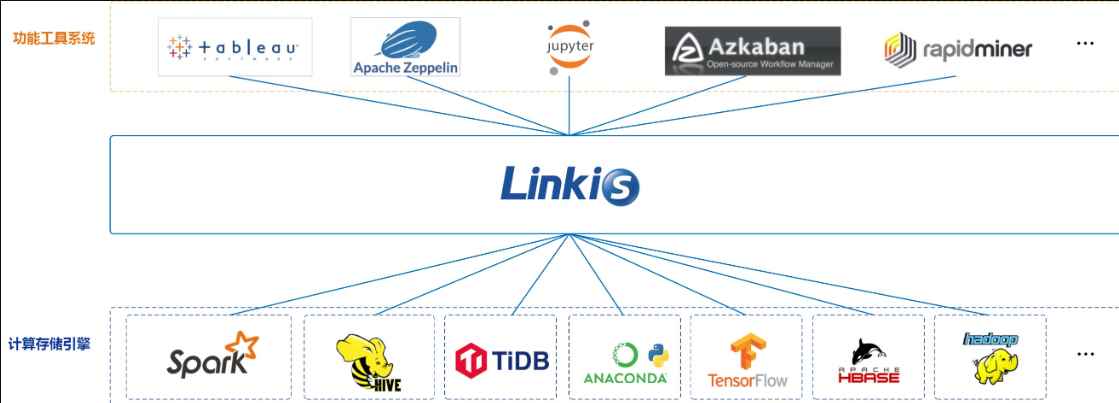
Apache Linkis creates a compute middleware layer to unify task and engine governance and orchestration while enabling cross-engine context sharing. It also provides standardized interfaces (REST, JDBC, WebSocket, etc.) to connect to multiple engines like Spark, Presto, Flink, etc.
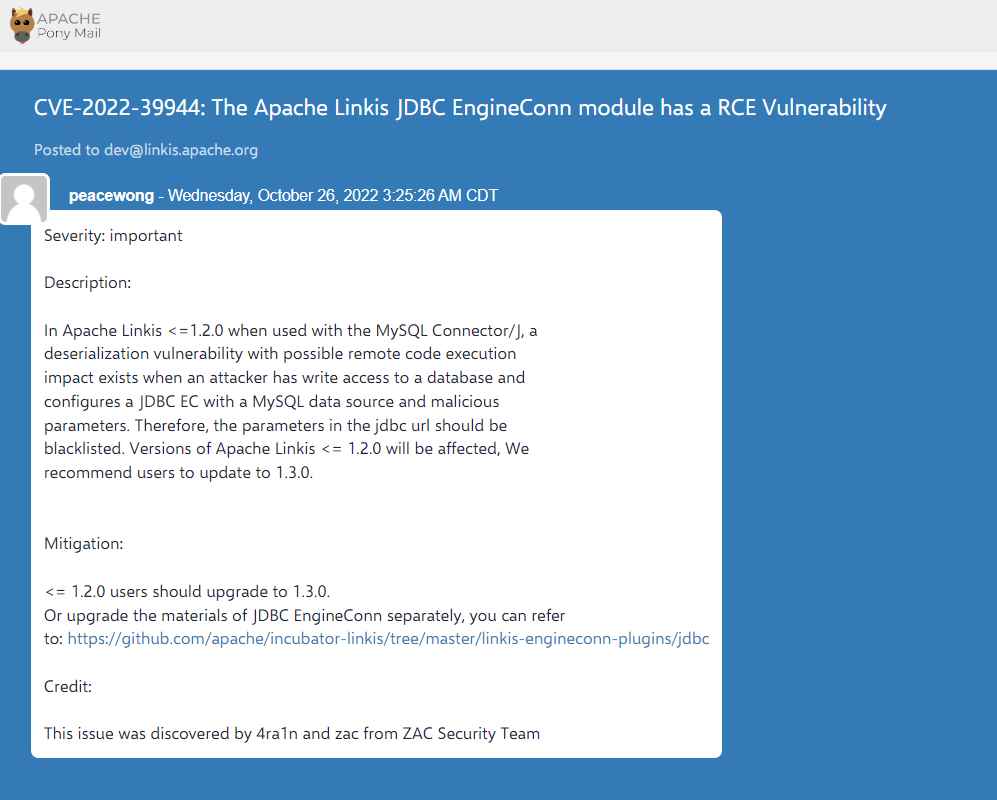
CVE-2022-3994
The JDBC EngineConn module has a flaw, which an attacker might use to deserialize and thereby get remote code execution.
A deserialization vulnerability exists in Apache Linkis =1.2.0 when combined with the MySQL Connector/J when an advisory has write access to a database and configures a JDBC EC with a MySQL data source and malicious parameters. Consequently, it is necessary to blacklist the arguments in the jdbc url. Affected version includes Apache Linkis version prior to 1.3.0.
The vulnerability has been patched in the most recent version of Apache Linkis. Users are recommended to upgrade the JDBC EngineConn materials individually or install the unaffected version as soon as feasible,

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.