An open-source project called OpenSSL is used to protect communications all across the world and offers simple cryptographic functionality. Simply put, OpenSSL powers the internet. OpenSSL has a number of flaws, but the two that are most well-known are the Heartbleed bug (CVE-2014-0160) and the OpenSSL 1.1.0a vulnerability (CVE-2016-6309).
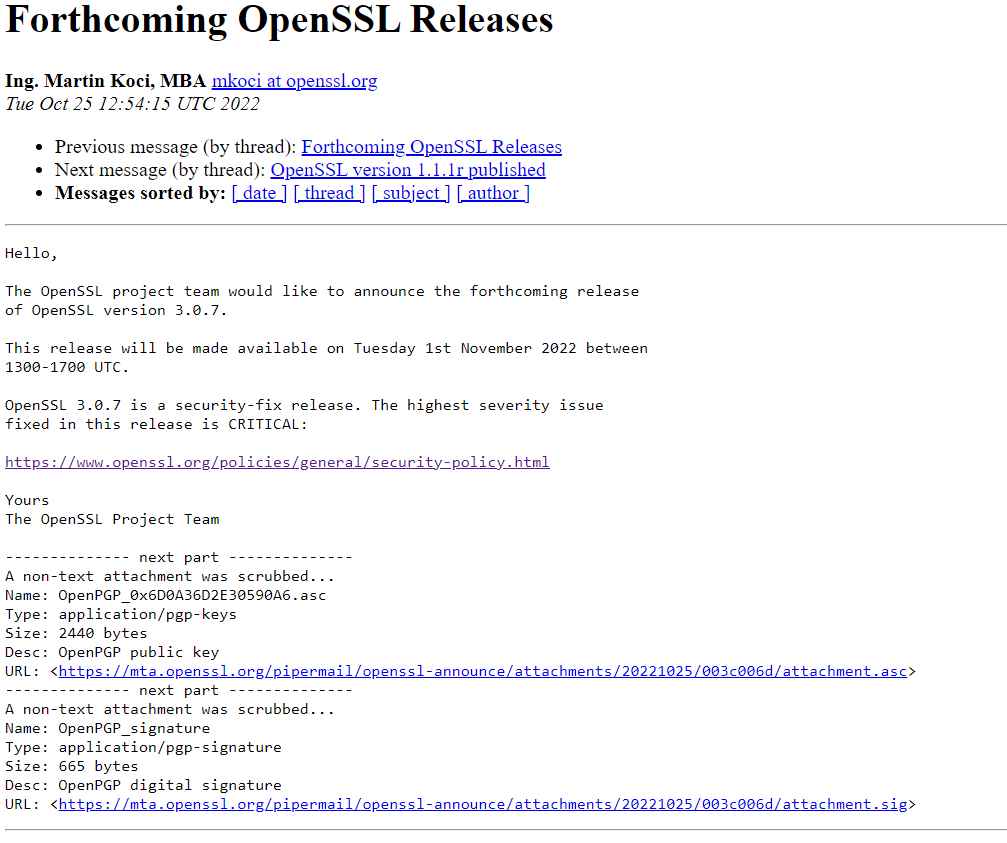
The upcoming release of OpenSSL 3.0.7 was announced by the OpenSSL Project Team. This is one of the most crucial upgrades since the OpenSSL Project has identified a “critical” vulnerability in versions 3.0 and later of the very well-liked cryptographic library used to secure Internet connections.
Everyone is dependent on OpenSSL because, as we stated before, “the internet runs on OpenSSL.” You might not be aware of this, but Linux, Unix, Windows, and many more operating systems can all employ safe Transport Layer Security (TLS) thanks to OpenSSL.
A Critical Severity vulnerability “affects common setups and which are also likely to be exploited,” according to the security guidelines of the OpenSSL team. Examples include considerable server memory exposure (which might divulge user information), vulnerabilities that are readily exploited remotely to compromise server private keys, or circumstances where remote code execution is thought to be possible.
This issue only affects OpenSSL versions 3.0.0 through 3.0.6, according to the first alert. This indicates that earlier devices and operating systems are probably unaffected by the problem.
However, Ubuntu 20.04 and previous versions of Red Hat Enterprise Linux (RHEL) 8.x are unaffected by it. Due to the usage of OpenSSL 3.x, RHEL 9.x and Ubuntu 22.04 may be susceptible.
We must wait till then because there isn’t much information known about the vulnerability, no CVE has been given, and an update will also be released on November 1st.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.