Cybersecurity specialists report the detection of a critical zero-day vulnerability in Google Chrome that could put at risk the data of all browser users. While most researchers who have analyzed this report consider it a serious problem, a sector of the community believes that the failure is even worse than previously thought.
Despite these claims, the tech giant says that it is enough to apply the new Chrome updates to fully mitigate the risk of exploitation and potential incidents of data leakage.
It should be remembered that, despite the wide availability of options, Chrome has remained the most used browser on the market, with more than 2 billion active users worldwide. Therefore, any minimal risk to the security of users’ information could pose an unprecedented threat.
In addition to its inherent flaws, threat actors are always looking for new methods to exploit any flaws in Chrome, considered one of the main targets for cybercriminals.
On the reported vulnerability, the experts did not add too many details, they only mentioned that some cases of exploitation have already been detected in real scenarios and that it is best to implement the relevant updates as soon as possible. Experts also mentioned that the flaw has been exploited in Windows, Linux and macOS systems, present in hundreds of millions of computers around the world.
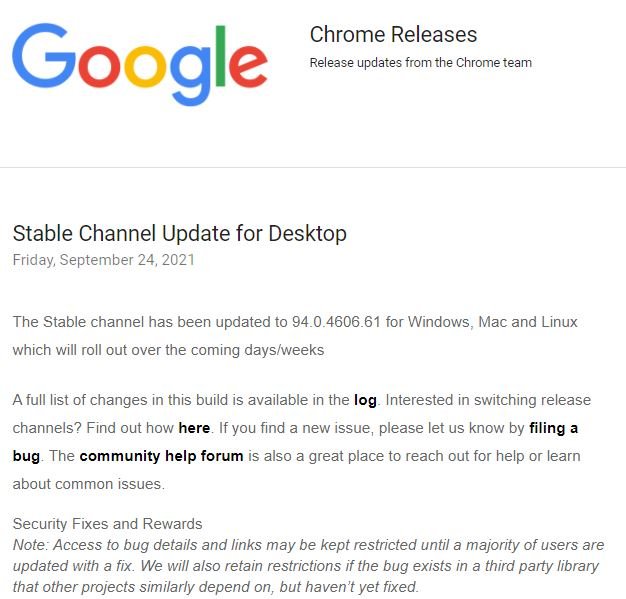
After receiving the report Google recognized the flaw, tracked as CVE-2021-37973, issuing a statement to recommend its users update their systems: “We want to thank all the researchers who collaborated in this finding to prevent these errors from reaching the stable channel.”
As a security measure, browser users are strongly encouraged to update Chrome to the latest version available (v94.0.4606.61), available for Linux, Windows, and macOS users. While Google did not share technical details about the failure, the company has emphasized the fact that it is enough to apply these updates to avoid the risk of exploitation in real scenarios.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















