Vulnerability in Drupal CMS turned popular websites into Monero Mining Platform. The criptockacking is becoming a plague that affects consumers around the world, and what are even worse, experts do not know how to deal with the situation. According to an investigation carried out by the information security professional Troo Mursch about the defective packages, more than 400 websites have been attacked by hackers with crypto-jacking last weekend.

These sites are vulnerable because they use an outdated version of the Drupal Content Management System. The main victims were found in the USA since 123 US websites were identified UU France in second place with 26 infected sites, Canada 19, Germany 18 and Russia 17.
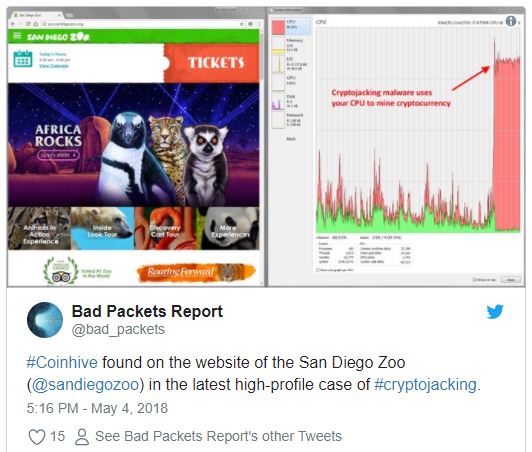
Researchers commented that some government websites, including the Chihuahua government, are included in the victims; the Revenue Administration of Turkey, and the Higher Education Quality Improvement Project of Peru, Lenovo, the San Diego Zoo and the websites of the US educational institutions. UU
Other important names within the list of victims are: The National Board of Labor Relations of EE. UU. University of California at Los Angeles, Board of Arizona Behavioral Health Examiners, and City of Marion websites.
The information security researcher has closely followed the campaign, has managed to identify what it means to hijack the processing of the PC to generate Monero. Users may not know that their PC is being used to mine cryptocurrencies.
All infected websites use a piece of similar JavaScript hosted on vuuwd.com. Which is an obfuscated code that affects the performance of the visitor, since he is obliged to dedicate 80% of his CPU resources to mining Monero?
The miner who infects the PC is active in the browser and, as it loads the website, begins to consume the power of the processor for mining, say information security professionals. Hackers need to infect enough computers with crypto-miners to earn enough money.
By mining, the processor slows down due to the heavy workload and an excessive amount of electricity is consumed.
The Drupal CMS vulnerability makes it easier to launch code execution attacks, Drupalgeddon2. Although the defect was patched in March, there are still many sites that are outdated and vulnerable.
“If you are a website operator that uses Drupal’s content management system, you must update to the latest available version as soon as possible,” Mursch wrote.
After the publication of the information security expert was published over the weekend, few of the infected websites were disinfected on Monday morning. The campaign is still active and continually engages new websites, as until the weekend Mursch identified 348 infected websites and the number increased to more than 400 by Monday morning.
In addition to exploiting Drupalgeddon2, cybercriminals are also installing malware to perform denial of service attacks on websites.










