JFrog security teams report finding 5 vulnerabilities in PJSIP, a multimedia communication library developed by Teluu. According to the report, successful exploitation of these flaws would allow threat actors to lead to an arbitrary code execution scenario in applications using this library.
This library provides an API that can be used by IP telephony applications, such as VoIP phones and video conferencing applications. It is used today by the most popular communication apps in the world, such as WhatsApp and BlueJeans.
Below are brief descriptions of the reported flaws, in addition to their respective identification keys and scores assigned under the Common Vulnerability Scoring System (CVSS).
CVE-2021-43299 (CVSS 8.1/10): The flaw lies in pjsua_player_create, which creates a file player and automatically adds it to the conference bridge. This feature contains a stack overflow vulnerability:
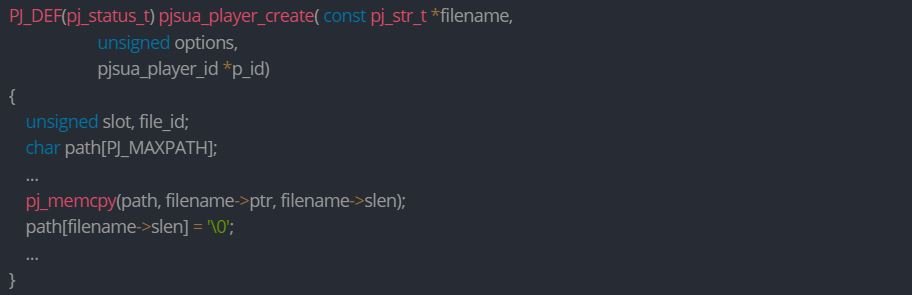
The filename->ptr feature is copied to the path without verifying that filename->slen has a maximum of the assigned path size, which is PJ_MAXPATH<c/ode> (260). Therefore, passing a file name longer than 260 characters will cause the stack to overflow.
CVE-2021-43300 & CVE-2021-43302 (CVSS 8.1/10): These flaws reside in pjsua_recorder_create(), tasked with creating a file recorder and automatically connects this recorder to the conference bridge, leading to a stack-based buffer overflow.
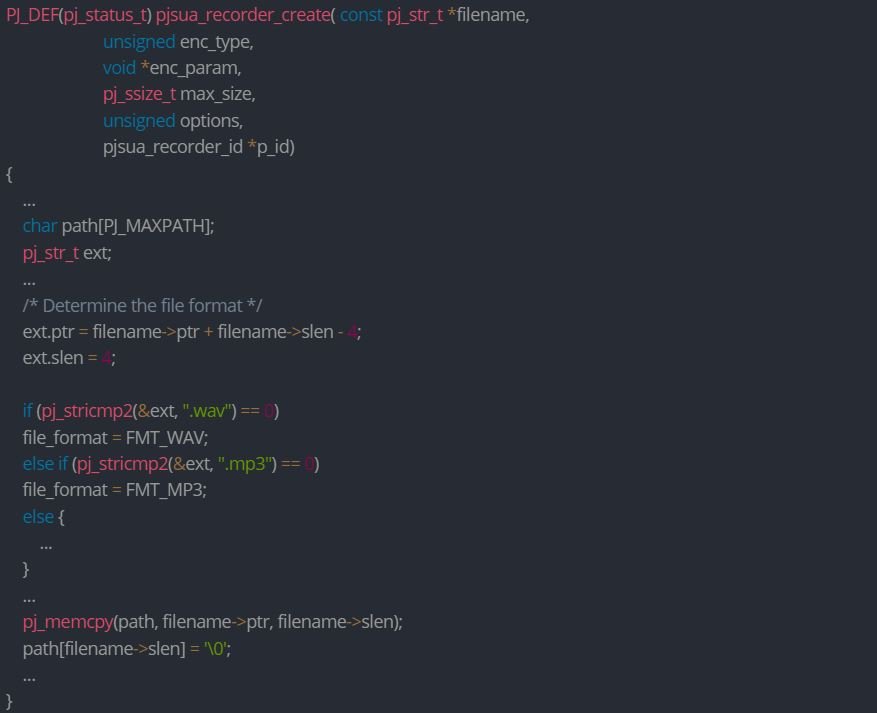
CVE-2021-43302 exists because pjsua_recorder_create does not check if the length of the file name is at least 4. If the file name is shorter than 4, pj_stricmp2 will cause an out-of-bounds read when comparing strings.
On the other hand, CVE-2021-43300 exists because filename->ptr is copied with memcpy to the path stack variable without verifying that filename->slen has at most the size assigned to the path, which is PJ_MAXPATH (260).
CVE-2021-43301 (CVSS 5.9/10): This is also a stack overflow flaw that affects pjsua_playlist_create, which creates a file playlist media port and automatically adds the port to the conference bridge. At startup, pjsua_playlist_create calls pjmedia_wav_playlist_create with the file_names argument assigned as file_list:
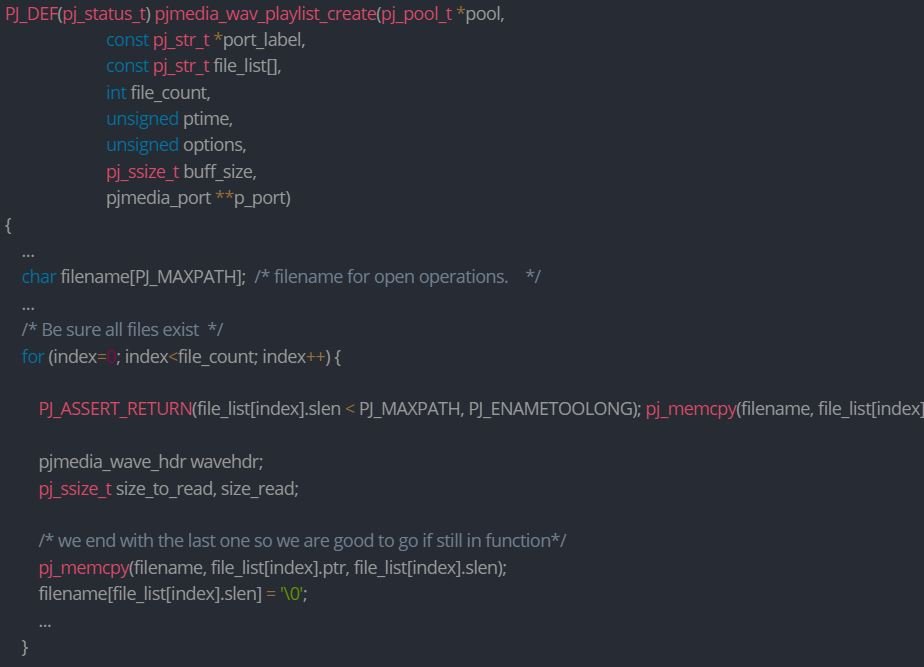
The function copies each file name from file_list to filename without checking whether its length is at most PJ_MAXPATH (260). If the length of the file name is longer, the stack-based buffer overflow is created.
CVE-2021-43303 (CVSS 5.9/10): Buffer overflow vulnerability in pjsua_call_dump, a function that downloads call statistics to a given buffer:
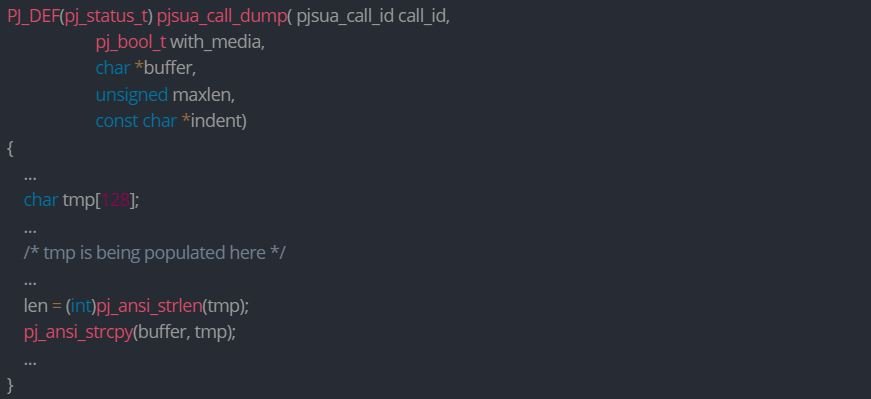
The function uses tmp to store the statistics temporarily and then copies them to the output argument buffer without validating that maxlen is at most len. This can cause a buffer overflow if the capacity of the given buffer parameter is less than len.
Fixing these flaws requires updating PJSIP to version 2.12, so developers recommend addressing the flaws as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















