Microsoft has reported the correction of a critical vulnerability in Exchange Server detected at the beginning of 2021 and whose exploitation would have allowed threat actors to establish forwarding rules in the affected accounts, which would eventually allow access to incoming emails. Known as ProxyToken and tracked as CVE-2021-33766, the flaw received a score of 6.5/10 according to the Common Vulnerability Scoring System (CVSS).
This flaw was reported by researcher Le Xuan Tuyen, in collaboration with The Zero Day Initiative (ZDI). The expert mentions that the vulnerability is related to the authentication of requests to services within the ecp web application, and could be exploited by sending requests specially designed to evade the authentication process.
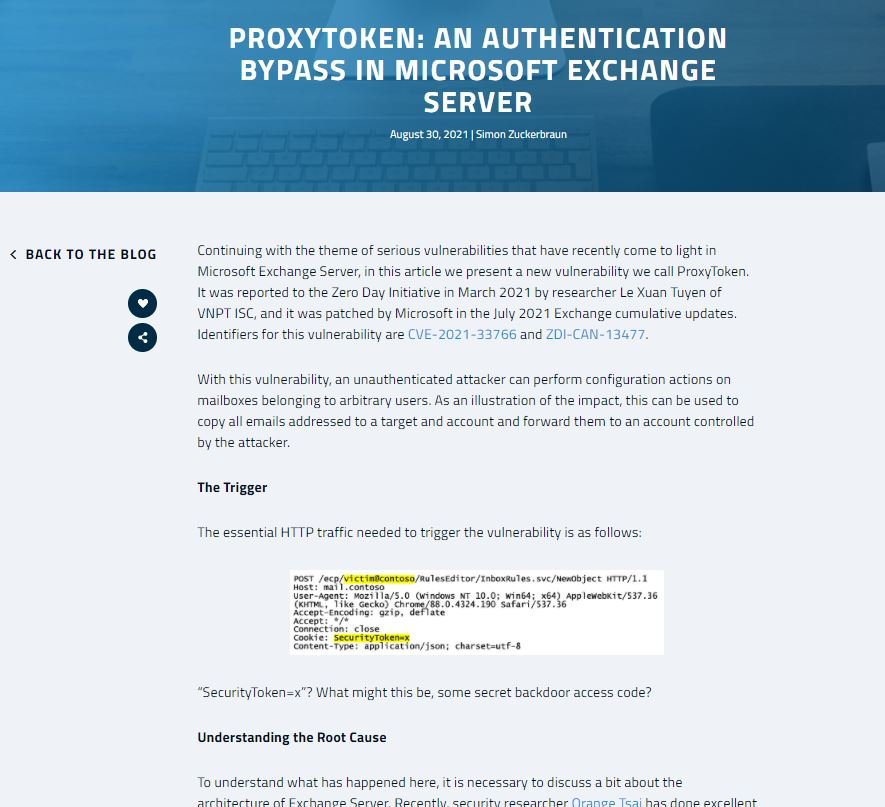
On the other hand, the ZDI report notes that: “Unauthenticated threat actors can perform arbitrary configuration actions on the affected email accounts.” As a result of these malicious actions, it is possible to copy all emails received by the affected user and redirect them to a location controlled by the attackers.
Experts point out that the flaw exists because the sites that Exchange creates in IIS (front-end and back-end) authenticate specific requests when the delegated authentication feature is not enabled and a cookie known as SecurityToken is used.
“When the front-end sees the SecurityToken cookie, it knows that only the back-end is responsible for authenticating this request. Meanwhile, the backend is completely unaware that it needs to authenticate some incoming requests based on the SecurityToken cookie, as DelegatedAuthModule is not loaded on installations that have not been configured to use the special delegated authentication feature,” the ZDI report states.
Threat actors with an account on the same Exchange server as the affected user could abuse the flaw to establish a forwarding rule that allows access to information in the affected inbox. Additionally, if Exchange administrators set a global configuration value to allow the use of forwarding rules to arbitrary Internet targets, the attack will not require authentication on the affected system.
For security, users of vulnerable deployments are encouraged to upgrade Exchange to a secure version.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















