Protecting sensitive organizational credentials, limiting privileged user access, actively imposing security policies, and monitoring and recording privileged user behavior across virtual, cloud, and physical environments are all part of Symantec Privileged Access Management’s (PAM) security breach prevention strategy. A serious security flaw in Symantec Privileged Access Management (PAM) was found by researcher Nikola Kojichas from the cyber security firm RAS-IT. This flaw enables a remote attacker to take control the system with elevated privileges. In order to address non-human actors like software, configuration files, and scripts, the solution offers a privileged credential vault, session recording, threat monitoring, host-based access control for servers, and application-to-application password management.
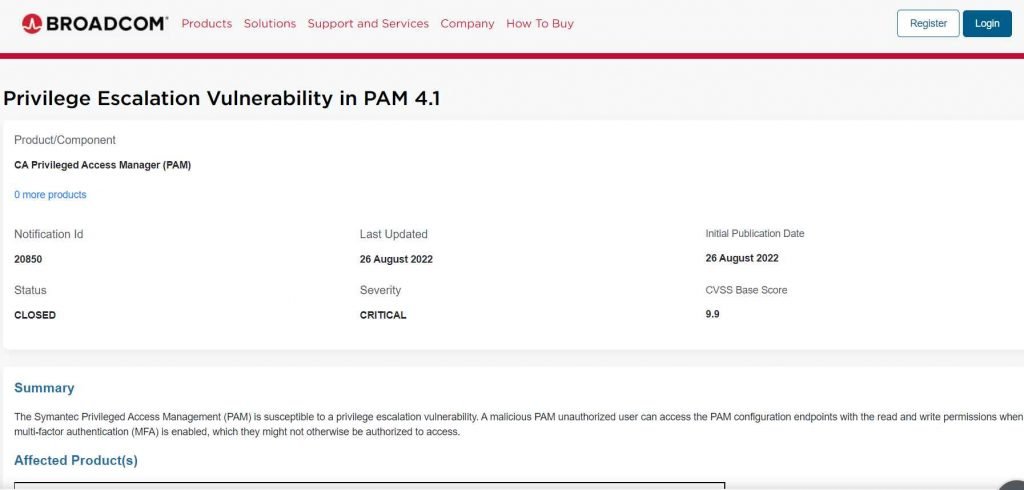
The vulnerability has been given a critical severity level and is tracked as CVE-2022-25625 (CVSS score 9.9). The security alert stated that “when multi-factor authentication (MFA) is enabled, a malicious PAM unauthorized users are able to access the PAM configuration endpoints with the read and write rights, which they may not be permitted to access.”
The CVE-2022-25625 vulnerability might be used by an attacker to escalate their permissions on the vulnerable system by delivering a specially crafted request.
Unsecure version
Privileged Access Management by Symantec 4.1.0
Privileged Access Management by Symantec 4.0.0-4.0.3
Privileged Access Management by Symantec 3.4.0-3.4.6
Secure version
Privileged Access Management by Symantec 4.1.0.10, 4.0.3.01, 4.0.2.04, 4.0.1.19, 4.0.0.05 and 3.4.6.05
Quick fix
Users using Broadcom’s Symantec Privileged Access Management should update to the most recent version.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.