SonicWall security teams launched an emergency alert asking their users to install the released security patches to fix three zero-day flaws in their email security solution. SonicWall ES is a solution designed to protect traffic and email communication, capable of containing any phishing emails and other business email compromise (BEC) attempts.
The risk increases as the company acknowledged that at least one case of active exploitation of these flaws has been detected: “It is urgent that hardware or virtual device administrators install the latest available versions,” the security alert says.
Below are brief descriptions of the reported flaws by SonicWall security teams:
- CVE-2021-20021: A misconfigured endpoint API would allow HTTP requests to be sent to a remote host, leading to unauthorized creation of administrator accounts. The flaw received a score of 9.4/10 according to the Common Vulnerability Scoring System (CVSS)
- CVE-2021-20022: After authentication, a threat actor might upload arbitrary files to a remote host due to a problem with the “branding” functionality. The flaw received a CVSS score of 6.7/10
- CVE-2021-20023: Attackers can also read arbitrary files on a remote host due to “branding” configuration flaws. This vulnerability received a CVSS score of 6.7/10
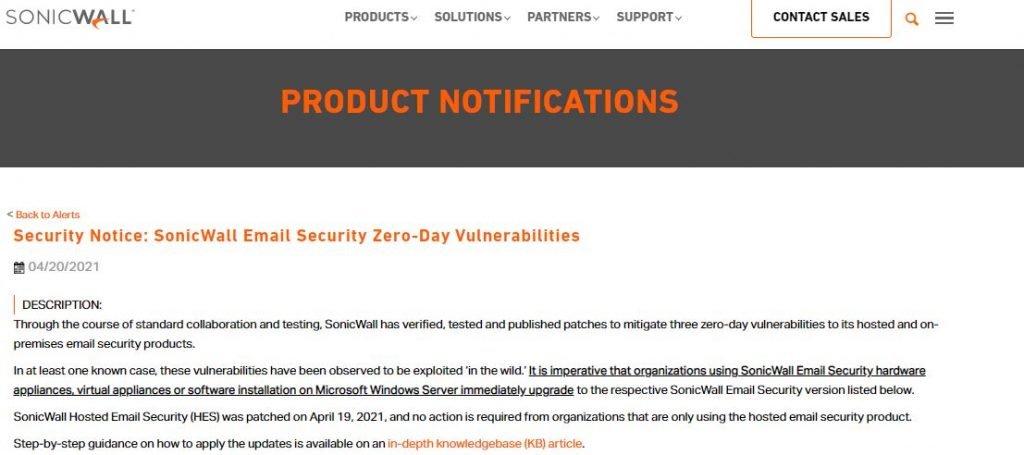
The flaws were discovered by FireEye as part of an investigation of post-exploitation web shell activity in the email security solution, which was identified as the original source of the engagement soon after.
Josh Fleischer, Chris DiGiamo and Alex Pennino, responsible for this investigation, point out that vulnerabilities have already been chained up to gain administrative access and execute code in vulnerable deployments or even install a backdoor for subsequent attacks.
After receiving the reports, SonicWall began working on developing the necessary updates, which were released this week. The company strongly requests customers to install the required updates for their virtual (v10.0.9.6173) and hardware (v10.0.9.6177) deployments to mitigate the risk of exploitation. SonicWall has published a detailed guide to installing these patches on its official platforms.
What are your thoughts about this security issue? Does it put your email platforms under risk? Are you willing to learn more about it? To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.