Technology firm QNAP has asked its users to disable the AFP file service protocol in its network-attached storage (NAS) deployments on a temporary basis while fixing some critical vulnerabilities in Netatalk, which allows *NIX/*BSD systems to act as an AppleShare file server for macOS system users.
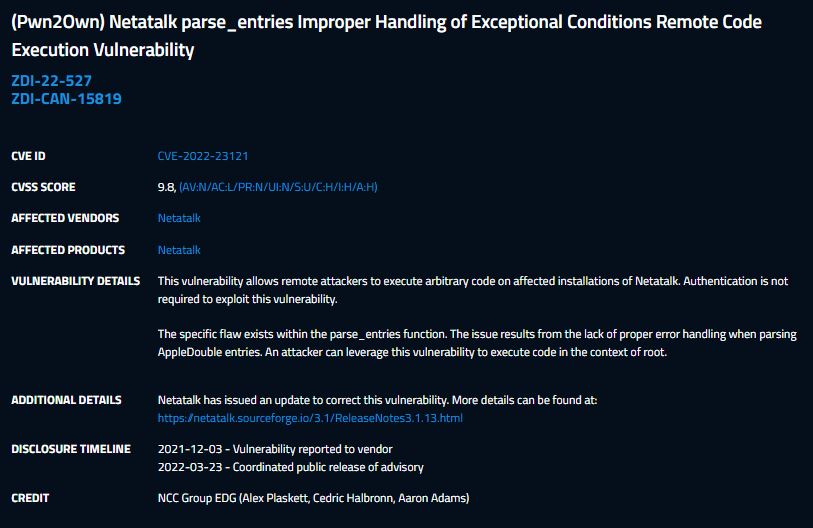
Researchers from NCC Group managed to exploit one of these vulnerabilities, tracked as CVE-2022-23121 and with a score of 9.8/10 according to the Common Vulnerability Scoring System (CVSS). This flaw was exploited on a Western Digital PR4100 NAS device, which runs the My Cloud OS firmware.
QNAP reported detection of three other vulnerabilities, tracked as CVE-2022-23125, CVE-2022-23122, CVE-2022-0194 and which also received CVSS scores of 9.8/10. Exploiting these flaws would allow threat actors to execute arbitrary code remotely.
On March 22, the Netatalk development team released version 3.1.13 to fix these security flaws, three months after the flaws were exploited at the Pwn2Own ethical hacking event. QNAP says the Netatalk vulnerabilities affect the following operating system versions:
- QTS 5.0.x and later
- QTS 4.5.4 and later
- QTS 4.3.6 and later
- QTS 4.3.4 and later
- QTS 4.3.3 and later
- QTS 4.2.6 and later
- QuTS hero h5.0.x and later
- QuTS hero h4.5.4 and later
- QuTScloud c5.0.x
“QNAP is thoroughly investigating the case. We will release security updates for all affected QNAP operating system versions and provide more information as soon as possible.” As mentioned above, QNAP recommends disabling AFP to mitigate exploitation risk. To apply this security measure, you will need to go to Control Panel > Network Services and > Win/Mac/NFS/WebDAV > Apple Networks and select Disable AFP (Apple File Protocol).
In addition to fixing these flaws, QNAP is working to address a Linux vulnerability called ‘Dirty Pipe’ actively exploited in attacks that allows root privileges to be obtained and a high-severity OpenSSL bug that can lead to denial-of-service (DoS) states.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















