 Short Bytes: There has been an increase in the number of DDoS attacks on educational institutes. These attacks are a realization of students’ intentions to change their grades or cause harm to the school network. They are using the dark web to perform such attacks.
Short Bytes: There has been an increase in the number of DDoS attacks on educational institutes. These attacks are a realization of students’ intentions to change their grades or cause harm to the school network. They are using the dark web to perform such attacks.
So, what sort of illegal activity a student would like to perform?
Apart from purchasing drugs, one of the many ambitions of every student is getting good grades and attendance. Some work hard to achieve it while for some, grades are just a few clicks away. That’s where the dark web comes in the picture. All they have to do is pay some bitcoins to websites like PirateCrackers on the dark web and they’ll hack the school website for them, change their grades, increase their attendance and much more.
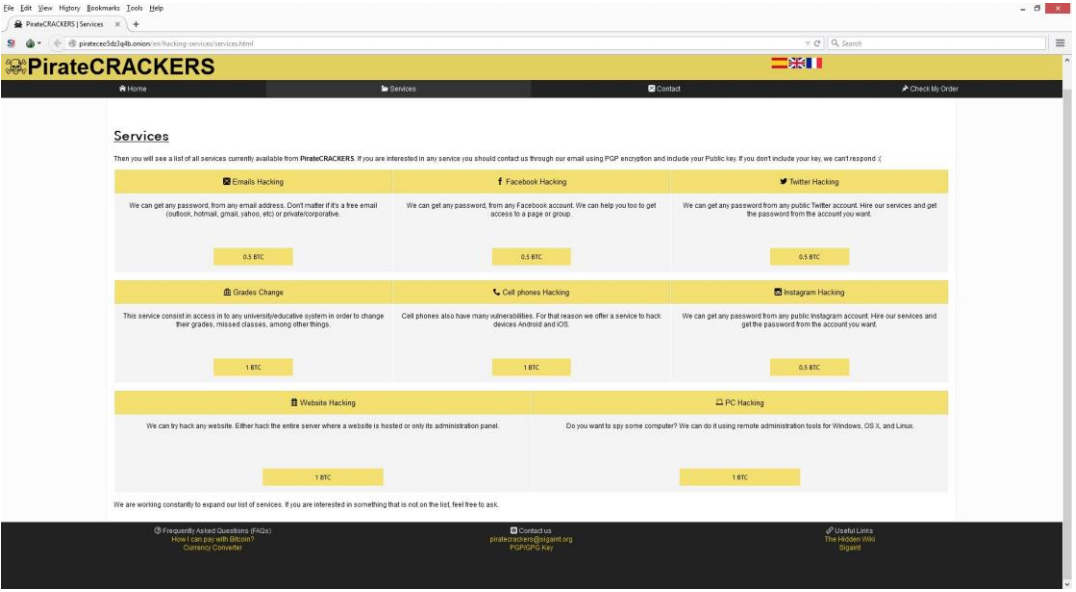
For some frustrated students, and maybe staff members, a perfect solution to unleash vengeance on the school is DDoS attack or Distributed Denial of Service attack. A student doesn’t have to be pro hacker to harm his school network, there are plenty of them for hire on the dark web. The frequency of DDoS attacks educational institutions is increasing.
Sometimes, it not about the grades. Last year, a Japanese 15-year old student performed a cyber attack, reported in May 2016, taking down the websites of 444 schools. He wanted to show the teachers, how incompetent they were.
“I hate how the teachers talk down to us and never let us express ourselves. So, I thought I would remind them of their own incompetence. It felt good to see them have problems. I did it several times,” — the student told the police after being arrested.
“In the new digital era, students are looking to cheat the system just like those of the past. The only difference is they’re using computers now and run the risk of facing lengthy charges if caught,” — said Daniel Smith, a security researcher at Radware.
The commonly implemented modus operandi for such attacks are UDP flooding, SQL injection and reflection attacks like DNS flooding. “The operators behind these services are just like any other vendor in existence and engage marketing. They advertise their services via stunt hacking, social media post, forums and private offering,” – Smith said.
If you have something to add, tell us in the comments below.
Also Read: Arbor Networks Report: Largest DDoS Attack Of 579Gbps In The First Half Of 2016









